Infrastructure as Code Management
Orchestrate and Govern IaC Workflows with AI
The Practical Guide to Modernizing Infrastructure Delivery
In today’s AI-native landscape, siloed workflows and manual steps still slow infrastructure delivery. This guide outlines a unified, automated framework that platform teams can use to deliver and orchestrate secure, governed and scalable infrastructure.

Collaborate, Standardize, and Scale Infrastructure
Harness IaCM is a unified and trusted platform for DevOps teams, platform engineers, and cloud engineers to manage Terraform, OpenTofu, and other IaC tools with consistent, repeatable, compliant workflows.
Self-Service IaC for DevOps Teams & Platform Engineers
Improve collaboration by allowing teams to manage and reuse shared modules and templates, reducing conflicts, improving visibility, and simplifying the review process.
Accelerate the adoption of Infrastructure as Code by making it easier for teams to work with approved infrastructure components.
Reduce time to market by decreasing manual steps and deployment cycle times.
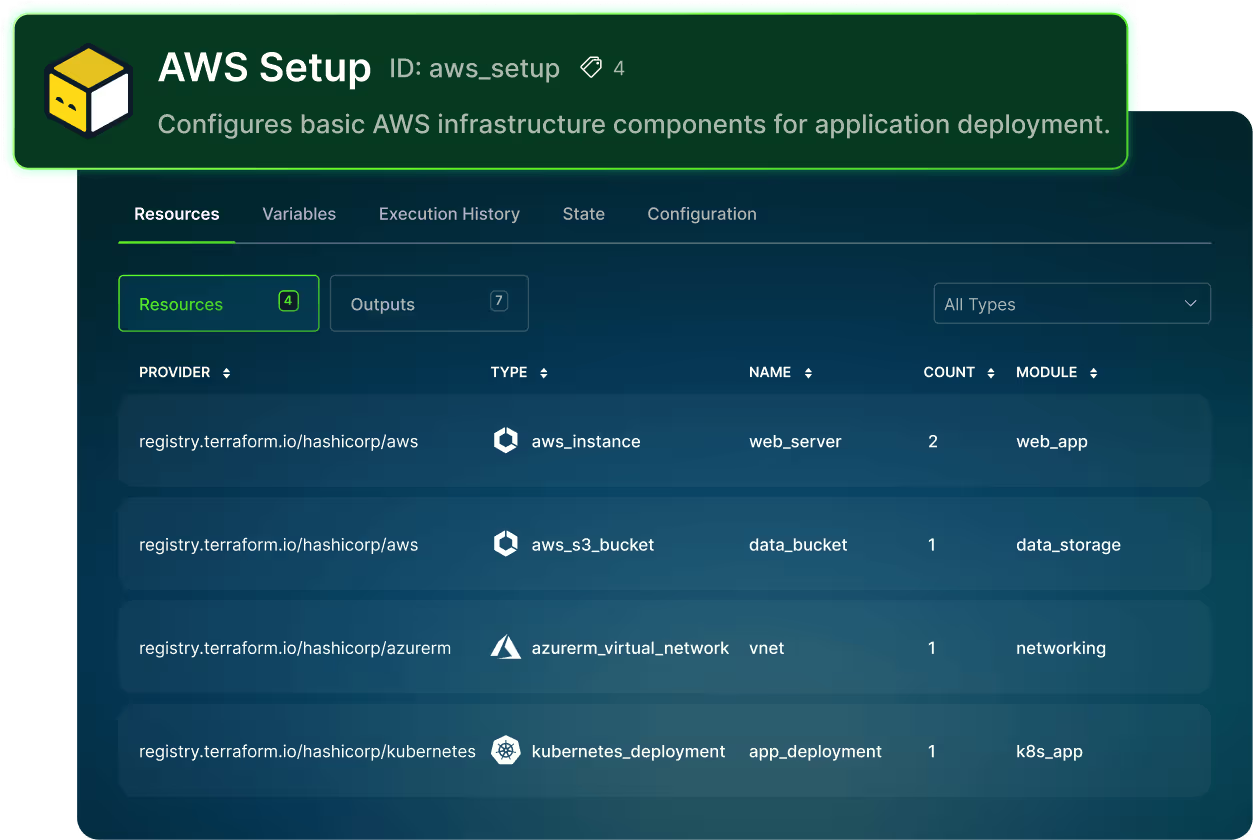
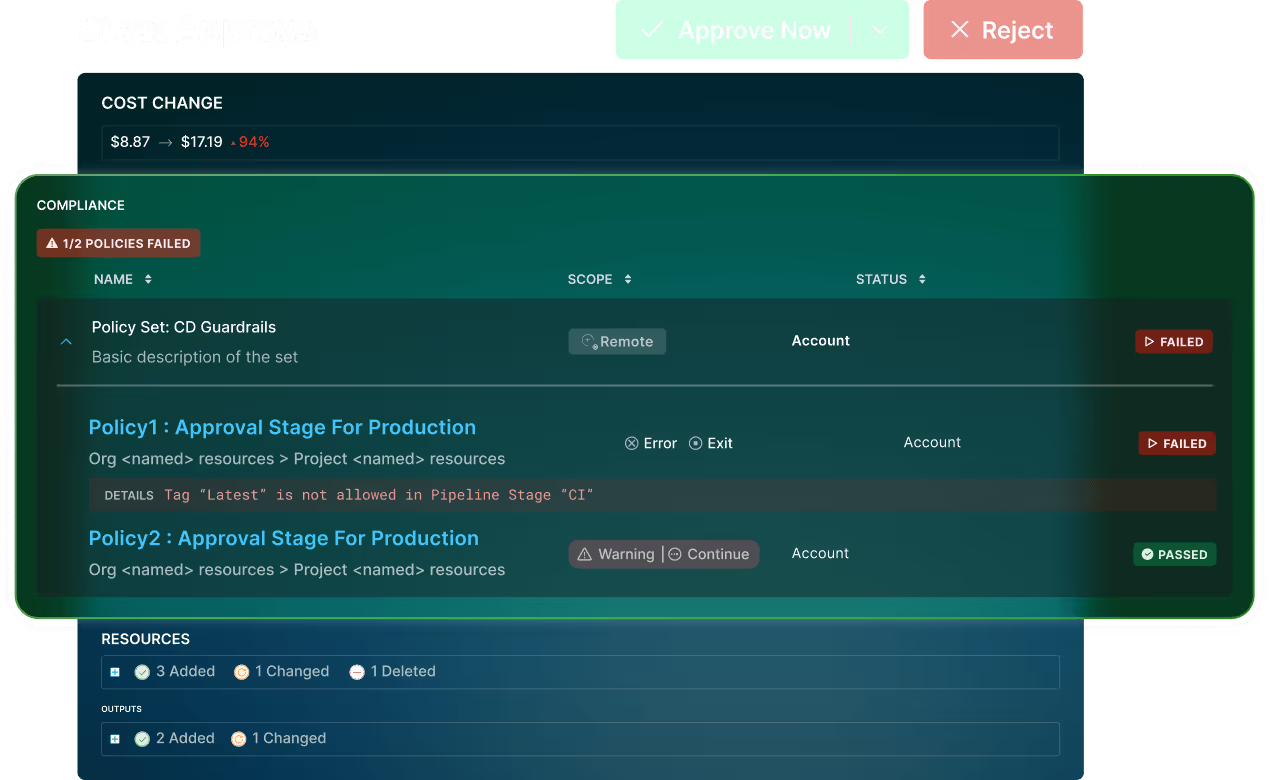
Centralize Control and Governance
Reduce errors by removing manual processes and automating infrastructure workflows.
Detect issues earlier in the design process through integrated checks and automated validations.
Maintain full control with governance policies that prevent security breaches and keep infrastructure environments safe and compliant.
Shared pipelines for infrastructure changes
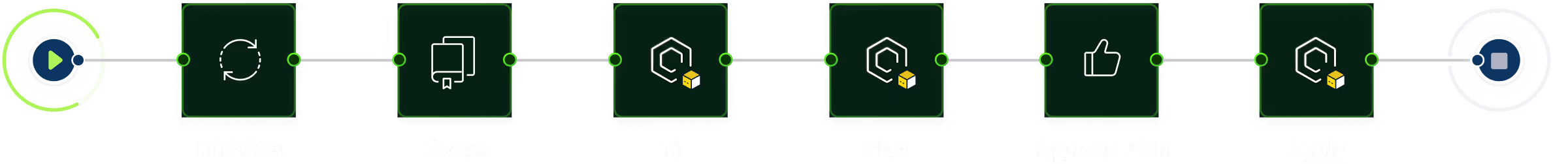
Harness Infrastructure as Code management offers a dedicated CI/CD solution for fully automating deployments of Terraform scripts, OpenTofu scripts, and other IaC tools to accelerate DevOps teams and platform engineering workflows.
Seamlessly integrates Infrastructure as Code management into Harness pipelines for automated provisioning and updates across environments.
Drive consistency with workspace templates, variable sets, and centrally managed modules and providers registries, standardizing workflows across Terraform, OpenTofu, and other IaC tools.
Control and Optimize Infrastructure Costs
Gain full visibility into resource ownership, usage, changes, and associated costs across environments.
Preview resource changes before they are applied to make proactive, informed cost decisions.
Enforce policies to prevent unexpected cost spikes and ensure teams stay within budget.
Customer Success Stories
Frequently Asked Questions
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) is the practice of provisioning, managing, and orchestrating infrastructure using code instead of manual processes. It treats infrastructure like software—version-controlled, testable, repeatable, and automated. Using declarative configuration files stored in Git, teams gain end-to-end visibility, GitOps workflows, and the ability to consistently recreate environments across clouds and regions. IaC enables idempotency, ensures configurations are reproducible, and streamlines collaboration across DevOps, platform engineering, and SRE teams.

What is configuration drift and how does IaC address it?
Configuration drift occurs when the live infrastructure state no longer matches the desired state defined in code usually due to ad-hoc manual changes, inconsistent updates, or unmanaged cloud resources. IaC solves this through automated drift detection, continuous state monitoring, and reconciliation back to the version-controlled configuration. By using Git as the single source of truth, IaC tools enforce policy-as-code guardrails, prevent unauthorized changes, and ensure production stays aligned with the intended, declarative configuration.

What are the benefits of using IaC?
IaC improves speed, consistency, and scalability by automating infrastructure provisioning through reusable modules, templates, and stacks. It reduces human error, supports immutable infrastructure practices, and enables CI/CD-driven workflows for infrastructure changes. With built-in policy-as-code, compliance, and granular guardrails, IaC enhances security posture and reduces operational risk. Teams gain auditability, version control, repeatability, and the ability to roll back or promote changes across environments with confidence.

What's the difference between declarative and imperative IaC?
Declarative IaC describes what the desired end state should be, allowing the IaC engine to automatically determine the steps needed to achieve that state. Imperative IaC specifies how to build or update infrastructure by defining the exact sequence of operations. Declarative IaC is common in tools like Terraform, OpenTofu, Pulumi (in declarative mode), and CloudFormation, while imperative approaches resemble scripting and procedural automation.

What tools are commonly used for IaC?
Popular IaC tools include OpenTofu, Terraform, Pulumi, AWS CloudFormation, Azure Resource Manager (ARM), Google Cloud Deployment Manager, Kubernetes manifest-based GitOps tooling, and configuration/provisioning tools like Ansible. Harness IaCM layer workflow automation, Policy as Code, drift detection, compliance enforcement, and orchestration on top of these IaC frameworks.

Why do teams use IaCM on top of IaC tools?
Teams use IaCM to create and orchestrate consistent workflows, improve governance, and standardize how infrastructure changes move through development, staging, and production. IaCM centralizes state management, secrets, variable sets, and policy controls, making it easier to implement best practices and avoid manual errors.

How does IaCM support GitOps for infrastructure?
IaCM enables GitOps for infrastructure by ensuring that every infrastructure change starts with a pull request, moves through automated checks and approvals, and is applied consistently across environments. This aligns application delivery and infrastructure provisioning under the same version controlled workflow.

What is the role of Policy as Code in IaC and IaCM?
Policy as Code allows organizations to define rules for security, compliance, resource usage, and cost optimization in a machine readable format. These policies are applied automatically during IaC workflows to ensure all cloud resources meet required standards. Policy as Code improves governance, reduces risk, and keeps infrastructure deployments consistent.

.svg)


