
Application Security Testing
Keep up with your developers using pipeline-native security that goes from the first line of code to production and scales across every pipeline.
Our Products
Scan every part of your application - from first-party code to open source packages and even your CI/CD toolchain - for vulnerabilities and other security issues natively in your pipelines with application security testing from Harness.
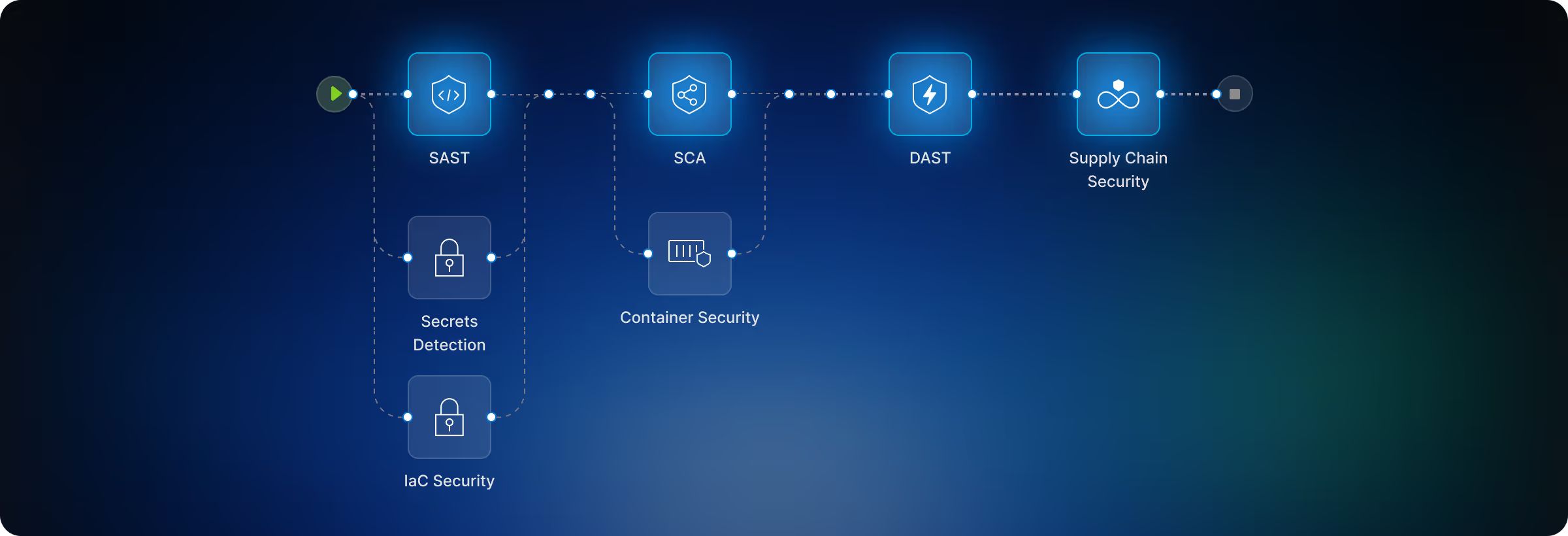
SAST
Scan code for vulnerabilities with low FP, pipeline speed, and no tuning required

Supply Chain Security
Open source security, CI/CD security, artifact security, SLSA, and more

Security Testing Orchestration
Manage AppSec posture across every vendor + scanner in your pipelines

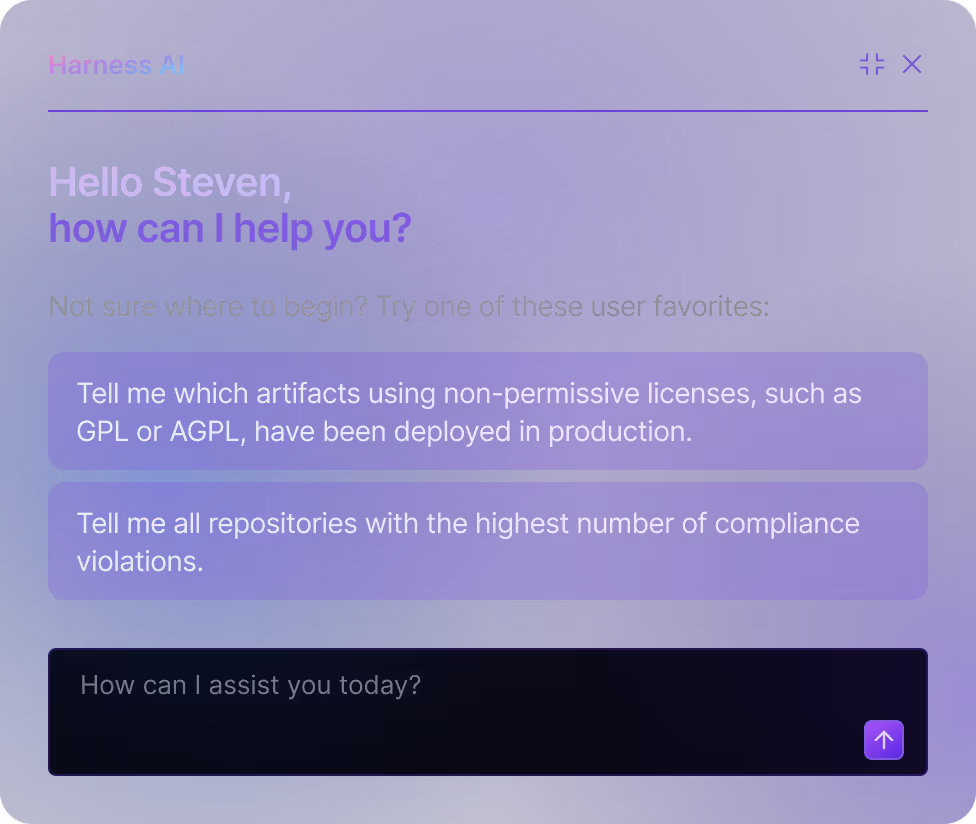
AI-First Security
Harness AI for Security
Make security easier - simplify security tasks, understand your security findings, create complex security policies, and more.
Test AI-Native Applications
Dynamically test applications for evolving AI-specific threats, such as the OWASP Top 10 risks for LLM applications.
AI-Powered Remediation
Help developers remediate vulnerabilities faster with AI-provided and validated fixes - both in the IDE and Pull Request
Easy to Deploy
Customizable Stages & Steps
Easily configure security scans in the same way as any other stage or step in your Harness pipeline.
1-Click Scanning
Deploy Harness SAST, SCA, container security, secrets detection, and IaC security faster and as easily as a single click.
Scalable Pipeline Templates
Standardize on a pre-approved set of security controls and easily scale deployment to 1000s of pipelines.
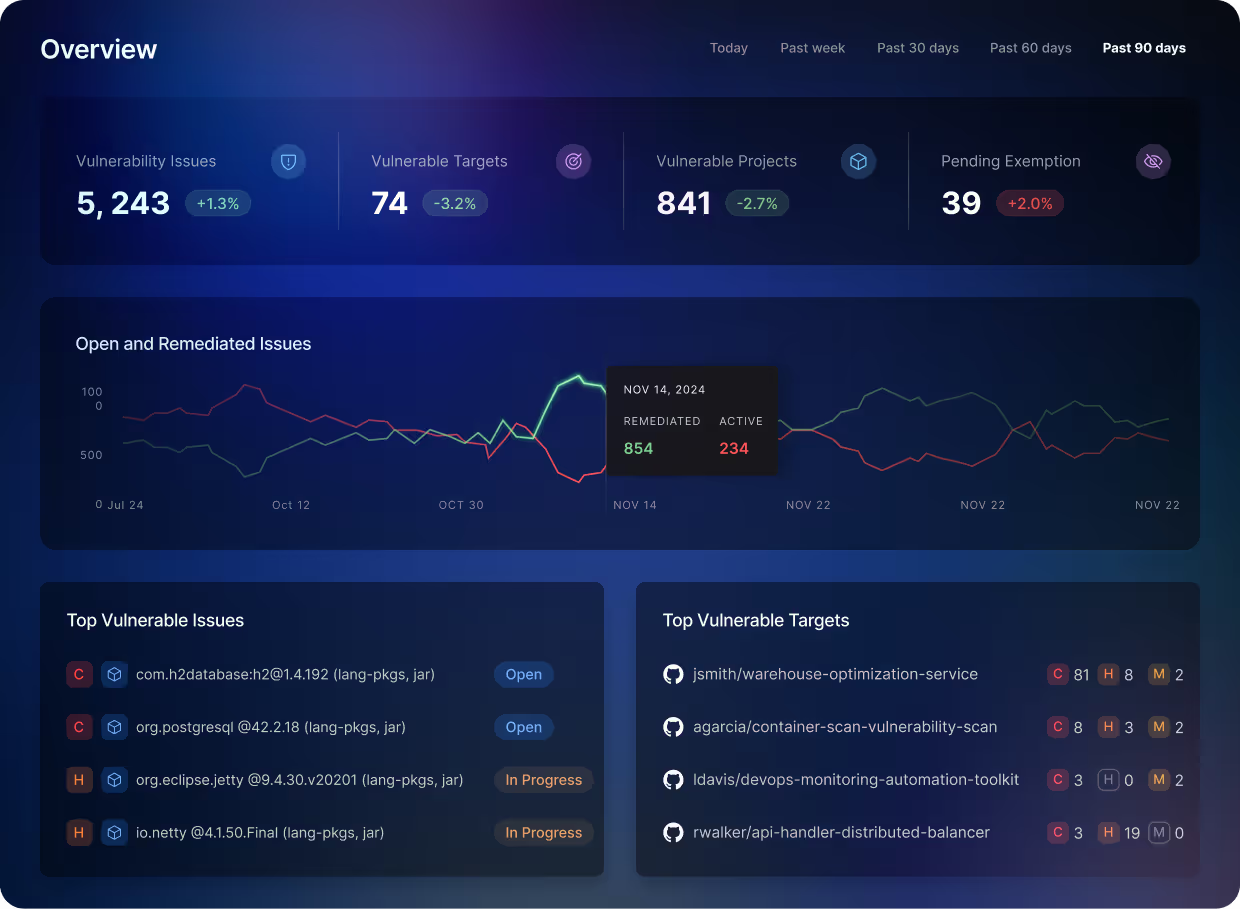
Pipeline-Wide Posture
Unified Vulnerability Management
See and remediate all your vulnerabilities in one place for every security tool in your pipeline, even across multiple vendors.
Vulnerability Deduplication
Reduce the noise in your pipelines with automatic deduplication of vulnerabilities found across multiple tools.
Remediation Prioritization
Prioritize remediation with more than CVSS, using EPSS, static reachability, and runtime reachability analysis.
Pipeline-Level Policies
True Pipeline Policy Enforcement
Pipeline-level policies enforce outcomes across multiple stages, steps, tools, and vendors instead of individual tests.
Enforce Security Requirements
Define security policies to require specific tests in your pipelines and take appropriate action on adverse test results.
Auditing and Change Control
Always maintain a full history of policy evaluations, actions taken, and policy changes made across pipelines.
Developer-First Security
Integrated with developer workflows
Bring security into developers' existing workflows, with IDE integrations, auto-Pull Requests, JIRA ticket creation, and more.
AI-guided remediation
Help developers remediate security vulnerability faster and more easily with AI-provided and validated fixes.
Issue Exemption
Create approval steps or work with devs to review and exempt specific issues from your security policies.
AppSec Testing with Flexibility for Every Pipeline
Tailor security to your unique software projects and pipelines, with a broad range of available application security testing options at every stage of the software development lifecycle (SDLC)





























Best-of-Breed Harness AST
Start with best-of-breed Harness scanners for SAST, SCA, container scanning, and more.
Security Partner Integrations
Complement Harness scanners with 50+ partner integrations for additional security tests.
Pre-built integrations
Easily deploy Harness or partner AST across your pipelines in just few clicks with pre-built integrations.
Frequently Asked Questions
What is Application Security Testing (AST)?
Application Security Testing (AST) is a comprehensive approach to identifying security vulnerabilities in software applications throughout the development lifecycle. AST encompasses multiple testing methodologies including static application security testing (SAST), software composition analysis (SCA), and dynamic application security testing (DAST). By integrating AST into your DevSecOps pipeline, development teams can detect and remediate security issues earlier in the SDLC, reducing risk and preventing costly breaches in production environments.

What is container security and why is it important?
Container security protects containerized applications and infrastructure from vulnerabilities and misconfigurations. As containers package applications with their dependencies, container security scanning examines base images, application code, and runtime configurations for vulnerabilities. Container security is critical in modern DevSecOps environments because a single vulnerable container image can be deployed thousands of times across your infrastructure, exponentially increasing risk exposure.

How does SCA differ from traditional Application Security Testing?
Software Composition Analysis focuses specifically on third-party and open-source components, while traditional application security testing primarily examines proprietary code. SCA tools maintain databases of known vulnerabilities in millions of open-source packages, providing continuous monitoring as new vulnerabilities are disclosed. In DevSecOps environments, combining SCA with SAST and container security creates a complete application security testing strategy that addresses both custom code and dependency risks.

How does Application Security Testing integrate with DevSecOps?
Application security testing integrates seamlessly into DevSecOps workflows by embedding security checks directly into CI/CD pipelines. SAST scans analyze code commits, SCA tools monitor dependencies during builds, and container security scans validate images before deployment. This "shift-left" approach enables development teams to identify and fix vulnerabilities automatically without disrupting development velocity, making security a shared responsibility across development, security, and operations teams.

When should I implement Static Application Security Testing (SAST)?
Static application security testing should be implemented early in the software development lifecycle, ideally when developers commit code to version control. Integrating SAST into your DevSecOps pipeline enables immediate feedback on security issues while code context is fresh in developers' minds. Organizations implementing SAST during development reduce remediation costs by 100x compared to fixing vulnerabilities in production, making early-stage application security testing a cost-effective security investment.

What are the benefits of automating Application Security Testing in CI/CD?
Automating application security testing in CI/CD pipelines enables continuous security validation without manual intervention. Automated SAST, SCA, and container security scans provide immediate feedback to developers, preventing vulnerable code from reaching production. This DevSecOps approach reduces security bottlenecks, accelerates release cycles, and ensures consistent security standards across all deployments. Organizations with automated AST report 50% faster vulnerability remediation times and improved developer productivity.

How do I choose the right Application Security Testing tools?
Selecting application security testing tools requires evaluating your technology stack, development workflow, and security requirements. Prioritize solutions offering comprehensive coverage including SAST for custom code analysis, SCA for dependency management, and container security for modern infrastructure. The best AST tools integrate seamlessly into DevSecOps pipelines, provide low false-positive rates, offer developer-friendly remediation guidance, and support your programming languages and frameworks. Consider scalability, reporting capabilities, and compliance support when evaluating solutions.


.svg)