Automatically discover and catalog APIs and sensitive data flows
Find API vulnerabilities with continuous scanning and contextualized remediation
Protect your APIs and defend against evolving threats
Stop automated attacks that target your applications and business logic
Protect your web applications with cloud-scale, API-centric security.

Web Application & API Protection
Gain API visibility and protect your applications at the speed of modern delivery, matched to your architectures.
API Security Foundations
Harness WAAP by Traceable provides full visibility and control of modern applications and their data flows.

API Testing
Find API vulnerabilities with continuous scanning and contextualized remediation.
See more detailBot & Abuse Protection
Stop automated attacks that target your applications and business logic.
See more detailWeb Application Firewall
Protect your web applications with cloud-scale, API-centric security.
See more detail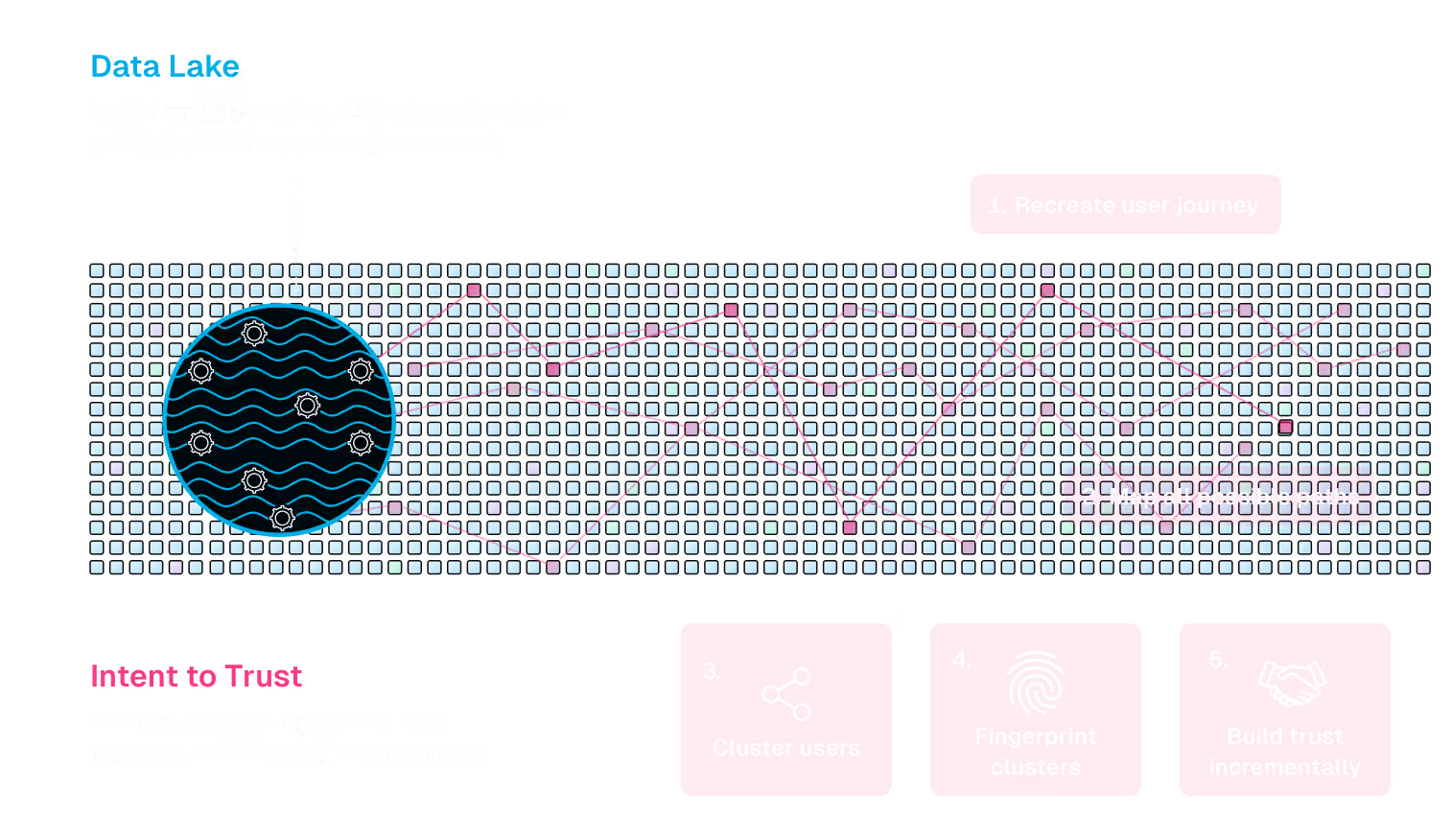
Untangle User Intent
Application Threat Intelligence
Gain deep application insight and API threat intelligence where other tools overwhelm you with network traffic that's blind to business context.
Tuned for Your Architecture
Tune configuration for your unique environments so you can stop more than just broad categories of CVEs and OWASP Top 10 Risks.
Detect with Full Fidelity
Harness is powered by a data lake built for application-layer context. Uncover usage patterns based on complete application signals, not just network traffic, metadata, or samples.
Infuse IR with Application Signals
Provide Fraud and SecOps teams with application context and minimize wasted cycles sifting through incomplete logs.
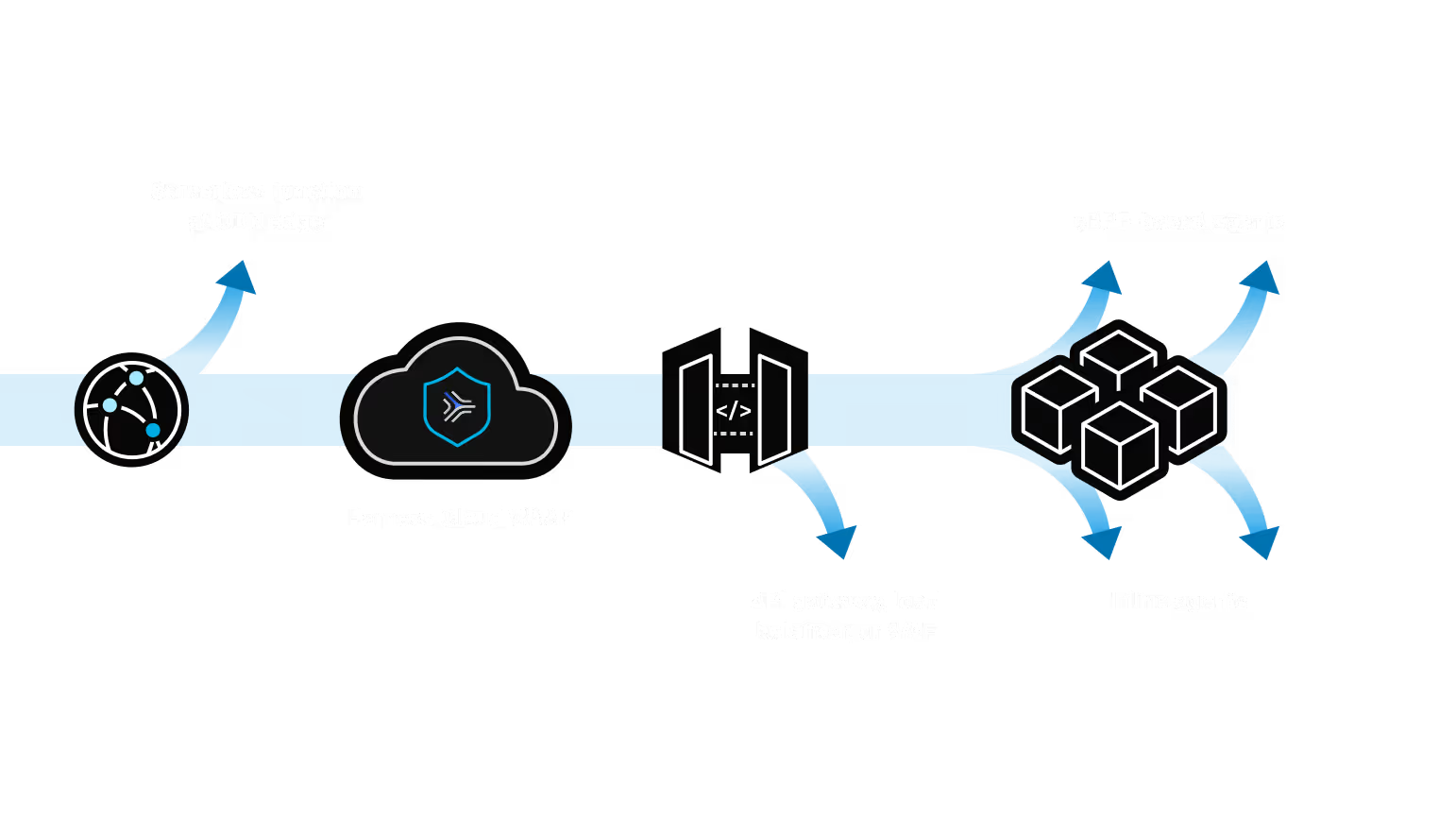
Quickstart with Edge & Scale As Needed
Agentless Edge
Route traffic securely via DNS or deploy behind a CDN for agentless protection.
In-line Instrumentation
Deploy directly in API gateways, proxies, and load balancers, or inside applications using lightweight language agents.
Out-of-Band Collection
Mirror traffic from existing network elements, or use eBPF to maintain visibility without code changes.
AI-Power Your Runtime Security
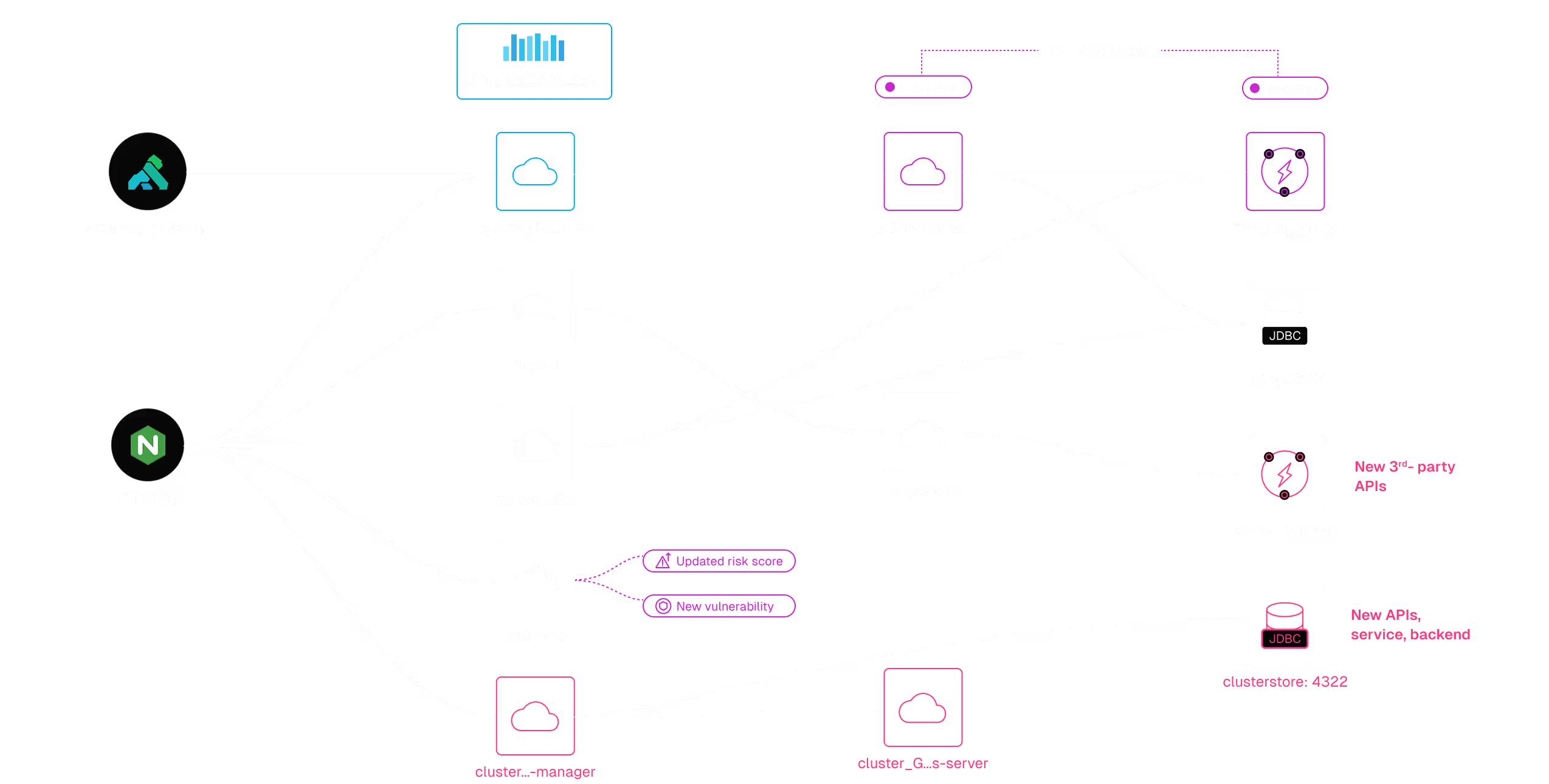
Contextualized Signals
Analysis is based on your application configurations, not just predefined rules. Using AI/ML to parse application and API telemetry is in our DNA.
Simplify Complex Designs
Simplify usage patterns and API call chains along with explanations of controls needed to secure your attack surface.
Machine-Speed SecOps
AI-assisted policy creation and maintenance so you can protect your applications and business logic as they evolve.
Harness Customers Reduce Risk
at Enterprise Scale
3T+
App and API calls protected per month
90K
API scans run daily to detect vulnerabilities
700K+
APIs monitored across our customer base
107K+
App and API attacks blocked per month
Frequently Asked Questions
What is WAAP (Web Application and API Protection)?
WAAP is a platform-oriented, application runtime security approach that combines web application firewall (WAF), API discovery, API testing, API protection, and bot & abuse protection to defend web applications and APIs from modern attacks.

How is WAAP different from traditional WAF?
Traditional web application firewall (WAF) focuses primarily on web application attacks that occur through web protocols (HTTP/HTTPS), web UI interactions, and client-side JavaScript interactions with backend systems. If you expose APIs, run microservices, or see automated abuse, a WAAP platform adds API security controls and bot protection that most legacy WAF products don’t cover well.

How does WAAP protect APIs specifically?
WAAP platforms extend coverage to APIs with continuous API discovery, sensitive data flow analysis, continous vulnerability checking, API threat protection, and bot & abuse mitigation within a unified platform so you can detect and protect against application as well as API attacks.

What threats does WAAP protect against?
WAAP platforms help prevent SQL injection (SQLi), cross-site scripting (XSS), bruteforcing, credential stuffing, account takeover (ATO), business logic abuse, transaction fraud, bot attacks, and application-layer denial-of-service (DoS) attacks targeting web applications and APIs.

Can WAAP help prevent the OWASP API Security Top 10 risks?
Yes, WAAP platforms typically address OWASP API Security Top 10 risks with a combination of authentication and authorization checks, sensitive data flow analysis, threat detection, rate limiting, anomaly detection, and abuse protection. Risks also extend to unsafe third-party API consumption and API inventory management, which require a WAAP platform that offers continuous API discovery and data flow analysis across environments.

Does WAAP include bot management?
Most WAAP platforms include capabilities to detect and block malicious automation, or bots, like web scraping, credential stuffing, and transaction fraud, while allowing good forms of automation such as agentic AI and robotic process automation (RPA).

Is WAAP cloud-based, on-prem, or both?
WAAP platforms may deploy as cloud services (SaaS) or integration with a content delivery networks (CDN) at the edge. Stronger WAAP platforms provide multiple deployment options that support hybrid- and multi-cloud strategies, so you can protect web applications and APIs across environment types. This includes in-line deployment options like API gateway integration, sidecar containers, and instrumentation agents (e.g., eBPF) as well as other out-of-bound options like traffic mirroring.

Does WAAP work with Kubernetes and microservices?
Yes, some WAAP solutions work with Kubernetes by integrating with ingress controllers, deploying as sidecar containers in clusters, or instrumenting application workloads (e.g., eBPF) to provide additional layers of application and API protection for microservices traffic, sometimes referred to as inner-service or east/west (E/W) traffic.

How do WAAP platforms handle HTTPS/TLS encryption?
WAAP platforms typically inspect HTTPS traffic via TLS termination at the edge or proxies in different points of a system architecture. TLS termination enables application and API threat detection without sacrificing secure transport. WAAP platforms may also instrument application workloads directly (e.g., eBPF) before any transport encryption is in effect.

Can WAAP replace an API gateway?
WAAP platforms do not replace an API gateway’s access control enforcement, intelligent routing, rate/use limiting, versioning, and lifecycle management commonly seen in API management platforms. However, WAAP complements API gateways and API management with dedicated API discovery, API threat protection, and bot & abuse protection.

.svg)