Supply Chain Security
Secure your entire software supply chain, from open source packages to artifacts and even your CI/CD toolchain, with pipeline-level policy enforcement aligned with industry-standard risk frameworks like SLSA.
Cut Through Supply Chain Noise
Harness AI can analyze all of your software supply chain alerts - from vulnerabilities to OSS risks and compliance violations - to get you started on remediating identified issues.
Know Where to Start
Harness AppSec agent goes beyond vulnerabilities and look across your CI/CD toolchain to find the repos, registries, or build tools with the most risk, telling you where to focus your attention first.
Get Guidance to Remediate Faster
With Harness AI, you can just tell the agent what you want it to do, such as identify an alternate package or artifact to mitigate a license risk, and get AI remediation guidance to help devs fix it.
Secure More than Open Source
Most solutions only focus on open source libraries. But your software supply chain is not just code. Harness helps you secure more - the toolchain used to build it, the artifacts that get deployed, and the provenance of every part along the way.
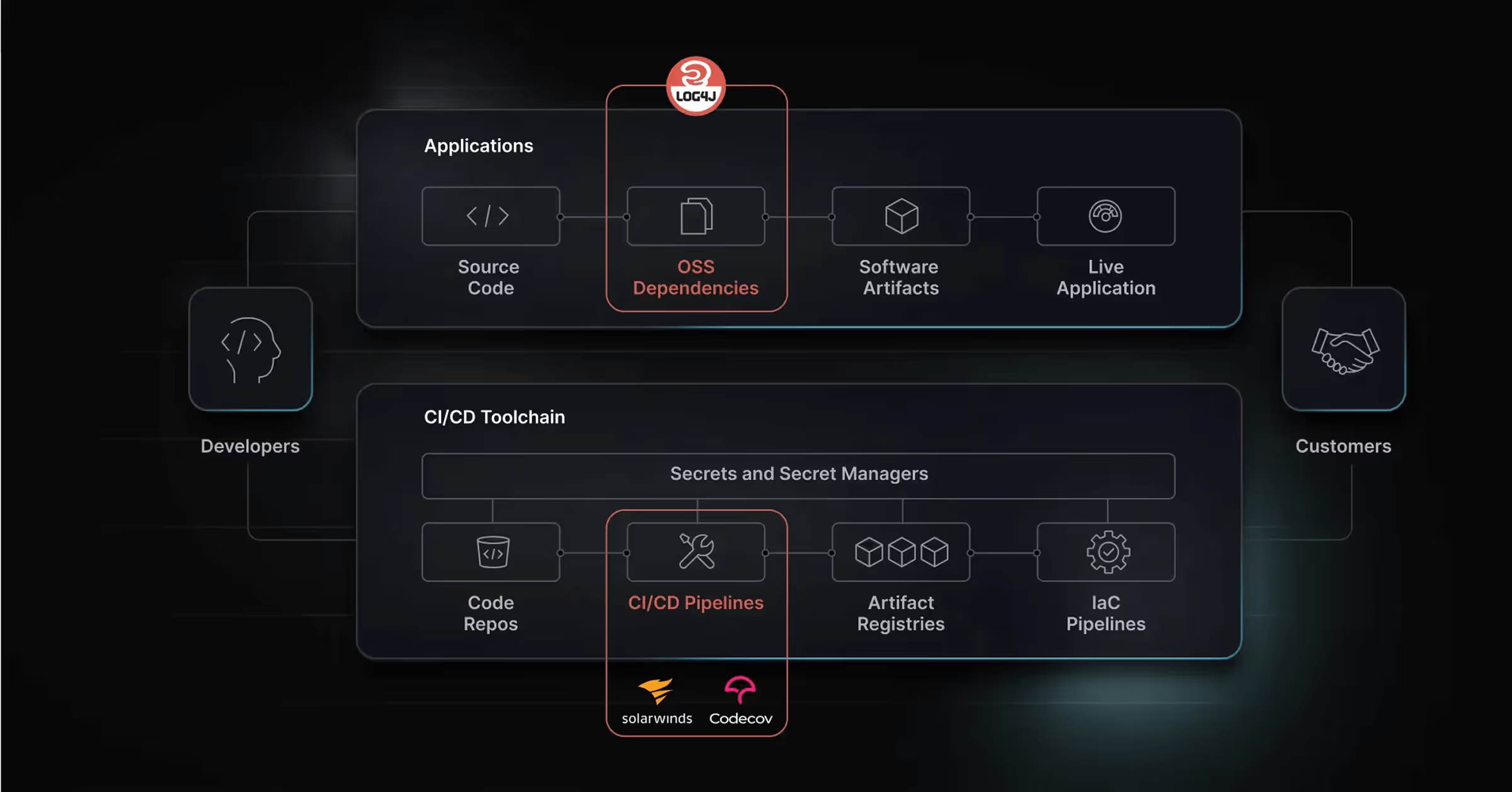
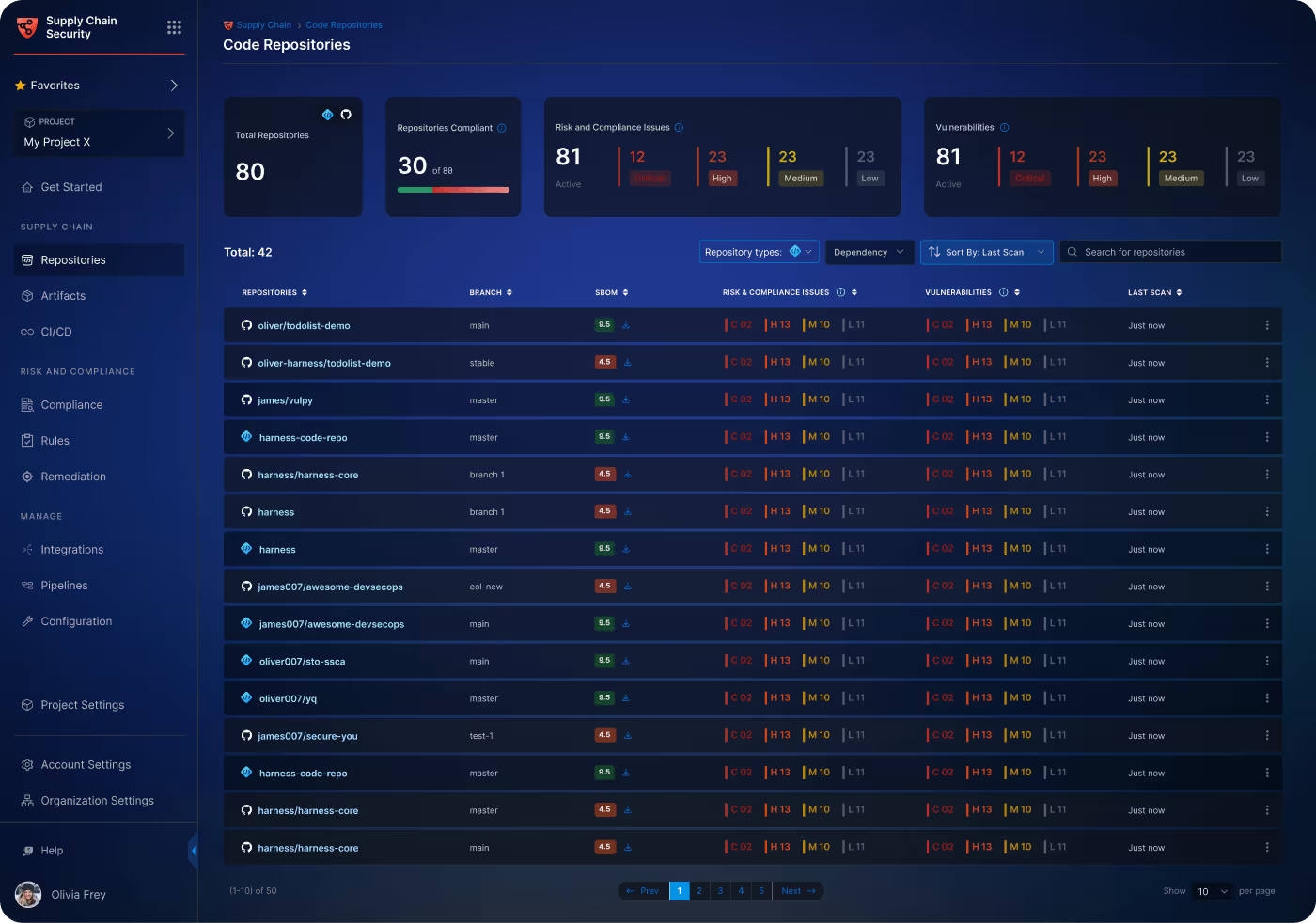
See All Your Supply Chain Risk
Every Part of Your Application
Generate a Software Bill of Materials (SBOM) to see what risky open source and third-party components you have.
Every Vulnerability in Your Repos
Get a unified view into every risk in the repo, from your code to open source packages and container images.
Your Entire Software Supply Chain
See vulnerabilities and secrets in your code, open source libraries, and containers, as well as compliance issues in your repos.
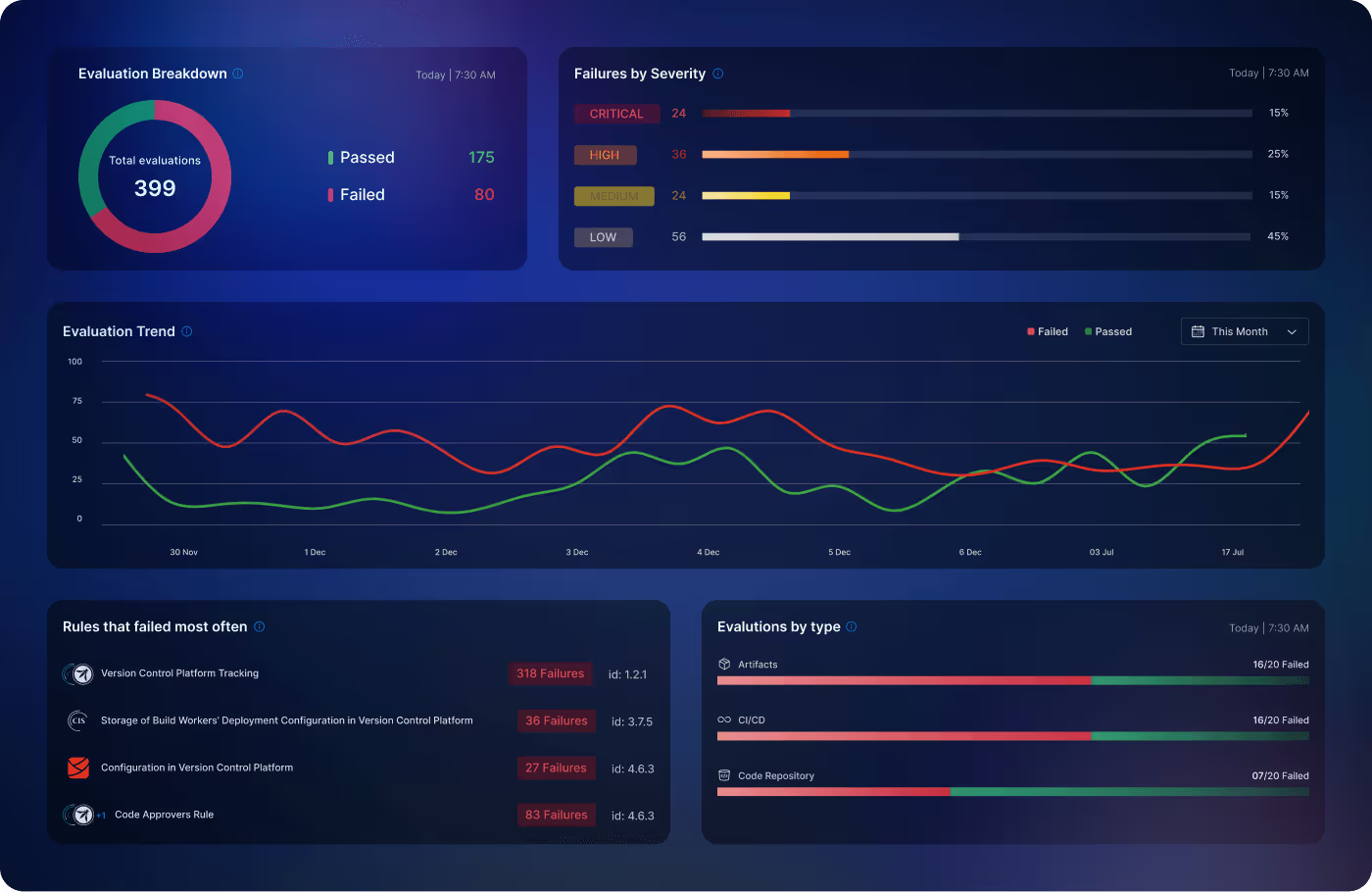
Secure Your CI/CD Toolchain
Industry-Standard Compliance and Reporting
Generate out-of-the-box compliance reports on security posture against industry-standard frameworks such as CIS & OWASP Top 10 Security Risks for CI/CD.
Harden Code Repositories
Create policy rules, apply security checks, and remediate any issues in your code repos to ensure compliance with CIS benchmarks, OWASP Top 10 CI/CD risks, and SLSA.
Secure Build Pipelines
Prevent your build pipelines against unwarranted user input and executable commands that could lead to a compromised build system using supply chain rules.
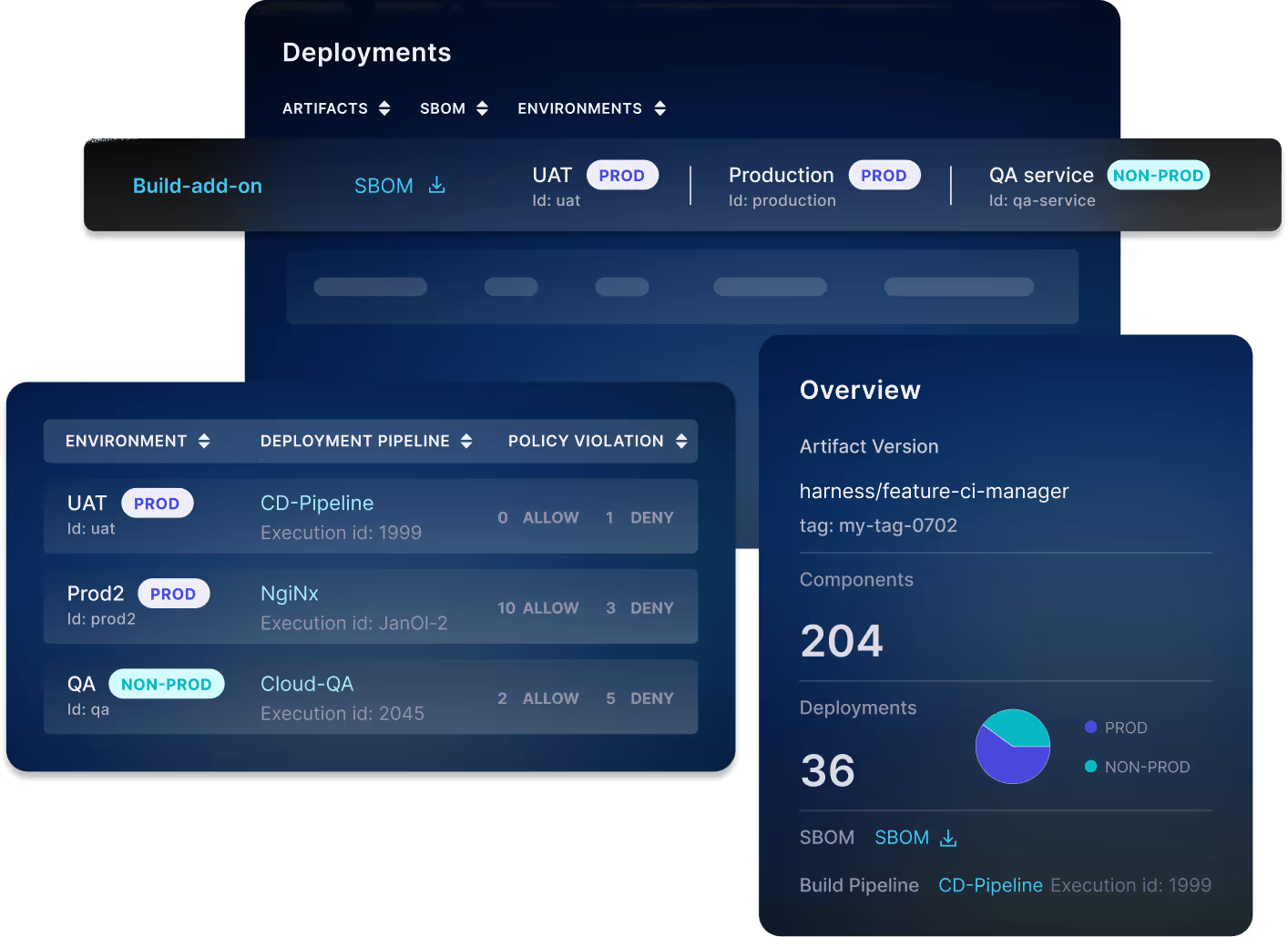
Governance Across Every Pipeline
Track remediation and response
Easily identify affected pipelines, create JIRA tickets, and track remediation to respond to zero-day vulnerabilities.
SBOM policy and governance
Enforce policies using OPA to prevent the use of harmful or risky open source and third-party dependencies.
Block 0-day vulnerabilities
Break the build and mitigate exposure to zero-day vulnerabilities across all your deployed environments.
Achieve SLSA Compliance
Comprehensive Audit Trail
Exportable audit logs capture build and deployment details, such as SLSA attestations, offering full traceability through the SDLC.
Artifact Integrity and Provenance
Establish full software transparency with detailed chain of custody, providing an immutable audit trail for every artifact.
Govern Artifact Promotion with SLSA Build Attestation
Enforce SLSA policies to prevent tampering and ensure artifact integrity and origination from trusted build environments.
Comprehensive Supply Chain Security
Harness helps you secure every part of your software supply chain, with application security testing solutions for open source security, container, artifact, and even AI security.
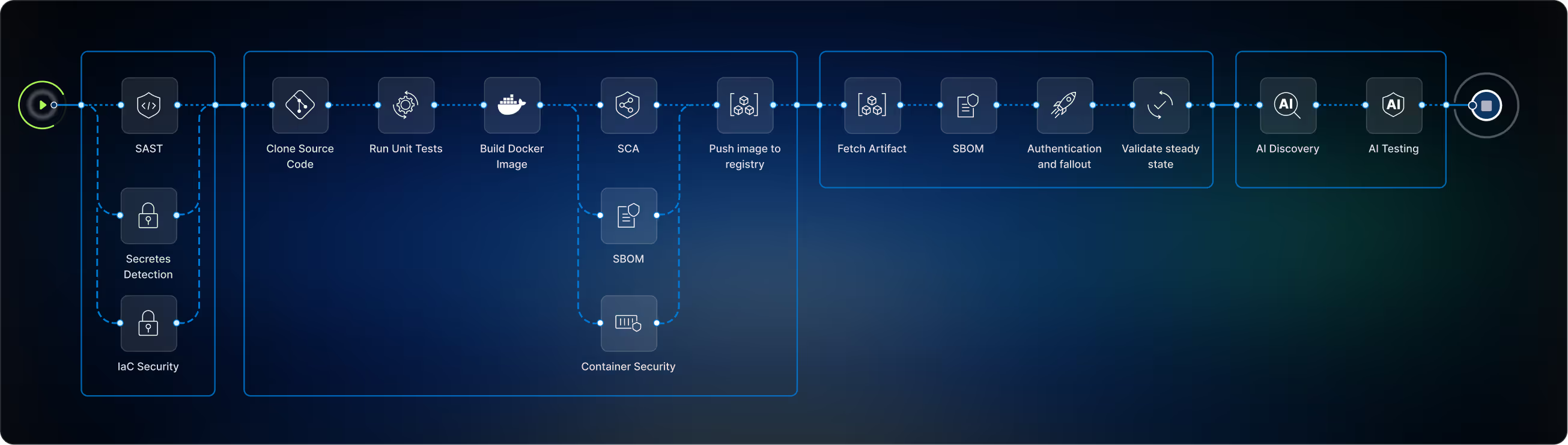
CI/CD Security
Secure your code repositories, artifacts, and CI/CD tools, and align them with industry-standard risk frameworks to ensure compliance with CIS benchmarks, OWASP Top 10 CI/CD risks, and SLSA.
Container Security
Scan images for vulnerabilities, secrets, and compliance risks, correlating findings with your application code through our patented Code Property Graph to prioritize remediation based on reachability and exploitability.
Artifact Security
Manage, secure, and govern software artifacts throughout their lifecycle. Automatically generate SBOMs, manage attestations, and enforce policies to ensure the integrity and provenance of your artifacts.
AI Security
Discover all the Large Language Models (LLMs), MCP servers, MCP tools, and agents in your applications to eliminate shadow AI, then test and protect against AI-specific threats like the OWASP Top 10 LLM risks.
Frequently Asked Questions
What is Software Supply Chain Security?
Software Supply Chain Security (SSCS) protects the entire software development and delivery pipeline from code creation through production deployment. Supply Chain Security encompasses multiple security layers including software composition analysis (SCA), secrets detection, container security, and Software Bill of Materials (SBOM) generation. As modern applications rely on hundreds of third-party dependencies and build tools, software supply chain security has become critical for preventing attacks like the SolarWinds breach and Log4Shell vulnerability that exploit trust relationships in the development ecosystem.

What are the biggest threats to Software Supply Chain Security?
Software Supply Chain Security faces threats including compromised dependencies, malicious package injections, stolen credentials discovered through inadequate secrets detection, and vulnerable container images. High-profile attacks like Codecov, SolarWinds, and npm package compromises demonstrate how attackers exploit trust relationships in the software supply chain. Additional threats include unsigned artifacts, absence of Software Bill of Materials (SBOM) for vulnerability tracking, and insufficient SLSA compliance. Comprehensive Supply Chain Security requires SCA, container security, secrets detection, and provenance verification to mitigate these risks.

How does Software Composition Analysis (SCA) improve Supply Chain Security?
Software Composition Analysis strengthens supply chain security by identifying vulnerabilities, licensing risks, and outdated components in your software dependencies. SCA tools continuously monitor open source and third-party libraries against vulnerability databases, alerting teams to Supply Chain Security risks before exploitation. Modern SCA solutions generate Software Bill of Materials (SBOM) automatically, support secrets detection in dependencies, and integrate with container security scanning to provide comprehensive Software Supply Chain Security coverage across development and deployment environments.

What is the relationship between SLSA compliance and SBOM generation?
SLSA compliance and SBOM generation are complementary Software Supply Chain Security practices. While Software Bill of Materials provides an inventory of components, SLSA establishes verifiable provenance proving where and how software was built. SLSA Level 2 and above require build process documentation that complements SBOM data, creating comprehensive Supply Chain Security attestation. Organizations pursuing SLSA compliance typically generate signed SBOMs with provenance metadata, integrate container security verification, implement secrets detection, and maintain audit trails demonstrating software supply chain integrity.

What is secrets detection and how does it protect the Software Supply Chain?
Secrets detection identifies exposed credentials, API keys, passwords, and tokens accidentally committed to code repositories or embedded in container images. Leaked secrets represent critical software supply chain security vulnerabilities, enabling attackers to compromise systems, access sensitive data, or inject malicious code. Modern secrets detection tools scan code repositories, container security images, and build artifacts in real-time, preventing credential exposure before reaching production. Integrating secrets detection with SCA and SBOM generation creates comprehensive supply chain security protection.

What is a Software Bill of Materials (SBOM)?
A Software Bill of Materials (SBOM) is a comprehensive inventory listing all components, libraries, and dependencies within a software application. SBOMs provide transparency into your Software Supply Chain Security posture by documenting component versions, licenses, and origin information. Regulatory frameworks and executive orders increasingly mandate SBOM generation, making it essential for Supply Chain Security Compliance. Organizations use SBOMs to rapidly identify exposure when new vulnerabilities are disclosed in open source components, enabling faster response to Software Supply Chain Security threats.

What is SLSA and why is it important for Supply Chain Security?
SLSA (Supply Chain Levels for Software Artifacts) is a security framework developed by Google and the OpenSSF that defines standards for securing the Software Supply Chain. SLSA provides four progressive levels of Supply Chain Security maturity, from basic version control to comprehensive build integrity verification. Implementing SLSA helps organizations prevent tampering, ensure build reproducibility, and verify software provenance. SLSA compliance enhances Software Supply Chain Security by establishing trust in your Software Bill of Materials (SBOM) and build artifacts through cryptographic attestation.

How does Container Security relate to Software Supply Chain Security?
Container security is fundamental to Software Supply Chain Security because containers package not only application code but entire dependency chains including base images, libraries, and system packages. Container security scanning examines images for vulnerabilities, malware, misconfigurations, and exposed secrets throughout the supply chain. Since vulnerable container base images affect all downstream applications, container security with SBOM generation provides visibility into your complete Software Supply Chain, enabling teams to track and remediate vulnerabilities across containerized environments efficiently.

How do I generate and maintain an accurate Software Bill of Materials (SBOM)?
Generating accurate Software Bill of Materials requires automated tooling integrated into your CI/CD pipeline that analyzes code, dependencies, and container images. Leading SCA solutions create SBOMs in standardized formats like SPDX or CycloneDX, supporting Software Supply Chain Security compliance requirements. Maintaining SBOM accuracy demands continuous updates as dependencies change, integrating secrets detection to identify credential exposure, and enriching SBOM data with vulnerability information. SLSA-compliant build processes with cryptographic signing ensure SBOM integrity throughout the software supply chain.

How do I implement comprehensive Software Supply Chain Security?
Implementing Software Supply Chain Security requires a multi-layered approach combining SCA for dependency analysis, secrets detection to prevent credential leaks, container security for image validation, and SBOM generation for transparency. Start by integrating SCA tools into your CI/CD pipeline to identify vulnerable dependencies, implement automated secrets detection across repositories, and generate Software Bill of Materials for all releases. Progress toward SLSA compliance by establishing secure build processes, cryptographic signing, and provenance attestation. Regular container security scanning and continuous SBOM updates ensure ongoing Supply Chain Security protection.


.svg)