AI speeds delivery but expands risk. Teams need context, verification, behavior detection, and learning to stay secure by default.
Software delivery has been accelerating for more than a decade, and the arrival of AI has pushed us into an entirely new velocity class. Code generation, configuration scaffolding, infrastructure suggestions, remediation hints, and deployment decisions now involve AI. It participates in every stage of the delivery pipeline.
On the surface, this feels like progress. Faster delivery, fewer bottlenecks, happier teams.
But a closer look reveals something more complicated.
The Gap Between Speed and Safety
Most modern pipelines were designed for a world where humans made the important decisions: writing code, reviewing changes, crafting configurations, and evaluating risks. AI changed that dynamic. It introduced automation that moves faster than traditional security practices can respond to.
The result is a widening gap between how fast we can ship and how safely we can ship.
Here are a few of the challenges teams are already feeling today.
1. AI Is Amplifying Existing Weaknesses
If your base images are outdated, your tests barely cover your codebase, or your deployment strategy lacks guardrails, AI does not fix these issues. It accelerates them. Pipelines automate mistakes just as quickly as they automate features.
2. The Threat Surface Has Shifted
The most common AI failures today are not the classic vulnerabilities we have spent years scanning for. Instead, organizations are facing challenges such as:
- prompt injection
- model jailbreaking
- vulnerable AI generated code
- behavior driven exploits
- configuration drift caused by AI tools
These threats target behavior and reasoning, not code lines.
3. Delivery Is Faster but Security Has Not Kept Up
AI assisted workflows generate code, configurations, and infrastructure definitions at machine speed. Meanwhile, security still relies heavily on:
- manual reviews
- point in time scans
- human approval gates
This mismatch means misconfigurations are no longer human scale accidents. They have become automated hazards.
4. Developers Are Not Set Up for AI Era Security
Developers are expected to recognize model manipulation, unsafe AI output, reasoning drift, and subtle behavioral failures. But most have very little or no training in AI security.
The expectation does not match the support we give them.
These challenges are already shaping the next era of DevSecOps.
And they set the stage for a new approach that I introduced at DevSecOps 2025.
A Framework for Secure by Default AI Delivery
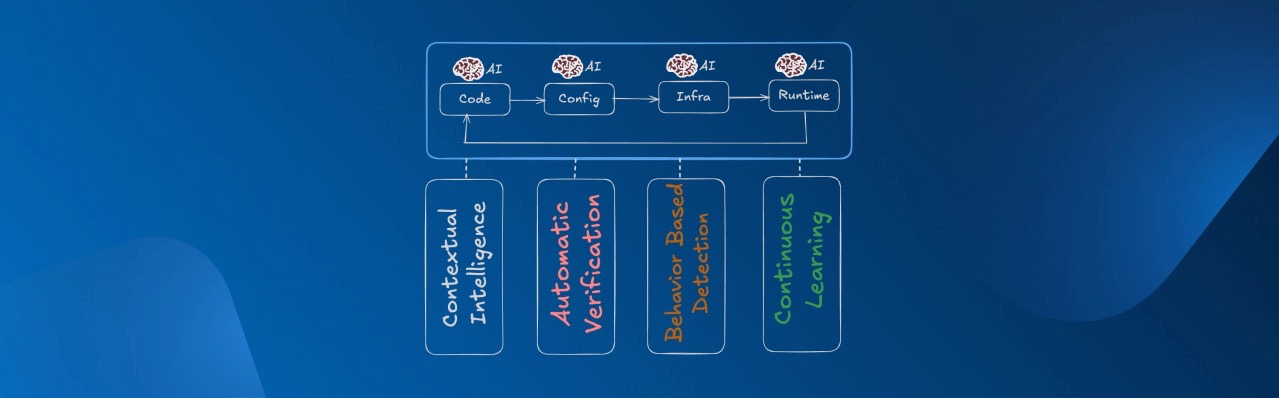
During my keynote at DevSecOps 2025, I introduced a practical four pillar framework designed for AI native delivery environments. This framework brings security and intelligence directly into the workflow, instead of adding more checks at the edges.

Here is a summary of the four pillars I presented.
Pillar 1: Contextual Intelligence
Pipelines need to understand what changed, why it changed, and how that change affects code, configuration, infrastructure, and runtime behavior.
Context is the foundation that allows everything else to work.
Pillar 2: Automatic Verification
Every artifact, configuration, model output, and pipeline step should be automatically verified for origin, trust, integrity, and consistency with the source of truth before deployment.
Pillar 3: Behavior Based Anomaly Detection
AI systems fail in behavioral ways, not just structural ones. Pipelines need the ability to detect deviations, drift, suspicious patterns, and unsafe outputs in real time.
Pillar 4: Continuous Learning Loops
Delivery systems must improve with every deployment and every incident.
This means using real pipeline data to strengthen guardrails, adapt verification rules, and continuously refine what “safe” looks like.
These four pillars work together to create delivery systems that remain secure and trustworthy even as AI accelerates everything around them.
If you want to learn more about how these pillars can be applied in real pipelines and how they support secure by default DevSecOps, you can access the recording of my keynote from DevSecOps 2025.
