Software Composition Analysis
Continuously monitor open source usage across all your software projects, identify software vulnerabilities and license risk, and prioritize remediation using EPSS, static reachability, and runtime reachability analysis.
Continuously Monitor Projects
Continuously scan software projects as part of your CI/CD pipelines to identify any newly identified vulnerabilities or other risks.
Find Risk Everywhere
Scan everywhere open source software is used, from direct software dependencies to transitive packages and even container images.
Ruthlessly Prioritize Remediation
Go beyond simple CVSS and prioritize based on actual risk - considering likelihood of exploit, reachability in code, and runtime risk.
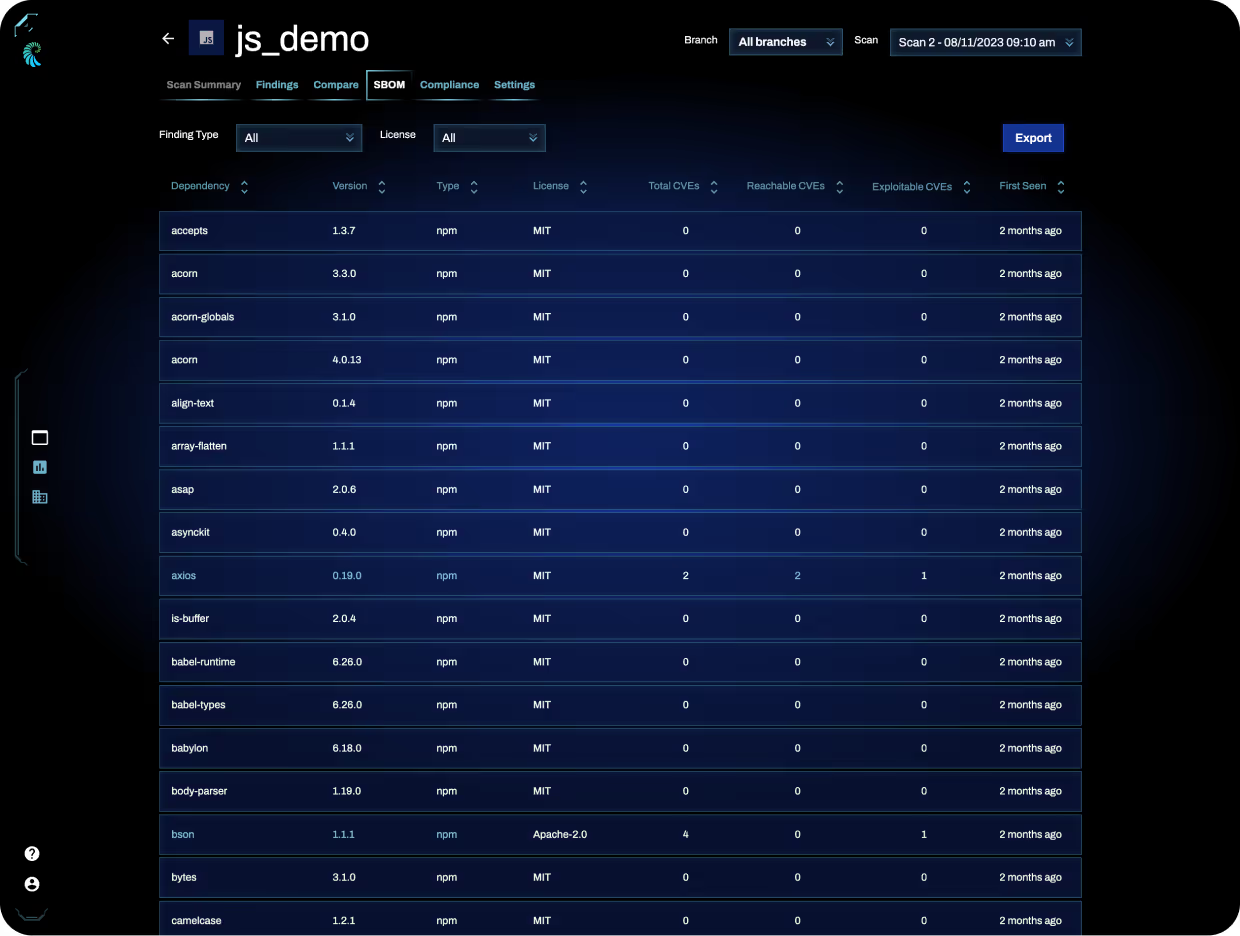
Find All Your Open Source Risk
Secure Your Open Source Code
Identifies open source libraries included in your project and alerts you to known security vulnerabilities and license risks.
Software Bill of Materials
Generate a Software Bill of Materials (SBOM) for your projects in CycloneDX, SPDX, or VEX and take action in Harness pipelines.
Transitive Dependency Scanning
Discovers and scans transitive dependencies to unlimited depth, similar to how a compiler includes them during compilation.
Find Hidden Container Risks
Analyzes every layer in a container image, identifies open source components, and alerts you to vulnerabilities and license risks.
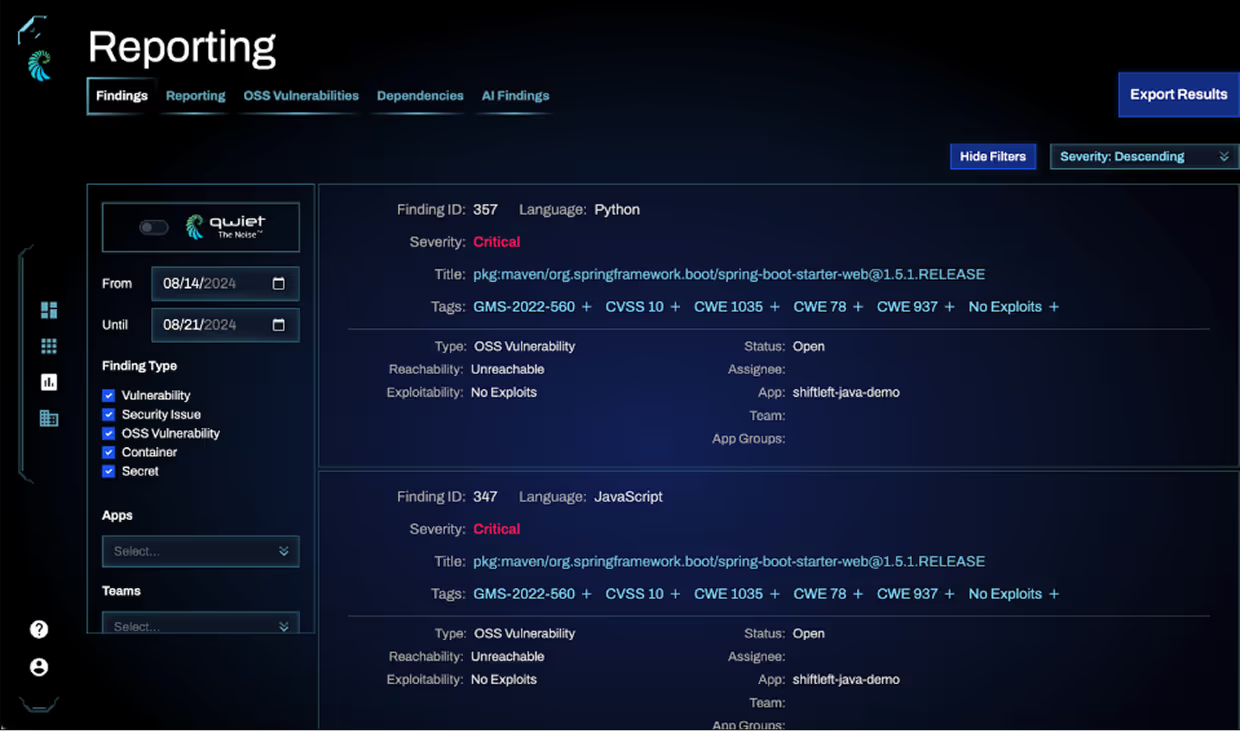
Prioritize by Real-World Risk
Start with Exploitable Vulnerabilities
EPSS scoring helps you go beyond simple CVSS ratings and prioritize based on the likelihood of exploitation in production.
Identify Reachable Vulnerabilities
CPG-based approach analyzes data flow through your code to identify reachable vulnerabilities in OSS with higher accuracy.
Incorporate Runtime Reachability
Harness correlates SCA findings with runtime data to prioritize vulnerabilities with the greatest risk in production environments.
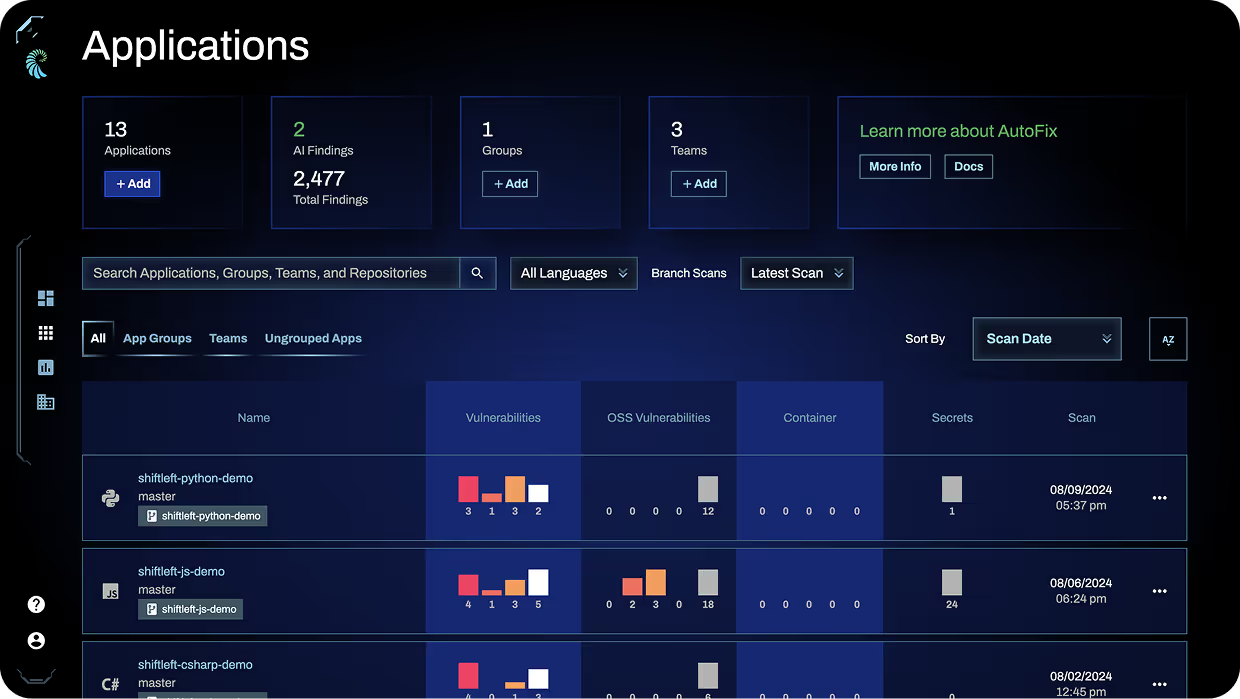
SCA Designed for DevSecOps
Seamless CI/CD Integration
Easily deploy SCA across all your Harness pipelines in just a few clicks with our pre-built integration and pipeline templates.
Automate Open Source Governance
Combine with Harness STO to create and enforce pipeline policies to govern acceptable use of OSS in your software projects.
Fit Into Developer Workflows
Trigger manual scans, or bring findings from automated scans straight to your developers in their IDEs so they can take action.
Comprehensive Supply Chain Security
Harness helps you secure every part of your software supply chain, with application security testing solutions for open source security, container, artifact, and even AI security.
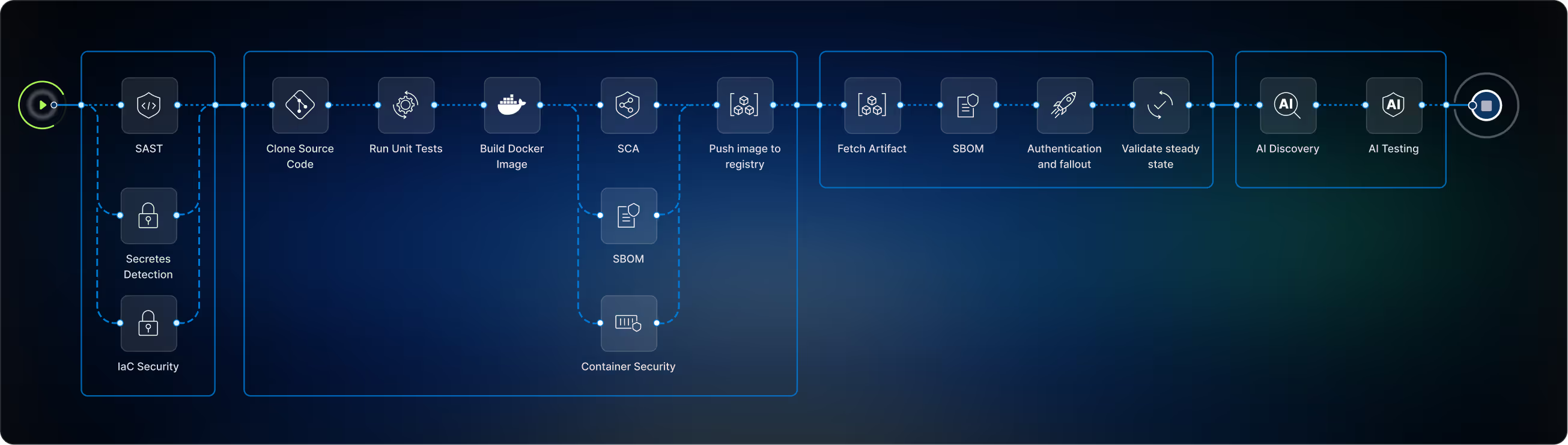
CI/CD Security
Secure your code repositories, artifacts, and CI/CD tools, and align them with industry-standard risk frameworks to ensure compliance with CIS benchmarks, OWASP Top 10 CI/CD risks, and SLSA.
Container Security
Scan images for vulnerabilities, secrets, and compliance risks, correlating findings with your application code through our patented Code Property Graph to prioritize remediation based on reachability and exploitability.
Artifact Security
Manage, secure, and govern software artifacts throughout their lifecycle. Automatically generate SBOMs, manage attestations, and enforce policies to ensure the integrity and provenance of your artifacts.
AI Security
Discover all the Large Language Models (LLMs), MCP servers, MCP tools, and agents in your applications to eliminate shadow AI, then test and protect against AI-specific threats like the OWASP Top 10 LLM risks.
Frequently Asked Questions
What is Software Composition Analysis (SCA)?
Software Composition Analysis (SCA) is a security testing methodology that identifies and analyzes open source components, third-party libraries, and dependencies in your applications. SCA tools automatically scan your codebase to create a complete inventory of all external components, detect known vulnerabilities (CVEs), check license compliance risks, and provide remediation guidance. By continuously monitoring your software supply chain, SCA helps development and security teams understand exactly what's in their applications and proactively address risks before they reach production.

How does dependency scanning work?
Dependency scanning works by analyzing your application's build files, package manifests, and container images to identify all direct and transitive dependencies. The SCA tool reads configuration files like package.json, requirements.txt, pom.xml, or go.mod to catalog every library and framework your code relies on—including dependencies of dependencies.
Once the inventory is complete, the scanner cross-references each component against vulnerability databases (NVD, GitHub Advisory Database, OSV) to identify known security issues. The tool then reports findings with severity scores (CVSS), exploit likelihood (EPSS), and actionable fix recommendations, enabling your team to prioritize and remediate vulnerabilities efficiently.

What types of vulnerabilities can SCA tools detect?
SCA tools detect a wide range of security vulnerabilities in open source components and third-party dependencies, including:
Known CVEs: Published vulnerabilities with assigned CVE identifiers, severity scores, and available patches
Outdated packages: Components running versions that are end-of-life or no longer maintained by their maintainers
Malicious packages: Intentionally harmful code including typosquatting attacks, dependency confusion, and supply chain poisoning
License compliance risks: Incompatible or restrictive licenses (GPL, AGPL) that conflict with your usage policies
Unpatched critical vulnerabilities: High-severity issues like Log4Shell, Heartbleed, or similar widespread threats
Transitive dependency risks: Vulnerabilities hidden deep in your dependency tree that aren't directly imported
By detecting these issues early in the development lifecycle, SCA enables teams to secure their software supply chain before vulnerabilities reach production environments.
Turn on screen reader support
To enable screen reader support, press ⌘+Option+Z To learn about keyboard shortcuts, press ⌘slash

What's the difference between SCA and SAST?
SCA (Software Composition Analysis) and SAST (Static Application Security Testing) are complementary security testing methodologies that examine different aspects of your code:
SCA focuses on open source and third-party code:
- Scans open source libraries, dependencies, and packages you didn't write
- Detects known vulnerabilities with published CVEs
- Checks license compliance and component versioning
- Monitors your software supply chain for risks
SAST focuses on first-party code:
- Analyzes source code you or your team wrote
- Identifies coding errors, logic flaws, and security weaknesses
- 4Detects issues like SQL injection, XSS, and buffer overflows in custom code
- Reviews code structure and implementation patterns
Most organizations need both: SAST secures the code you write, while SCA secures the 70-90% of modern applications composed of open source and third-party components. Together, they provide comprehensive application security coverage across your entire codebase.

How does SCA help with open source license compliance?
SCA tools automatically detect and track every open source license across your dependencies, helping you avoid legal and compliance risks. The scanner identifies licenses like MIT, Apache 2.0, GPL, AGPL, and BSD, then flags potential conflicts based on your usage policies. For example, if you're building proprietary commercial software, SCA will alert you when GPL-licensed components could trigger copyleft obligations requiring you to open-source your code.
Beyond detection, SCA provides:
- Policy enforcement: Automatically block builds containing prohibited licenses
- License inventory reports: Complete SBOM (Software Bill of Materials) for audits
- Risk scoring: Identify high-risk licenses that require legal review
This automation saves legal review time, prevents accidental license violations, and ensures your software distribution remains compliant with open source licensing terms and your corporate policies.

Can SCA scan container images for vulnerabilities?
Yes, modern SCA solutions scan container images to detect vulnerabilities in every layer of your containers. The tool unpacks each layer—base OS, system libraries, language runtimes, and application dependencies—to create a complete inventory of components.
It then identifies vulnerabilities in:
- Base images: Outdated or vulnerable OS packages (Ubuntu, Alpine, Debian distributions)
- System libraries: OpenSSL, glibc, curl, and other foundational components
- Language-specific dependencies: npm packages, Python wheels, Java JARs, Go modules embedded in the image
- Application binaries: Compiled code and executables copied into containers
Container scanning integrates into your CI/CD pipeline to block vulnerable images before deployment. This ensures your containerized applications stay secure across development, staging, and production environments without manual inspection of every image layer.

How does SCA integrate with DevOps and CI/CD pipelines?
SCA integrates seamlessly into modern DevOps workflows to provide automated security scanning without slowing down development velocity.
Integration options include:
- Version control systems: GitHub, GitLab, Bitbucket—scanning pull requests before merge
- CI/CD platforms: Harness
- Container registries: Docker Hub, Amazon ECR, Azure Container Registry—image scanning before deployment
- IDE plugins: Real-time vulnerability detection as developers write code in VS Code, IntelliJ, or other editors
- Package managers: npm, pip, Maven, NuGet—scanning during dependency installation
The SCA tool runs automatically at multiple checkpoints in your pipeline, providing immediate feedback through inline PR comments, build status checks, and dashboard alerts. You can configure quality gates to fail builds when critical vulnerabilities are detected, or set policies to block deployments of non-compliant components. This "shift-left" approach catches security issues early when they're fastest and cheapest to fix, without requiring security experts to manually review every change.

How should I prioritize vulnerability remediation with CVSS and EPSS scores?
Effective vulnerability prioritization combines multiple risk factors rather than relying solely on severity scores. Here's a practical framework:
Use CVSS scores (0-10) to understand severity:
- Critical/High (7.0-10.0): Serious vulnerabilities with significant potential impact
- Medium (4.0-6.9): Moderate risks requiring attention
- Low (0.1-3.9): Minor issues to address during normal maintenance
Add EPSS scores (0-100%) to assess exploit likelihood:
- High EPSS (>50%): Actively targeted by attackers, prioritize immediately
- Medium EPSS (10-50%): Elevated risk, schedule remediation soon
- Low EPSS (<10%): Lower probability, can be addressed in regular patching cycles
Add reachability analysis to assess whether code is executed
- Reachable: vulnerability is in an OSS function/method called by your code, lower risk
- Not reachable: vulnerability is not in an OSS function/method called by your code, lower risk
Prioritization matrix:
- Critical + High EPSS + reachable: Fix immediately—these are actively exploited high-severity vulnerabilities
- High + Medium EPSS + reachable: Address within days—serious risks with moderate exploit likelihood
- Medium + High EPSS + reachable : Faster than severity alone suggests—attackers are targeting these
- Low CVSS or EPSS: Schedule for routine maintenance
- Not reachable: Schedule for routine maintenance

What is SBOM generation and why does it matter?
SBOM (Software Bill of Materials) generation creates a comprehensive, machine-readable inventory of all components in your software—similar to an ingredients list on food packaging. An SBOM documents every open source library, dependency version, license, and supplier for your application. SCA tools automatically generate SBOMs in standard formats like SPDX, CycloneDX, or SWID tags.
Why SBOMs matter:
- Regulatory compliance: Required by executive orders (EO 14028) and regulations for government software suppliers
- Incident response: When new vulnerabilities like Log4Shell emerge, quickly identify which applications are affected
- Supply chain transparency: Understand your software supply chain dependencies and third-party risks
- Vendor risk management: Share SBOMs with customers who need to assess your software's security posture
- Audit readiness: Provide complete documentation for SOC 2, ISO 27001, or customer security questionnaires
Modern SCA solutions generate and continuously update SBOMs automatically, ensuring you always have current documentation of your software composition without manual maintenance. This transparency is increasingly essential for software procurement, security assessments, and meeting emerging compliance requirements.

What programming languages and package managers does SCA support?
Comprehensive SCA solutions support multiple programming languages and their associated package managers to cover polyglot development environments.
Common support includes:
- JavaScript/TypeScript: npm, Yarn, pnpm—scanning package.json and lock files
- Python: pip, Poetry, Pipenv—analyzing requirements.txt, Pipfile, and pyproject.toml
- Java/Kotlin: Maven, Gradle—scanning pom.xml, build.gradle, and JAR files
- Ruby: Bundler, RubyGems—analyzing Gemfile and Gemfile.lock
- Go: Go modules—scanning go.mod and go.sum
- PHP: Composer—analyzing composer.json and lock files
- .NET/C#: NuGet—scanning packages.config, .csproj files
- Swift: CocoaPods, Swift Package Manager
- C/C++: Conan, vcpkg
Beyond language support, effective SCA tools also scan container images (Docker), infrastructure as code (Terraform), and cloud-native platforms (Kubernetes manifests). This broad coverage ensures security across your entire technology stack without requiring multiple specialized tools. When evaluating SCA solutions, verify support for your specific languages, frameworks, and build systems to ensure comprehensive vulnerability detection across all your applications.


.svg)