Static Application Security Testing
Build trust with your developers with an industry-leading 97% True Positive rate, up to 90% fewer False Positives, and prioritization based on exploitability and runtime reachability.
Fewer False Alarms
Harness finds vulnerabilities by analyzing the flow of data through your code, only alerting when tainted data can reach a dangerous operation.
Find Hidden Vulnerabilities
Our code property graph can identify complex vulnerabilities that span multiple functions, classes, and even different parts of your app.
Minimal Tuning Required
Harness understands your code right out of the box, without having to spend weeks or months tuning rules for every app like legacy SAST tools.
Better Security Through Code Awareness
Our patented Code Property Graph (CPG) is more effective than simple pattern matching and abstract syntax tree analysis used by legacy SAST tools, integrating both data flow and control flow analyis to understand how your code behaves in the context of actual exectution scenarios.
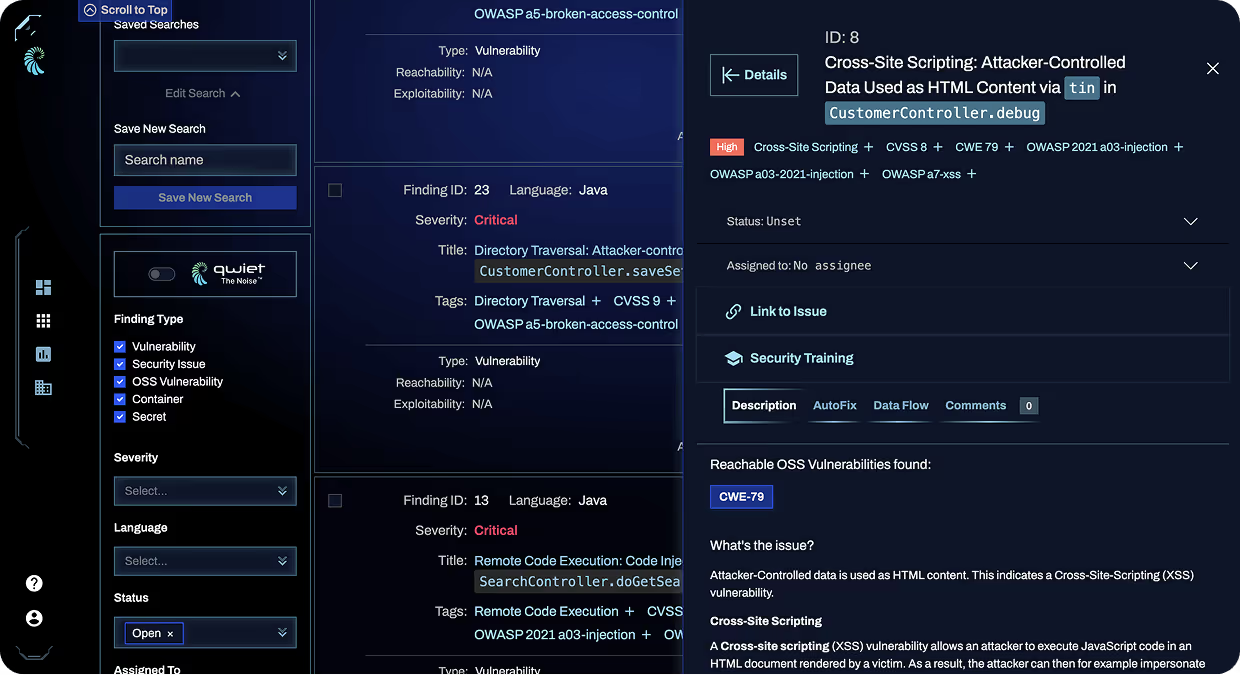
Find the Most Critical Vulnerabilities
Higher Scan Accuracy
Start with a true understanding of your code to find more real vulnerabilities and fewer false positives than legacy SAST tools.
Find Vulnerabilities and Secrets
Scan your code for vulnerabilities, as well as hardcoded secrets that can lead to breaches or supply chain attacks in production.
Continuously Improving
Harness continuously enhances the CPG with new language & framework annotations, improving accuracy for every customer.
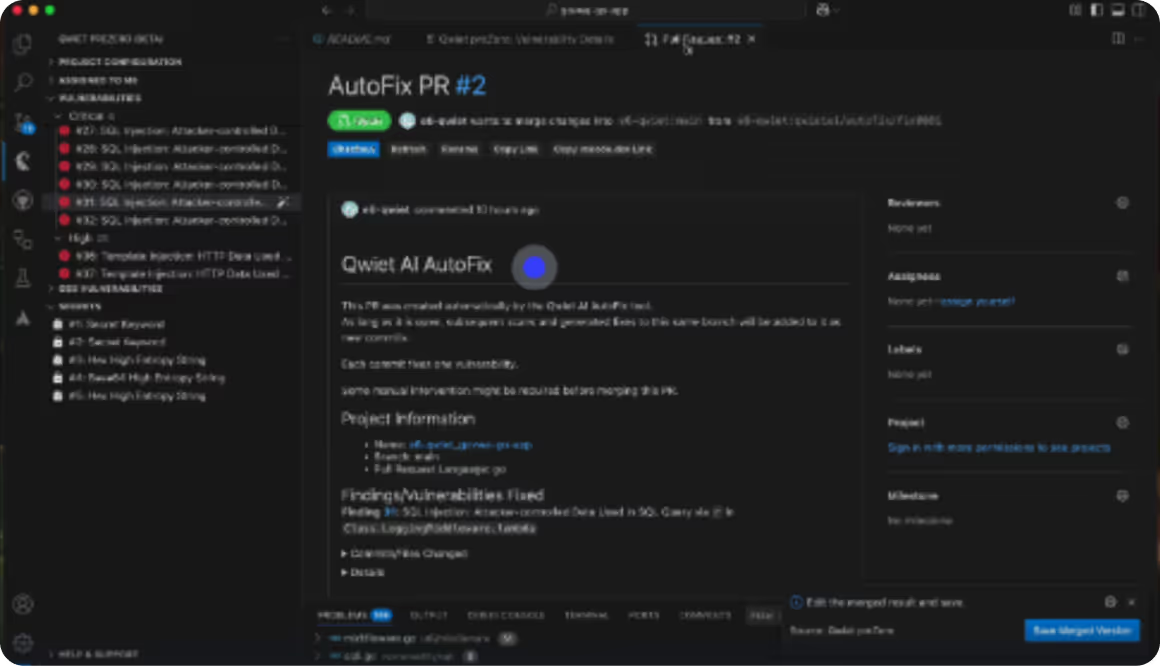
AI-Powered Remediation
Full Agentic Workflow
Seven different AI agents perform separate tasks to suggest, validate, and refine fixes that your developers can actually use.
Better Code Fixes
A full agentic workflow suggests better code fixes, eliminating vulnerabilities while still fitting into your existing code .
95% Faster Remediation
AI-generated code fixes make it easy for developers with even minimal security training to remediate vulnerabilities fast.
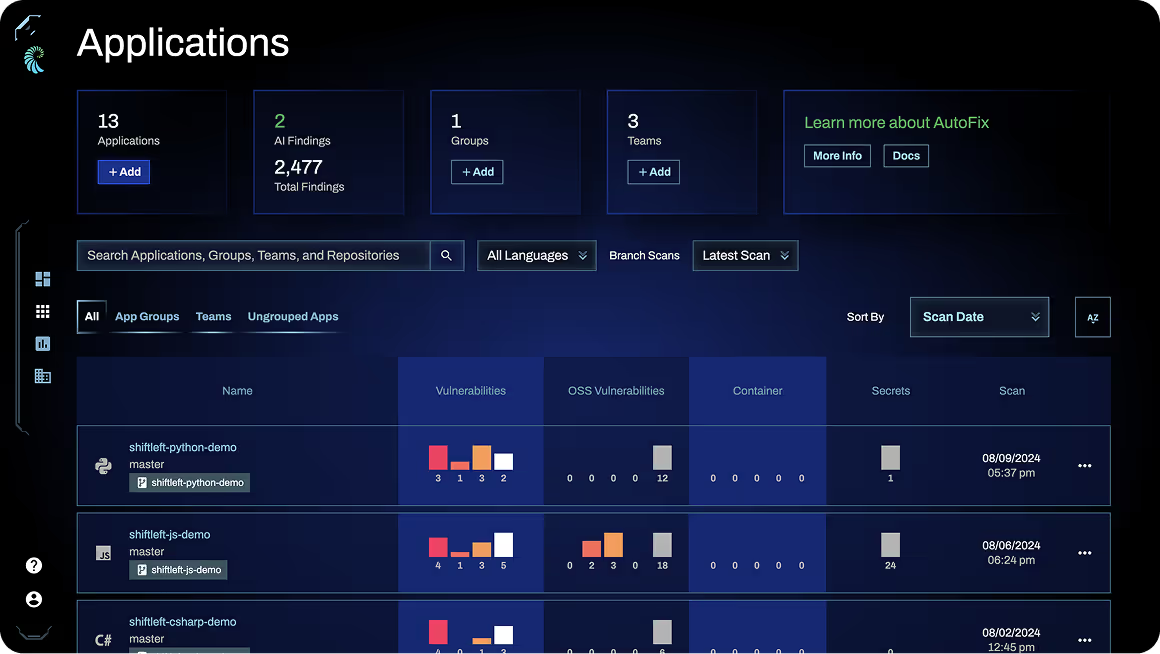
SAST Designed for DevSecOps
Seamless CI/CD Integration
Easily deploy SAST across all your Harness pipelines in just a few clicks with our pre-built integration and pipeline templates.
1-Click Scanning
Perform SAST, SCA, secrets detection, and container security with a single scan to always ensure comprehensive AppSec testing.
10x Faster Scans
Scan millions of lines of code in minutes to fit into any DevOps pipeline, identifying security risk without sacrificing lead times.
Fit Into Developer Workflows
Trigger manual scans, or bring findings from automated scans straight to your developers in their IDEs so they can take action.
Cover All Your Pipelines
Harness SAST is the only solution designed specifically for DevSecOps, with the accuracy, speed, and ease-of-deployment you need to integrate with and cover all your CI/CD pipelines.
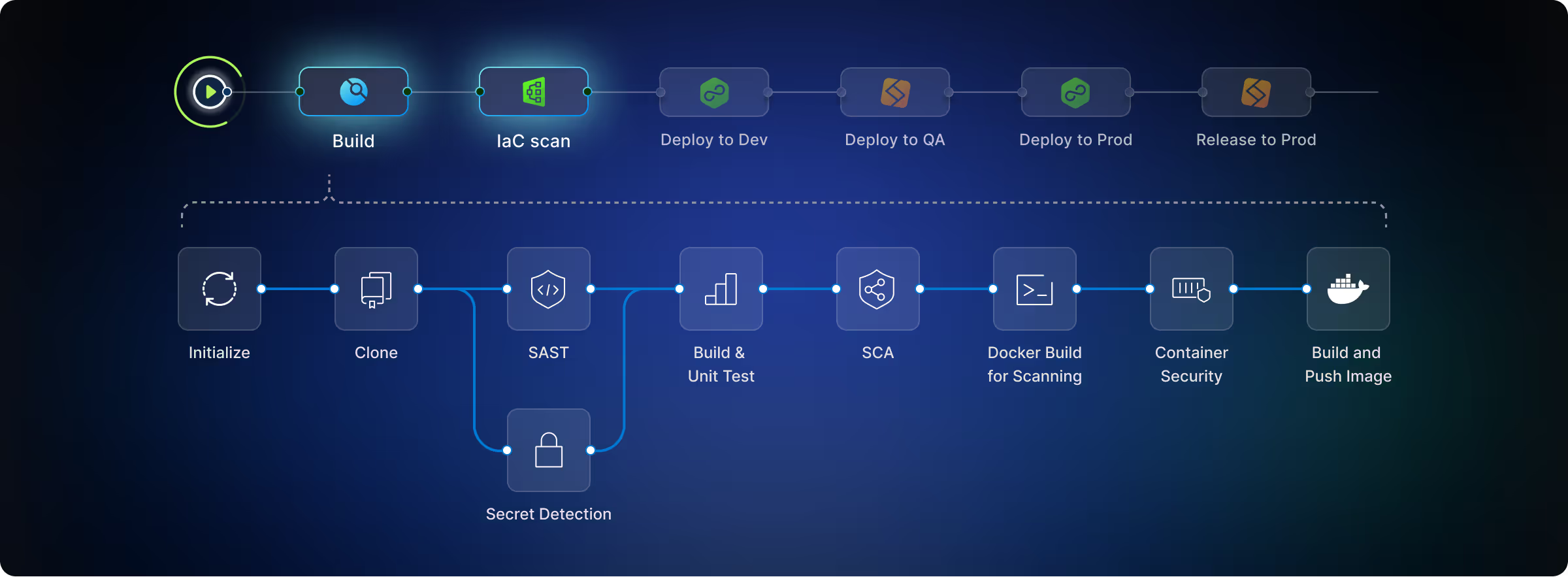
Deploy Fast With Pre-Built Integration
Harness SAST is designed to work natively within Harness pipelines, making it super easy to deploy as a new security stage or step in a single click.
Cover All Your Pipelines
Pipeline templates allow you to standardize SAST testing, configuring once and then scaling deployment across 100s or even 1000s of pipelines.
Manage Risk at the Pipeline Level
Security Testing Orchestration aggregates SAST findings with other security scanners used in a pipeline, giving you a pipeline-wide view into risk.
Frequently Asked Questions
How does SAST help with compliance requirements?
SAST plays a crucial role in meeting regulatory and industry compliance requirements by providing documented evidence of secure software development practices. Here's how it supports compliance:
Key compliance standards:
- PCI DSS Requirement 6.5: Organizations handling payment card data must address common coding vulnerabilities. SAST provides automated verification that code is tested for OWASP Top 10 vulnerabilities including injection flaws, broken authentication, and sensitive data exposure.
- GDPR and data protection: SAST helps identify vulnerabilities that could lead to data breaches, demonstrating due diligence in protecting personal information. Tools can flag insecure data handling, weak encryption, and improper access controls.
- HIPAA: Healthcare organizations must implement technical safeguards for protected health information (PHI). SAST validates secure coding practices and identifies potential vulnerabilities that could compromise patient data.
- SOC 2: SAST provides evidence of security controls in the development lifecycle, supporting availability, confidentiality, and security trust principles.
- NIST Secure Software Development Framework (SSDF): SAST enables organizations to implement the "Review and/or analyze human-readable code" practice (PW.7) within the NIST framework.
- ISO 27001: SAST supports secure development lifecycle requirements and provides audit trails for security testing activities.
Compliance benefits:
- Automated documentation: SAST generates reports showing vulnerability testing history, remediation timelines, and coverage metrics
- Audit trails: Detailed logs demonstrate continuous security testing throughout development
- Policy enforcement: Configure quality gates to prevent non-compliant code from reaching production
- Standards mapping: Leading tools map findings to CWE, OWASP, and compliance-specific requirements
- Executive reporting: Dashboard views showing security posture and compliance status
By integrating SAST into your SDLC, you create verifiable evidence that your organization follows secure coding practices—essential for passing audits and maintaining compliance certifications.

What are the advantages and limitations of SAST?
Advantages:
- Early vulnerability detection: SAST identifies security flaws during development, when fixes are 10-100x cheaper than in production. Developers receive immediate feedback and can remediate issues before code review.
- Comprehensive code coverage: Unlike manual reviews or testing, SAST analyzes 100% of your codebase, including rarely executed paths and edge cases that might be missed by dynamic testing
- Pinpoint accuracy: SAST identifies the exact file, line number, and code snippet where vulnerabilities exist, making remediation straightforward for developers.
- No runtime required: SAST doesn't need a compiled or running application, enabling security testing earlier in the SDLC than other methodologies.
- Cost-effective scaling: Automated SAST scans can run continuously across hundreds of projects without additional security staff.
Limitations:
- False positives: SAST tools can flag issues that aren't actually exploitable in context, requiring manual triage and potentially eroding developer trust if not managed properly.
- Language limitations: Each SAST tool supports specific programming languages; polyglot environments may require multiple tools.
- Cannot detect runtime issues: SAST misses vulnerabilities related to deployment configuration, server settings, authentication mechanisms, or third-party service integrations.
Limited context awareness: SAST may not understand business logic or complex data flows across microservices, potentially missing sophisticated vulnerabilities or generating false positives.
For optimal security coverage, combine SAST with DAST, Software Composition Analysis (SCA), and regular penetration testing.

What vulnerabilities can SAST tools detect?
SAST tools can identify a wide range of security vulnerabilities and coding flaws aligned with industry standards like the OWASP Top 10 and CWE/SANS Top 25. Here are the primary vulnerability types:
Injection flaws: SQL injection (SQLi), command injection, LDAP injection, XML injection
Cross-site scripting (XSS): Reflected XSS, stored XSS, DOM-based XSS
Authentication and session management issues: Hardcoded credentials, weak password storage, insecure session handling, missing authentication checks
Cryptographic failures: Weak encryption algorithms, insecure random number generation, improper certificate validation
Additional vulnerabilities: Buffer overflows, path traversal, insecure deserialization, race conditions, memory leaks, insecure API usage
SAST tools detect these issues by analyzing code structure, data flow, and control flow patterns. The most advanced tools can also identify business logic flaws, code quality issues that impact security, and violations of secure coding standards. However, SAST cannot detect runtime-specific vulnerabilities like server misconfigurations or infrastructure issues—which is why it's most effective when combined with DAST and other security testing methods.

How does static code analysis work?
Static code analysis works by examining source code without executing the application. The process begins when a SAST tool parses your code and breaks it down into tokens—individual elements like keywords, operators, and identifiers. These tokens are then used to construct an Abstract Syntax Tree (AST), which represents the hierarchical structure of your code.
Once the AST is built, SAST tools may perform several types of analysis: control flow analysis maps all possible execution paths through your code, data flow analysis tracks how data moves from inputs to outputs, and pattern matching compares code structures against known vulnerability signatures. The tool checks for issues like unsanitized user input flowing into database queries, hardcoded credentials, insecure API usage, and violations of secure coding standards.

What programming languages do SAST tools support?
SAST tools vary significantly in programming language support, with most covering popular languages while some specialize in specific ecosystems. Here's what to expect:
Commonly supported languages (most tools):
- JavaScript/TypeScript
- Python
- Java
- C#/.NET
- PHP
- Ruby
- Go
Frequently supported (major tools):
- C/C++
- Swift/Objective-C
- Kotlin
- Scala
- HTML/CSS
- SQL
Less common (specialized tools):
- Rust
- Perl
- COBOL
- Apex (Salesforce)
- Dart
- R
Framework and ecosystem considerations: Beyond language support, consider whether tools understand your specific frameworks (React, Django, Spring Boot, .NET Core) and can analyze configuration files, Infrastructure as Code (Terraform, CloudFormation), and API specifications.
Multi-language environment challenges: Teams working with polyglot codebases face a critical decision: use a single SAST tool with broad language coverage (potentially sacrificing depth) or deploy multiple specialized tools (adding complexity but improving accuracy).

How do you integrate SAST into CI/CD pipelines?
Integrating SAST into CI/CD pipelines enables automated security scanning with every code change, catching vulnerabilities before they reach production. Here's how to implement it effectively:
Choose your integration point:
- Pre-commit hooks: Scan locally before code is pushed (fastest feedback)
- Pull request/merge request: Scan during code review (balances speed and coverage)
- Build stage: Scan during continuous integration (comprehensive checks)
- Scheduled scans: Run full codebase scans nightly or weekly
Implementation best practices:
- Start with non-blocking scans to establish baselines without disrupting workflows
- Configure quality gates to fail builds only on critical/high-severity issues
- Scan only changed code in PRs for faster feedback (full scans periodically)
- Integrate results into developer tools (IDE plugins, Jira, Slack notifications)
- Establish clear remediation SLAs based on severity levels
Successful SAST integration requires balancing security thoroughness with developer velocity. Start with critical projects, tune false positives, and gradually expand coverage across your organization.

What's the difference between SAST and DAST?
SAST and DAST are complementary testing methodologies that examine applications from different perspectives. SAST (Static Application Security Testing) analyzes code at rest during development, while DAST (Dynamic Application Security Testing) tests running applications in production-like environments.
SAST excels at finding issues like hardcoded secrets, insecure functions, and code-level vulnerabilities before deployment. DAST identifies runtime issues such as authentication problems, server misconfigurations, and vulnerabilities that only appear when the application is running. For comprehensive security coverage, leading organizations use both SAST and DAST together as part of a layered application security strategy.

What is SAST (Static Application Security Testing)?
Static Application Security Testing (SAST) is a security testing methodology that analyzes application source code to identify vulnerabilities without executing the program. SAST examines code from the inside out, giving developers visibility into potential security flaws during the earliest stages of the software development lifecycle (SDLC).
SAST tools scan code as it's written, identifying common vulnerabilities such as SQL injection, cross-site scripting (XSS), buffer overflows, and insecure cryptographic implementations. By catching these issues before compilation or deployment, SAST enables developers to fix security problems when they're least expensive to remediate—saving both time and money while reducing the risk of breaches in production. This proactive approach makes SAST an essential component of modern DevSecOps practices.


.svg)