
Harness's Security Testing Orchestration (STO) module automates API security testing within the DevOps pipeline, addressing the OWASP Top 10 vulnerabilities and beyond, to proactively protect against the increasing rate of API attacks. This approach not only identifies vulnerabilities early but also integrates security into the development lifecycle, enhancing overall DevSecOps maturity.
As cybersecurity attacks continue to increase, it’s more important than ever for any organization to have a security testing methodology to secure their APIs. There are various ways to secure APIs, and Harness has developed a unique methodology. In this blog, we’ll share our approach as a useful reference for other software companies to consider as they prioritize API security testing.
What is an API?
An application programming interface (API) is a software intermediary that allows two applications to communicate to each other. According to Gartner:
An application programming interface (API) is an interface that provides programmatic access to service functionality and data within an application or a database. It can be used as a building block for the development of new interactions with humans, other applications or smart devices. Companies use APIs to serve the needs of a digital transformation or an ecosystem, and start a platform business model.
Each time we use any app — whether posting to Facebook, sending a text or Slack message, or checking the weather on our phone — we’re using an API. For example: when you use an application on your mobile phone, the application connects to the internet and sends data to a designated server. The server then retrieves that data, interprets it, performs the necessary actions, and sends it back to your phone. The application then interprets that data and presents you with the information you wanted in a readable way. All of this happens via an API.
Specifications like OpenAPI or swagger help define the files required to describe APIs. These files then help organizations identify the necessary documentation, integrations, and testing tools to effectively manage their APIs.
What is API Security Testing?
API security testing involves testing for vulnerabilities to prevent attacks and reduce risk for your organization. While it’s great to know that APIs are airtight, you also want to proactively find any security gaps in this process, so engineers can fix them before they impact customers or the business. In addition, this testing can help ensure that the API stays true to its defined specifications.
Security testing helps ensure that basic security requirements have been met, including the conditions of user access, encryption, and authentication concerns. The idea behind API scanning is to craft inputs to coax bugs and undefined behavior out of an API, essentially mimicking the actions and attack vectors of would-be hackers.
These are the high-level steps necessary for security testing APIs:
- Define the APIs that need to be tested.
- Testers provide information on inputs and outputs of the API, using a variety of specification formats, including OpenAPI v2 / v3, Postman Collections, and HAR files.
- API security tests use this information to construct fuzzed input tailored to the input the API expects.
- The output of API security testing is a report of any vulnerabilities or bugs found while fuzzing the API. This could include SQL and OS command injections, authorization/authentication bypasses, path traversal issues, and Open Web Application Security Project (OWASP) Top 10 API vulnerabilities, including broken auth, security misconfiguration, and data exposure.
While many organizations have teams and departments devoted to testing after production, more and more we’re seeing that API security testing is becoming a part of the DevOps pipeline. This makes sense as it ensures that vulnerabilities are caught before code hits production.
Why API Testing Now?
Serving as a fundamental part of modern software development across all industries, APIs continue to grow in number. This increase in API usage is due in part to the standards that organizations have developed to foster API adoption. Because APIs are the heart of many applications, it’s more important than ever to adopt security testing into your software development lifecycle (SDLC).
Ensuring that APIs are conformant to published specifications and resilient to potentially malicious input is critical to an organization’s overall security. API attacks have more than doubled the growth in API traffic in the last 12 months, according to Salt Labs’ Q1 2022 State of API Security report (published March 2022). The report also indicated that:
- 95% of organizations running production APIs have experienced an API security incident in the last 12 months
- Most organizations are unprepared to handle these challenges, with over a third (34%) having no API security strategy
- Traditional security measures continue to fail, giving organizations a false sense of security
The Harness API Testing Strategy
While the OWASP Top 10 API Vulnerabilities are critical, to truly take your DevOps to the next level, this list is really just a starting point. Harness follows the full lifecycle of API security testing, bringing security and DevOps together into DevSecOps.
Testing isn’t a one-time project. To keep your APIs safe from vulnerabilities, it’s an ongoing process to be repeated regularly. At Harness, we use our Security Testing Orchestration (STO) module for testing automation and orchestration. Using STO, we run scans at regular intervals triggered directly from the pipeline and send emails if and when scan results contain critical or high vulnerabilities. We can then keep refining criteria to trigger the scan and an alert.
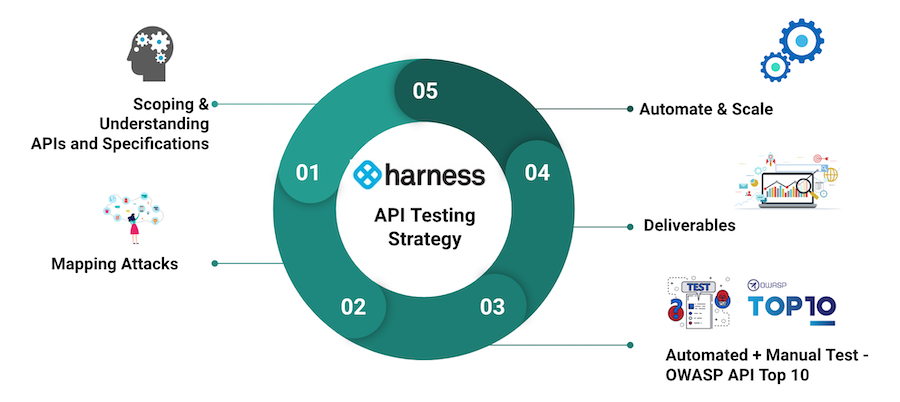
Our testing strategy covers five key areas:
- Scoping and understanding APIs and specifications
- Mapping attacks
- Automated and manual test (OWASP API Top 10)
- Deliverables
- Automate and Scale
1. Scoping & Understanding APIs and Specifications
Define the Scope
It is important to first define all the areas we would be covering as a part of testing. Generally, organizations document all their APIs using swagger or the OpenAPI spec, and these can be leveraged to understand the scope.
Understand the APIs and Business Use
Understanding APIs and their business use is of paramount importance in order to determine the amount of impact security loopholes would have on business. Additionally, this helps us build tailor-made attacks on APIs.
APIs expand the capabilities and functionalities business can offer, without putting a ton of resources behind integrations. To get the most out of APIs, businesses typically use APIs to:
- Integrate with third-party APIs
- Build APIs for internal use
- Build APIs and expose APIs for external use
Understanding which of the categories above current testing falls into is key. It’s important to think like an attacker.
First, Check the Spec – API as a Contract
An API is essentially a contract between the client and the server or between two applications. Before any implementation test can begin, it is important to make sure that the contract is correct. This can be done first by inspecting the spec (or the service contract itself, for example a Swagger interface or OpenAPI reference) and making sure that endpoints are correctly named, resources and their types correctly reflect the object model, there is no missing functionality or duplicate functionality, and relationships between resources are reflected in the API correctly.
2. Mapping Attacks
Mind-map the Attacks
Now that you know what APIs are designed for, their underlying technology, and specifications, it is so much easier to mind-map the attacks.
Generally, all the low-hanging fruit would be covered by automated tools. What you really want to focus on here is how business logic flows can be covered. Focus on business-specific flows to try and find the scenario that may be very difficult for any automated security tool to find.
You can also focus on chained attacks here. Taking the tools reported as baseline and associating them with other findings to create an attack scenario could be a focus here.
3. Automated + Manual Test – OWASP API Top 10
Review the OWASP API Top 10
The OWASP Foundation has a list of the top 10 security threats to APIs. Review the list on their site to prepare your teams.This is fundamental in any type of security testing.
Run an Automated Tool
There are a number of automated tools that can help improve efficiency. Instead of relying on manual testing, these automated tools will save time and resources. We’ve shared some of our favorites below:
- BurpSuite Pro and Traceable AI help find security issues, along with many other supporting tools
- Open source tools like Postman and/or SoapUI
- Burp has an extensive set of supporting plug-ins, which can be used to focus on various attacks, like the OpenAPI Parser
Test Business Logic Flows
Business logic vulnerabilities are flaws in the design and implementation of an API that allow an attacker to elicit unintended behavior. This potentially enables attackers to manipulate legitimate functionality to achieve a malicious goal.
For example, look at how certain permissions are given to resources, how licensing is being validated, and how cost to customer is calculated. If a potential manipulation or flaw in the above scenario exists, then it’s a confidentiality, integrity, and availability, also known as the CIA breach, which could lead to revenue loss for the business.
4. Deliverables
Reporting what we have found so far during the course of testing is the ultimate outcome. To make stakeholders aware of the risk, create associated tasks in JIRA, or any other ticketing system, and track them on a single security dashboard.
5. Automate and Scale
Considering the amount of rapid development happening throughout the year, the security team must keep up with the speed of software delivery. Automation enables scale.
There are various ways to automate both API testing and testing changes during each release. Since it’s not possible to test all the APIs during each of the release cycles, you’ll need to pick a cadence to perform complete API testing. For the rest of the releases, you would be picking up just the delta.
This integration of API testing in our pipeline takes our DevOps to the next level, achieving a maturing DevSecOps practice.
Harness Security Testing Orchestration
Ultimately, there’s no “one size fits all” when it comes to security testing. However, given the increase in attacks on APIs, having the right tools in place is key for proactive protection.
Want to learn more about how Harness can help automate your API security testing? Request a demo for Harness STO today!
