API Testing
Find and eliminate API vulnerabilities with zero-config, continuous scanning with contextualized remediation. Security test your APIs without disrupting development or slowing down release.
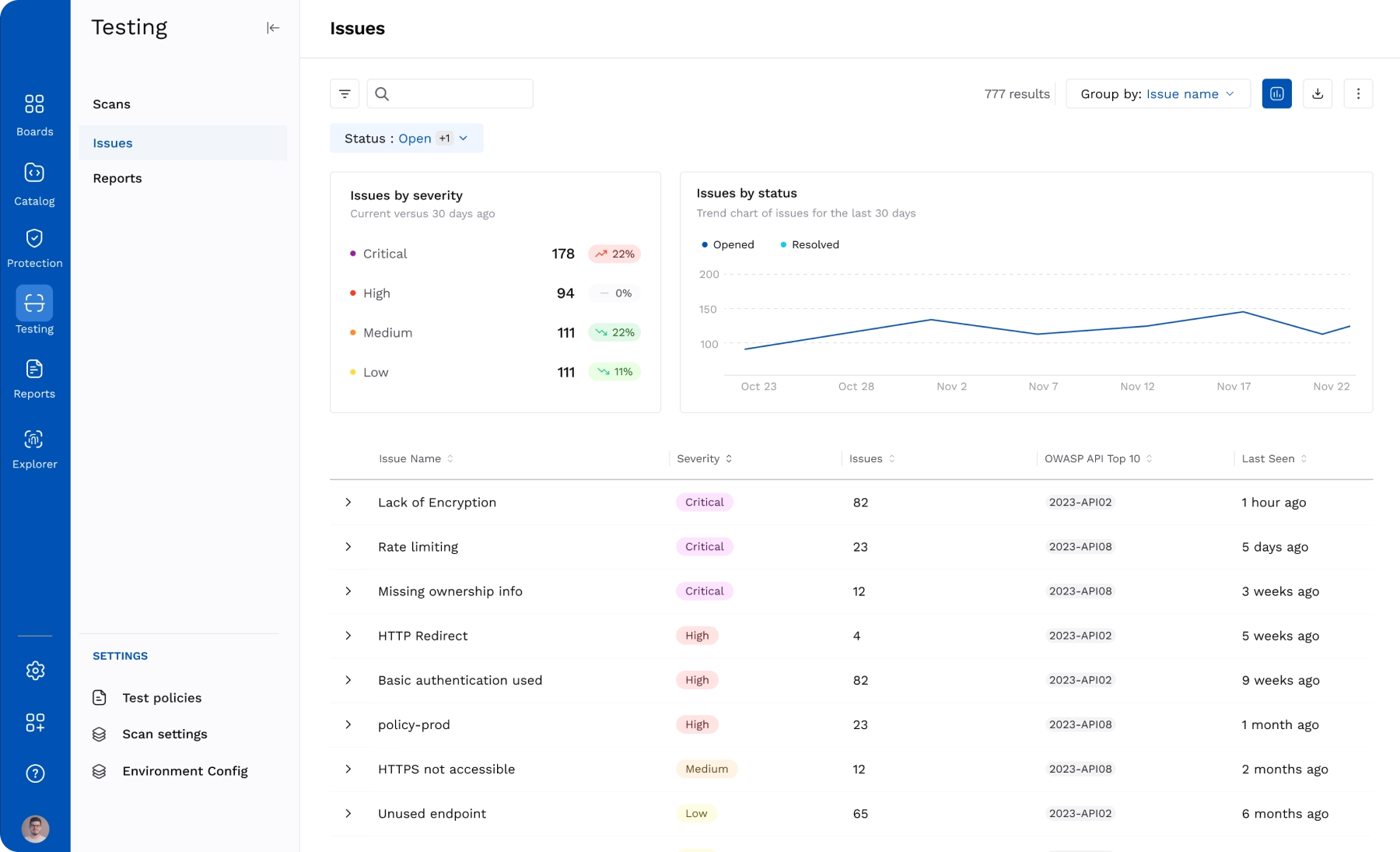
API-Specific Testing
Comprehensive API testing that covers the OWASP API Top 10, including authorization weaknesses, data exposures, and business logic flaws.
Security Without Friction
Scan APIs without disrupting DevOps release cadences, eliminate security friction, and ensure APIs are safe.
Actionable Compliance Validations
Generate detailed vulnerability results, including instance counts and last occurence, so you can prioritize violations before an incident.
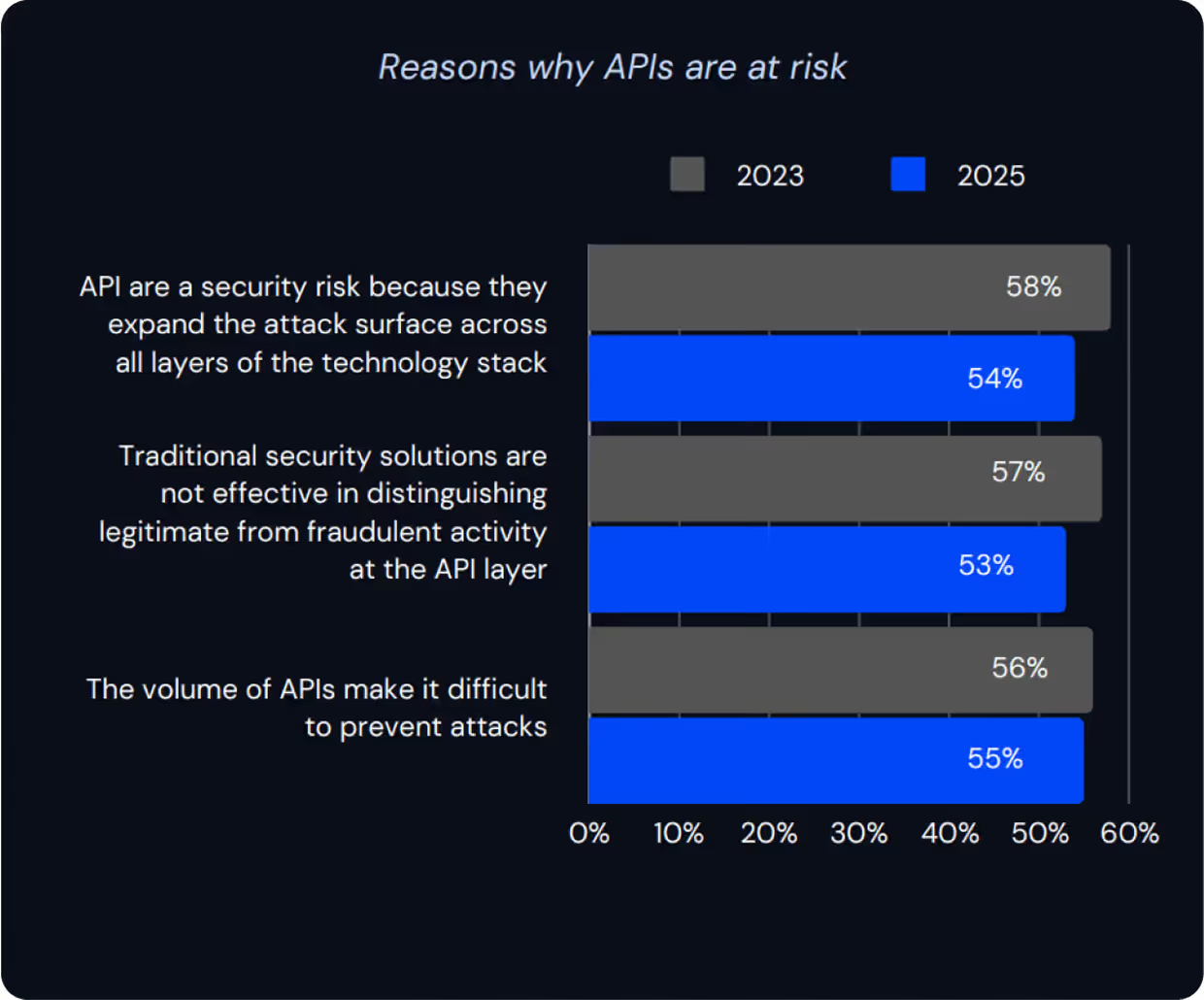
APIs are a Top Attack Vector
APIs indrectly create a large attack surface. Attackers target known API weaknesses or abuse business logic that APIs implement. In Traceable's State of API Security Report, the expanding attack surface, the ineffectiveness of existing API security solutions and the sheer number of unknown APIs were all identified as significant reasons why APIs are at risk.
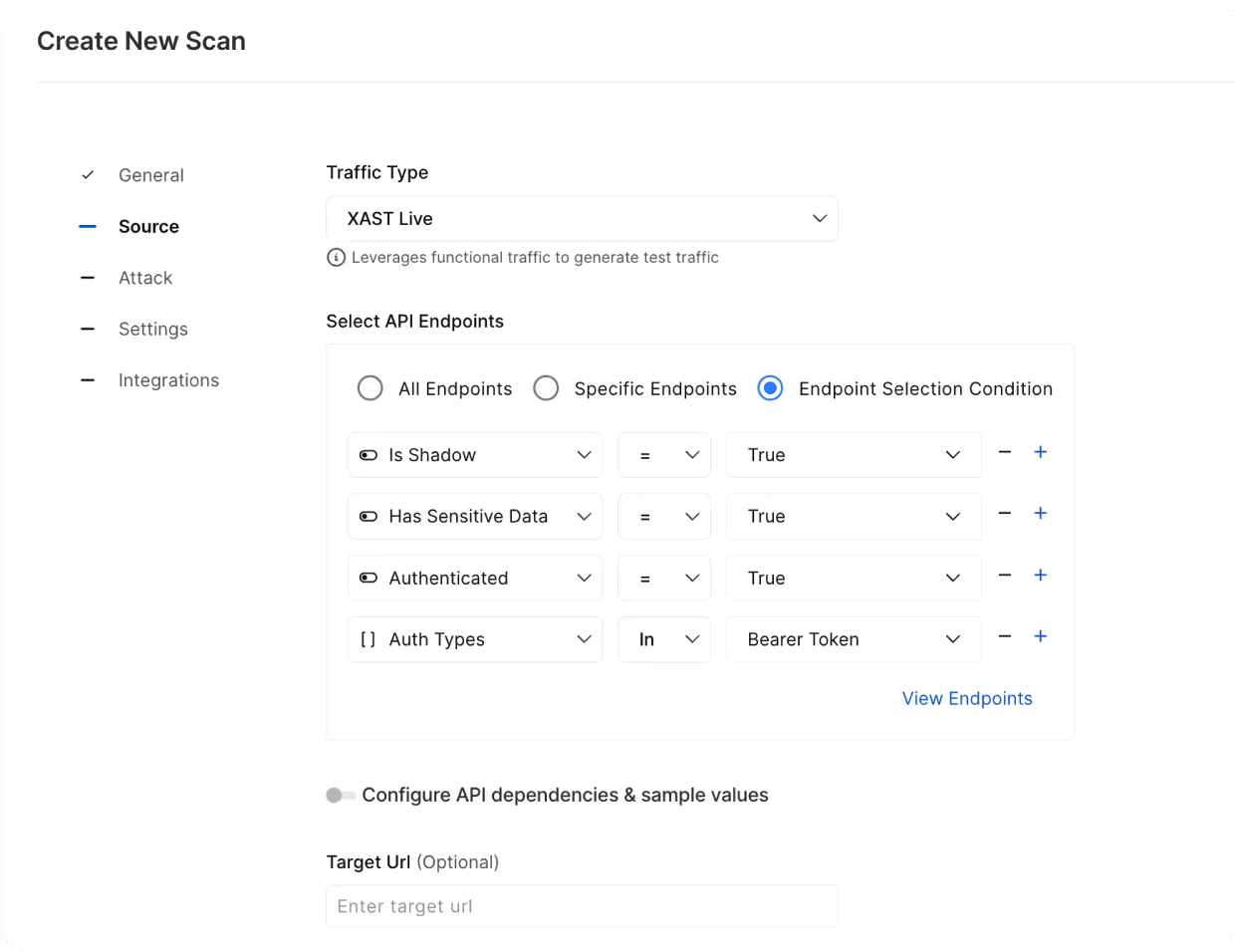
Security Test Based on API Behaviors
Automatically Configure Tests
Create security tests automatically from actual traffic and constrain tests to actively used APIs to reduce vulnerability overload.
Cutdown on Useless Findings
Avoid noise from inactive endpoints and boost pre-production testing using insights from runtime behavior.
Fast and Accurate Scanning
Harness API Testing maintains high accuracy and keeps security scans focused with customizable vulnerability types and support for modern auth mechanisms like JWT, mTLS, OAuth.
Test Using API Documentation
Use OpenAPI Specification (OAS) or GraphQL schema to guide API testing, or repurpose Postman collections that detail API endpoints.
Integrate with DevOps Tools
Shift-left API Testing
Embed security early in the SDLC with easy configuration and without disrupting release velocity.
Integrate Throughout the SDLC
Integrate testing within Harness pipelines, CI/CD services, or project management tools like Jira and ServiceNow so security scanning is continuous throughout the SDLC.
Validate for API Governance
Harness provides closed-loop API security so you can ensure API governance with minimal manual effort and configuration.
Produce Actionable Test Results
Contextualize Findings
Harness API Testing gives you full API context with every finding. Legacy scanners often miss APIs entirely, overwhelm you with unprioritized results, or provide only generalized guidance.
Reproduce Issues Quickly
Results include full API endpoint details, call flows, and user session data, so you can quickly reproduce and resolve security findings.
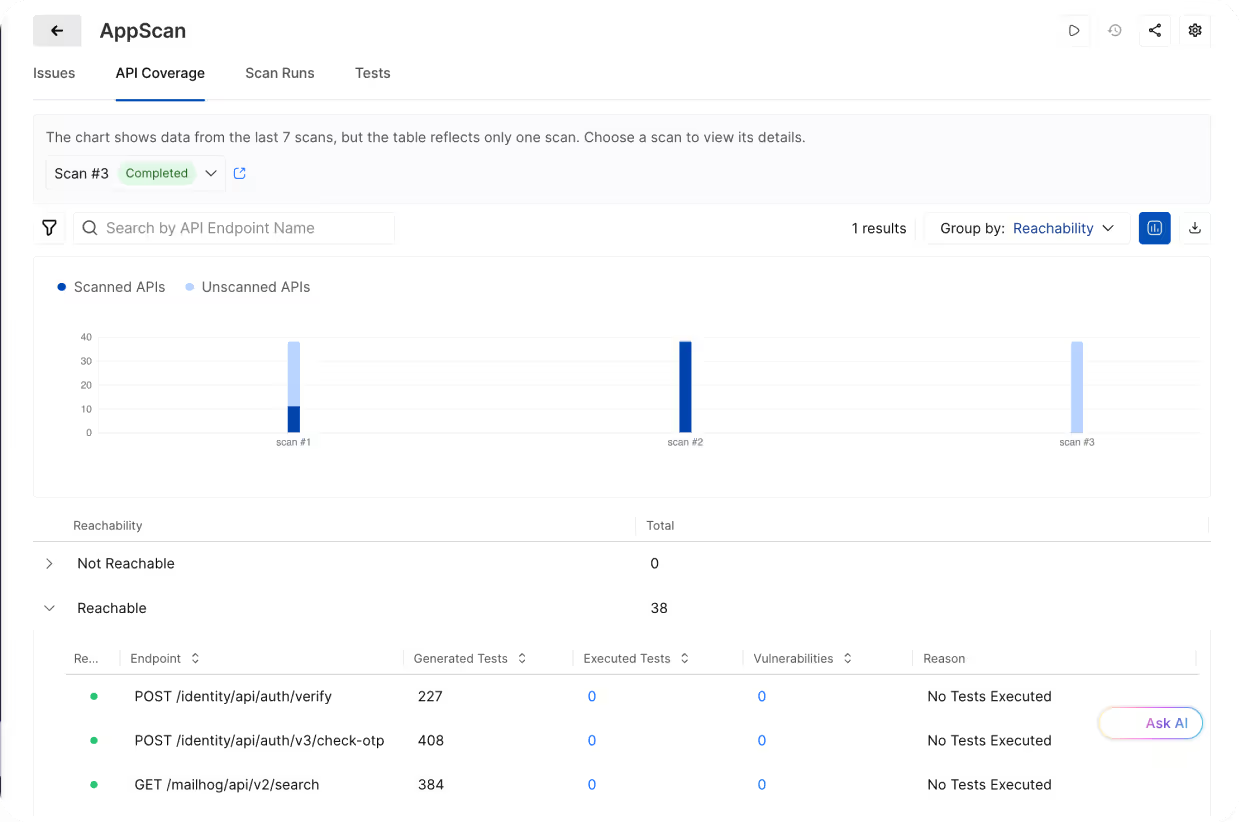
Ensure API Endpoint Coverage
Quickly verify which API endpoints were reachable during scanning, diagnose unscanned APIs, and gather details around generated and executed tests.

Security for Everything in Runtime
The Harness platform informs with API context, identifies sensitive data flows, protects against application-layer attacks, and guides on the best mix of protective controls to stop application abuse.
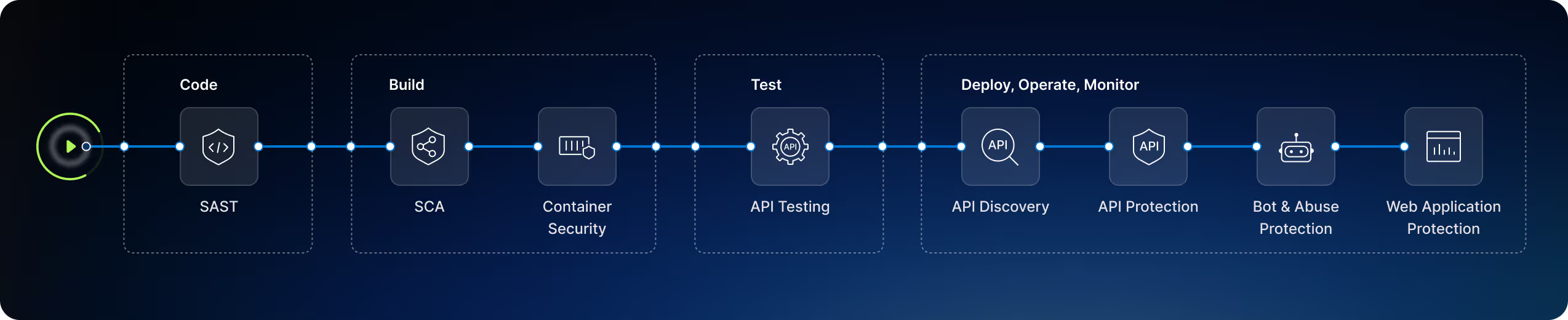
API Discovery
Automatically discover and catalog APIs and gain visibility into your real application attack surface.
API Protection
Protect your APIs with advanced, unified security and defend against evolving threats across hybrid- and multi-cloud environments.
Web Application Firewall
API-first WAF with flexible deployment, coverage for all OWASP Top 10 risks, false positive reduction with API context, and full telemetry to aid SecOps.
Frequently Asked Questions
What is API security testing, and why is it important?
API security testing is the process of finding and validating API vulnerabilities, such as broken authentication, authorization flaws, and injection. API security testing is important because APIs expose sensitive data and business logic by design, making them a top target for attackers.

What’s the difference between API security testing and API penetration testing?
API security testing often includes automated API vulnerability scanning, traffic analysis and manipulation (or fuzzing), plus continuous checks in CI/CD. API penetration testing is typically a tightly-scoped, time-boxed, manual pentest focused on deeper exploitation paths of specific sets of APIs. Many teams use both. Automated API security testing is frequently used for continuous validation and broad application portfolio coverage, while API pentesting is reserved for the organization's most critical assets or where regulation mandates it.

Can you automate API security testing in CI/CD pipelines?
Yes, automated API security testing can run in CI/CD. It's accomplished by executing security test suites on every build, pull request, or release. This “shift-left” approach catches API vulnerabilities early and supports continuous API security posture improvement.

How do you test APIs with authenticated context?
Testing with authenticated context is often where challenges arise for security testing, even for skilled practitioners. Most APIs don't make data or functionality available to anonymous users. Better test tooling provides ways to capture and repurpose valid sessions from live traffic to check for authentication or authorization flaws. Test tools may also provide a macro recording and playback mechanism, or they make use of Selenium scripts that can replay as needed to spawn valid, authenticated sessions.

What is the difference between SAST, DAST, and IAST for APIs?
Static application security testing (SAST) analyzes source code to find API security issues before runtime. Dynamic application security testing (DAST) tests APIs running in infrastruture without the source code context to identify exploitable vulnerabilities. Interactive applicaton security testing (IAST) aims to combine both techniques of SAST and DAST, instrumenting the application runtime directly, using extended traffic analysis, or evaluating application logs to detect issues. Using multiple forms of testing improves API security coverage across the SDLC.

What are common API vulnerabilities to test for?
The OWASP API Security Top 10 is frequently used as a starting point. Top risks include broken object level authorization (BOLA), broken authentication, broken object property level authorization (BOPLA), broken function level authorization (BFLA), security misconfiguration, and unsafe consumption of APIs, specifically third-party APIs.

How do you test APIs for authorization issues?
Authorization testing verifies role-based access control (RBAC) and attribute-based access control (ABAC) mechanisms by exercising API endpoints with different roles, tenants, and/or scopes to confirm least-privilege access. Specifically, testing for horizontal and vertical privilege escalation involves attempting actions beyond the user’s permissions. In the case of horizontal privilege escalation, you are checking to see if one user can access the data or functionality of another user with similar permision levels. In the case of vertical privilege escalation, you are checking to see if a user can attain priviliged or administrative access.

How do you test APIs for authorization issues?
Authorization testing verifies role-based access control (RBAC) and attribute-based access control (ABAC) mechanisms by exercising API endpoints with different roles, tenants, and/or scopes to confirm least-privilege access. Specifically, testing for horizontal and vertical privilege escalation involves attempting actions beyond the user’s permissions. In the case of horizontal privilege escalation, you are checking to see if a user can access unauthorized data or functionality of another user with similar permision levels. In the case of vertical privilege escalation, you are checking to see if a user can attain unauthorized administrative access.

How do you test for broken object level authorization (BOLA)?
To test for BOLA manually, you can attempt to access or modify resources by changing object IDs (e.g., change /users/123 to /users/124) while staying authenticated as a different user. Intercepting proxy tools like Burp Suite or OWASP ZAP common in pentesting can be used to perform this type of valiation. Effective API authorization testing at scale verifies object-level access control across every endpoint and method in an automated way.

How do you test for sensitive data exposure in API responses?
Excessive data exposure testing involves inspecting API responses for sensitive fields such as personally identifiable information (PII), secrets, internal IDs, and account numbers that are returned unnecessarily. The goal is to validate response filtering, field-level authorization, and safe defaults for serialization as described the OWASP risk API3:2023 Broken Object Property Level Authorization (BOPLA).

.svg)