
OpenTofu has emerged as the true open successor to Terraform, restoring transparency and community ownership after Terraform’s shift to a restrictive BSL license. With features like OCI registries, encryption at rest, and a public RFC process, it’s already outpacing Terraform’s innovation. Early adopters not only gain cutting-edge IaC capabilities but also a voice in shaping its future—and with Harness IaCM’s native OpenTofu support, migrating and scaling securely has never been easier.
Are you still using Terraform without realizing the party has already moved on?
For years, Terraform was the default language of Infrastructure as Code (IaC). It offered predictability, community, and portability across cloud providers. But then, the music stopped. In 2023, HashiCorp changed Terraform’s license from Mozilla Public License (MPL) to the Business Source License (BSL), a move that put guardrails around what users and competitors could do with the code.
That shift opened a door for something new and truly open.
That “something” is OpenTofu.
And if you’re not already using or contributing to it, you’re missing your chance to help shape the future of infrastructure automation.
The fork that changed IaC forever
OpenTofu didn’t just appear out of thin air. It was born from community demand, a collective realization that Terraform’s BSL license could limit the open innovation that made IaC thrive in the first place.
So OpenTofu forked from Terraform’s last open source MPL version and joined the Linux Foundation, ensuring that it would remain fully open, community-governed, and vendor-neutral. A true Terraform alternative.
Unlike Terraform’s now-centralized governance, OpenTofu’s roadmap is decided by contributors, people building real infrastructure at real companies, not by a single commercial entity.
That means if you depend on IaC tools to build and scale your environments, your voice actually matters here.
Why OpenTofu is gaining momentum
OpenTofu is not a “different tool.” It’s a continuation, the same HCL syntax, same workflows, and same mental model, but under open governance and a faster, community-driven release cadence.
Let’s break down the Terraform vs OpenTofu comparison:
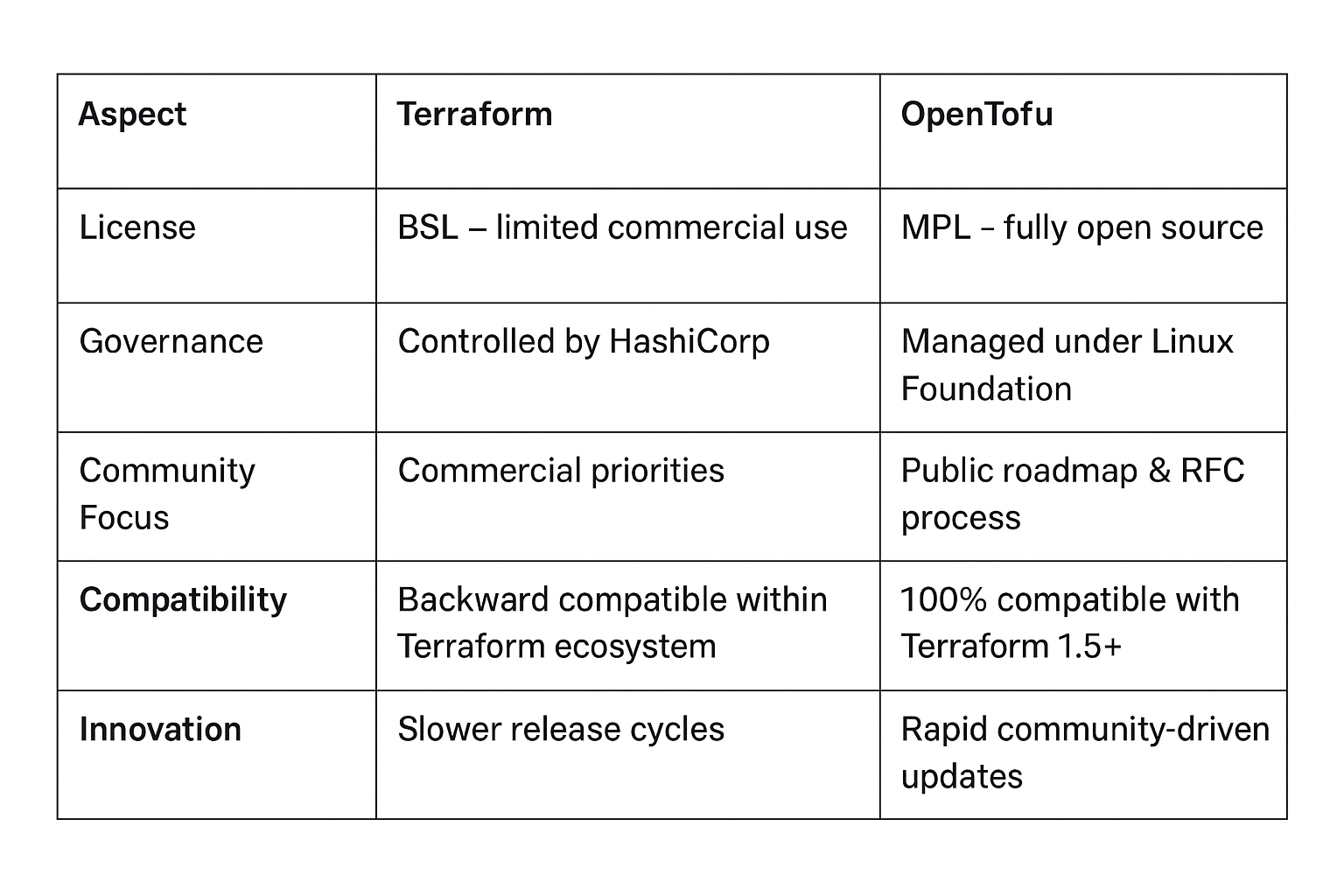
It’s still Terraform-compatible. You can take your existing configurations and run them with OpenTofu today. But beyond compatibility, OpenTofu is already moving faster and more freely, prioritizing developer-requested features that a commercial model might not. Some key examples of it's true power and longevity include:
1. Standardized distribution with OCI registries
Packaging and sharing modules or providers privately has always been clunky. You either ran your own registry or relied on Terraform Cloud.
OpenTofu solves this with OCI Registries, i.e. using the same open container standard that Docker uses.
It’s clean, familiar, and scalable.
Your modules live in any OCI-compatible registry (Harbor, Artifactory, ECR, GCR, etc.), complete with built-in versioning, integrity checks, and discoverability. No proprietary backend required.
For organizations managing hundreds of modules or providers, this is a big deal. It means your IaC supply chain can be secured and audited with the same standards you already use for container images.
2. True security with encryption at rest
Secrets in your Terraform state have always been a headache.
Even with remote backends, you’re still left with the risk of plaintext credentials or keys living inside the state file.
OpenTofu is the only IaC framework with built-in encryption at rest.
You can define an encryption block directly in configuration:
This encrypts the state transparently, no custom wrapper scripts or external encryption logic.
It also supports multiple key providers (AWS KMS, GCP KMS, Azure Key Vault, and more).
Coming soon in OpenTofu 1.11 (beta): ephemeral resources.
This feature lets providers mark sensitive data as transient so it never touches your state file in the first place. That’s a security level no other mainstream IaC tool currently offers.
3. A community-driven future
OpenTofu’s most powerful feature isn’t in its code, it’s in its process.
Every proposal goes through a public RFC. Every contributor has a say. Every decision is archived and transparent.
If you want a feature, you can write a proposal, gather community feedback, and influence the outcome.
Contrast that with traditional vendor-driven roadmaps, where features are often prioritized by product-market fit rather than user need.
That’s what “being late to the party” really means: you miss your seat at the table where the next decade of IaC innovation is being decided.
Why you don’t want to miss this party
Being early in an open-source ecosystem isn’t about bragging rights, it’s about influence.
OpenTofu is already gaining serious traction:
- Major cloud providers and IaC platforms are integrating it.
- Contributors from across the industry are shaping releases.
- Security and compliance enhancements (like encryption and OCI support) are coming faster than ever.
If you join later, you’ll still get the code. But you won’t get the same opportunity to shape it.
The longer you wait, the more you’ll be reacting to other people’s decisions instead of helping make them.
Ready to switch? The OpenTofu migration path is smooth.
Migrating is a one-liner!
The OpenTofu migration guide shows that most users can simply install the tofu CLI and reuse their existing Terraform files:
It’s the same commands, same workflow, but under an open license. You can even use your existing Terraform state files directly; no conversion step required.
For teams already managing infrastructure at scale, the move to OpenTofu doesn’t just preserve your workflow, it future-proofs it.
How Harness IaCM supports OpenTofu
When you’re ready to bring OpenTofu into a managed, collaborative environment, Harness Infrastructure as Code Management (IaCM) has you covered.
Harness IaCM natively supports both Terraform and OpenTofu. You can create a workspace, select your preferred binary, and run init, plan, and apply pipelines without changing your configurations.
That means you can:
- Experiment safely with OpenTofu while retaining version control.
- Store and share modules through a managed environment.
- Adopt OpenTofu’s features (like encryption and OCI) inside CI/CD pipelines.
- Gradually migrate Terraform workspaces without breaking production.
Harness essentially gives you the sandbox to explore OpenTofu’s potential, whether you’re testing ephemeral resource behavior or building private OCI registries for module distribution.
So while the OpenTofu community defines the standards, Harness ensures you can implement them securely and at scale.
Contribute, don’t just consume
The real magic of OpenTofu lies in participation.
If you’ve ever complained about Terraform limitations, this is your moment to shape the alternative.
You can:
- Test new features.
- Submit issues or RFCs.
- Contribute code or docs.
- Influence what the next release includes.
Everything lives in the open on the OpenTofu Repository.
Even reading a few discussions there shows how open, constructive, and fast-moving the community is.
Final thoughts
The IaC landscape is changing, and this time, the direction isn’t being set by a vendor, but by the community.
OpenTofu brings us back to the roots of open-source infrastructure: collaboration, transparency, and freedom to innovate.
It’s more than a fork, it’s a course correction.
If you’re still watching from the sidelines, remember: the earlier you join, the more your voice matters.
The OpenTofu party is already in full swing.
Grab your seat at the table, bring your ideas, and help build the future of IaC, before someone else decides it for you.
