Bot & Abuse Protection
Stop bots, malicious automation, and abuses that target your applications, leading to business logic manipulation, account takeovers, and transaction fraud.
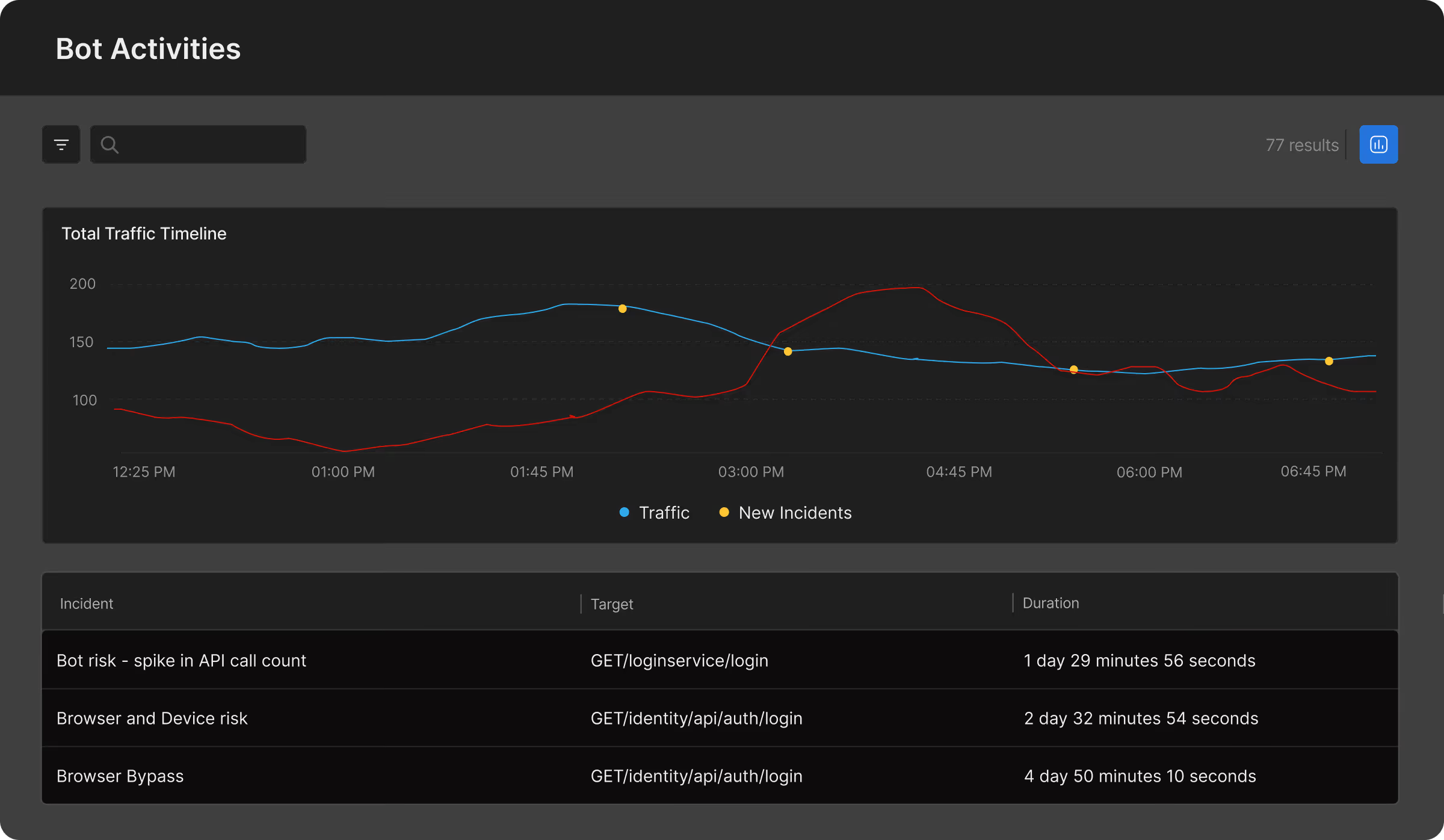
Full Awareness Into Bot Threats
Monitor automated threats that are targeting your applications, analyze traffic patterns, and validate control efficacy across environments.
AI-Assisted Incident Forensics
Use AI-Generated Insights to diagnose how your APIs are being targeted and how it compares to baselines.
Tune Effectively with AI
Ensure that future bot threats and abuses are prevented using an AI-powered policy engine to mitigate attacks without the guesswork.

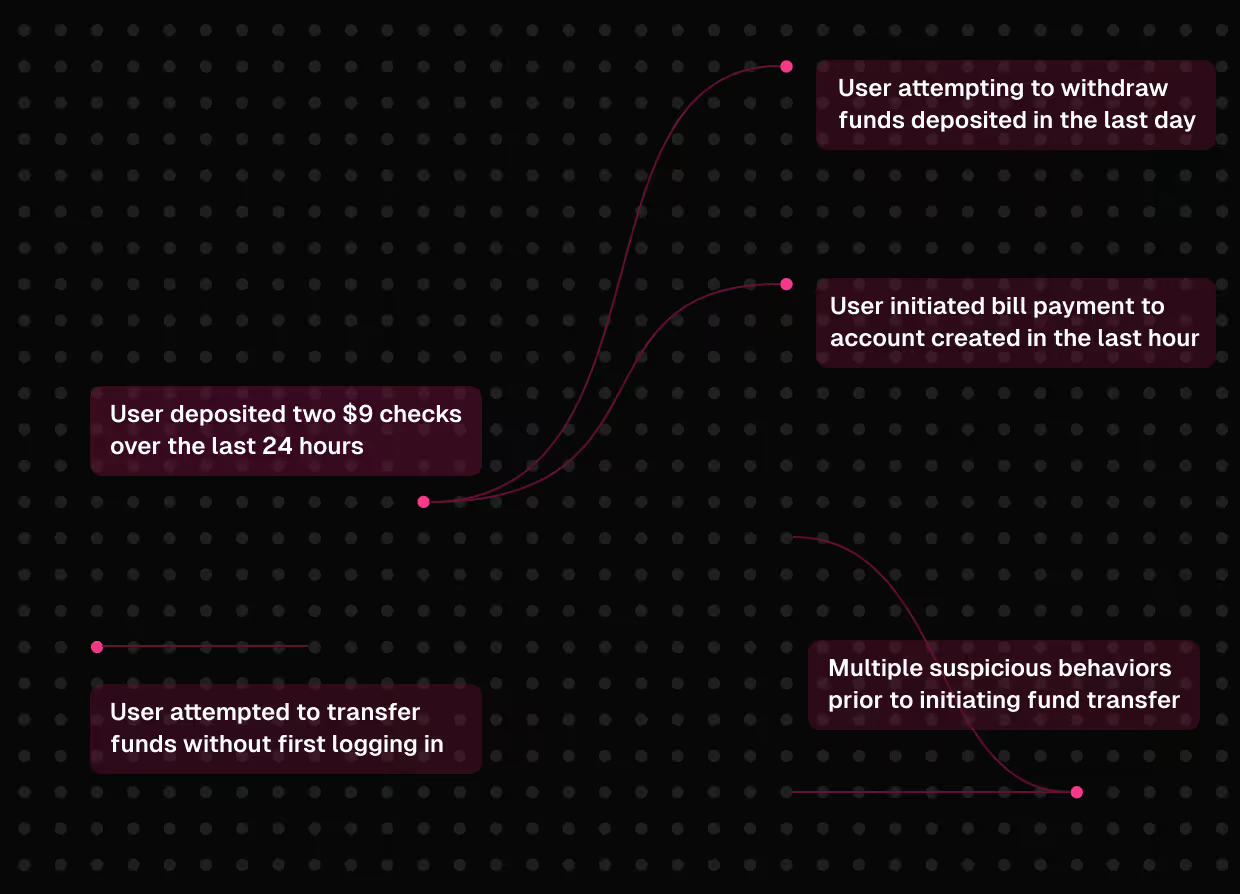
Detect When Intent Turns Malicious
Map User Behaviors
Translate user journeys based on the chains of API calls used to power functionality and data access.
Explainability with AI-Driven Insights
Normal API flows and attack sequences blend together. Harness explains patterns in natural language so you can understand why sets of actions are abnormal.
Stitch Service Calls for the Full Picture
Understand API call chains for first- and third-party services, including cloud, AI/ML, GenAI, and data storage services.
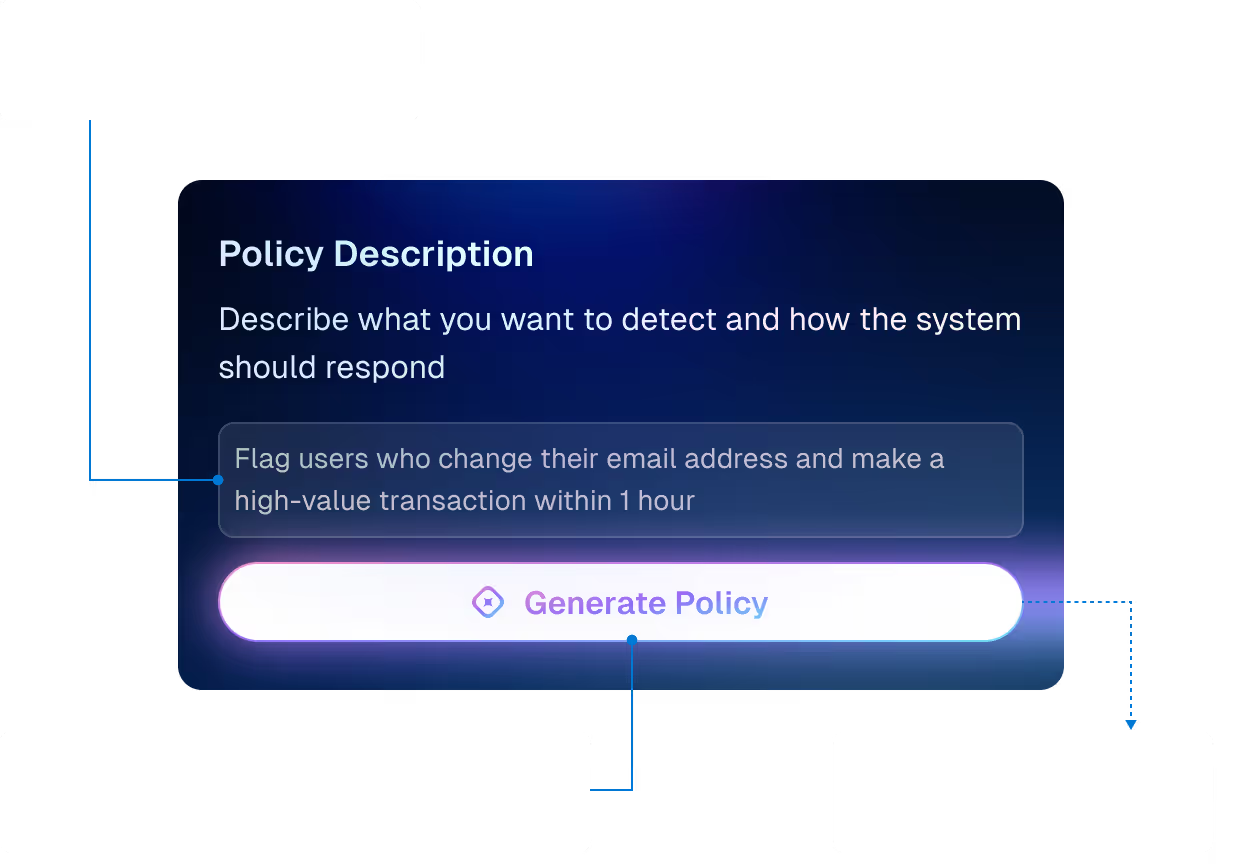
Contain Abuse Using AI Insights
Quickly Identify What Elements Inform Business Logic
Find vulnerable and abuse-prone logic and correlate to the APIs and infrastructure that power it so you can prioritize controls
Stop Abuse Before It Becomes a Breach
Use AI-powered policy guidance to prevent well-crafted, "low & slow" attacks that evade traditional controls where rules are broad
Mitigate Industry-Specific Abuse Patterns
Harness contextualizes recommendations specific to your business logic to protect applications and data effectively
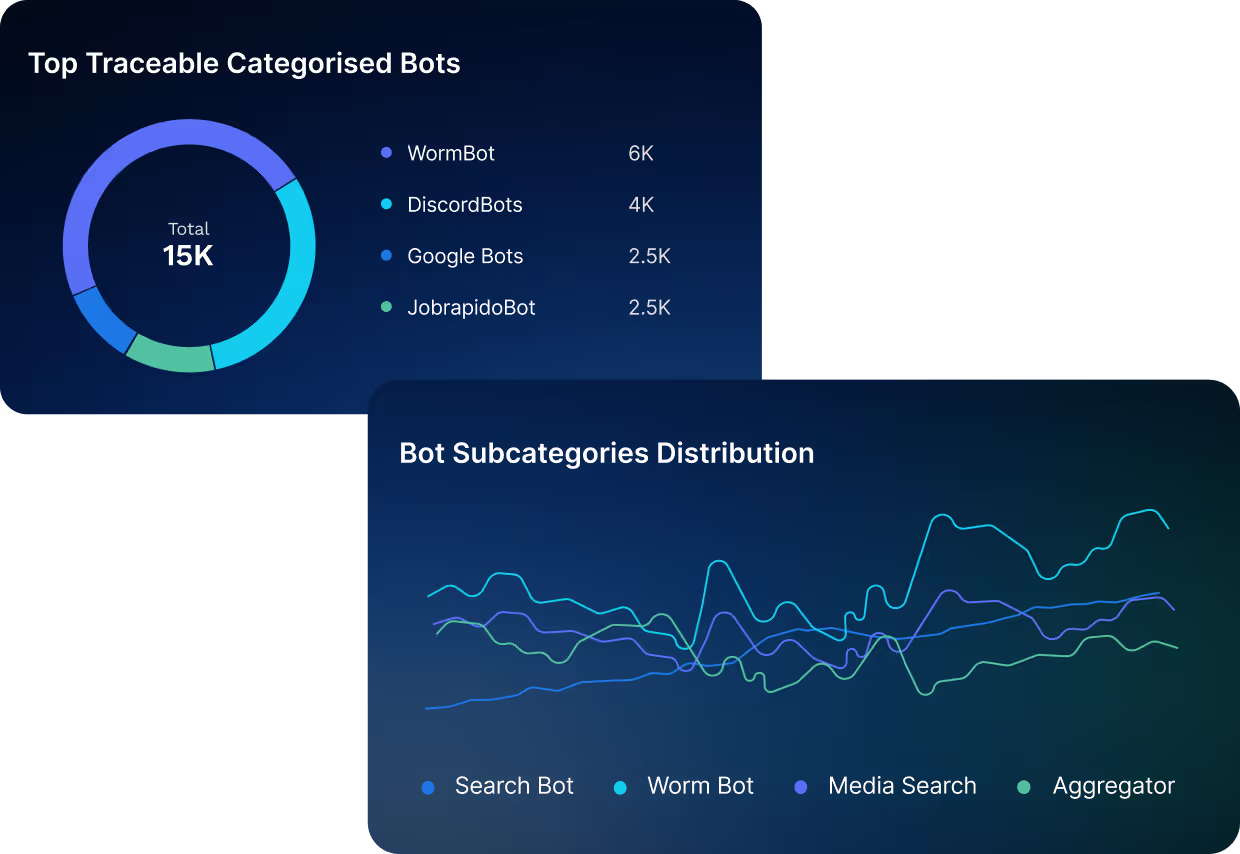
Stop Bots From Damaging Your Business
Identify and Prevent Bot Attacks
Prevent abuse cases such as scraping and resource drain by blocking or rate-limiting bots in real time.
Discern Humans from Machines
Harness distinguishes between "normal" usage and automated threats by analyzing full session lifecycles continuously.
Preserve User Experience
Protect customer experience, data integrity, and backend systems from malicious automation with a balanced mix of blocks, limits, and CAPTCHAs.

Security for Everything in Runtime
The Harness platform informs with API context, identifies sensitive data flows, protects against application-layer attacks, and guides on the best mix of protective controls to stop application abuse.
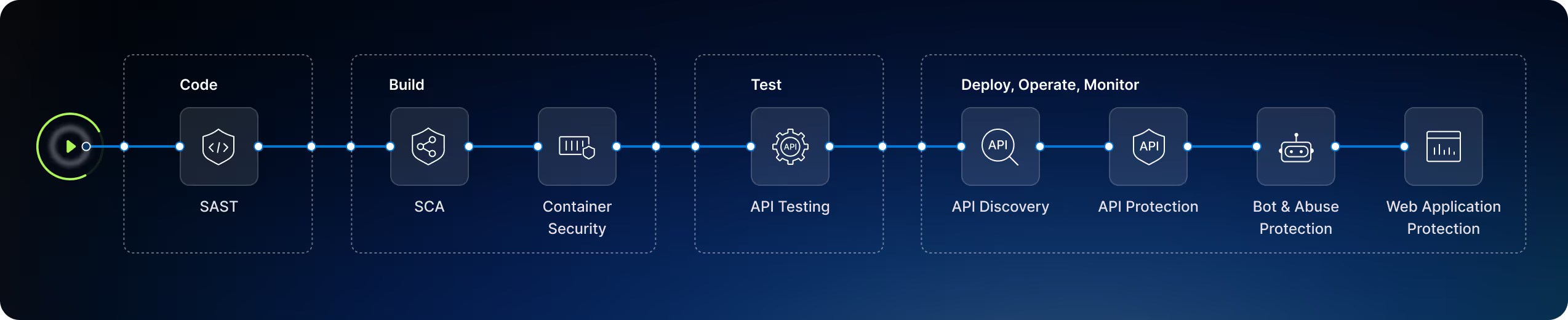
API Discovery
Automatically discover and catalog APIs and gain visibility into your real application attack surface.
API Protection
Protect your APIs with advanced, unified security and defend against evolving threats across hybrid- and multi-cloud environments.
Web Application Firewall
API-first WAF with flexible deployment, coverage for all OWASP Top 10 risks, false positive reduction with API context, and full telemetry to aid SecOps.
Frequently Asked Questions
What is bot detection?
Bot detection is the process of identifying automated traffic across web, mobile, and API endpoints using application telemetry and API signals like behavior, device fingerprinting, and network reputation to stop malicious automation. Distinguishing "good bots" from "bad bots" is often a moving target, varying per industry and business. Continuous signal gathering and intent analysis is needed to fully address the problem.

What is bot management or bot protection?
Bot management, also sometimes referred to as bot protection, combines bot detection and bot mitigation techniques such as explicit block, step-up authentication, dynamic rate limits, or bot challenges while still allowing legitimate users and approved bots like search crawlers or trusted partner integrations.

What is business logic abuse protection?
Business logic abuse protection prevents automated abuse that targets how an application works, primarily through APIs. Frequently targeted functions include login, password resets, change password, account signups, checkout, search, and digital promotion API flows. Attackers exploit APIs and API flows even when no traditional vulnerabilities and misconfigurations are present, making business logic abuse protection is so crucial.

How do bot attacks cause account takeover (ATO)?
Bots, or attackers using automation, perpetuate account takeover by automating other techniques like credential stuffing, password spraying, and bruteforcing scale. In the case of credentials, attackers often use stolen credentials that have been harvested from other breaches, or they may use other intelligence as a starting point such as social media data. Bots and attacker automations also rotate IPs to evade traditional, basic security controls like IP address block lists and static rate limits.

What is credential stuffing and how do you stop it?
Credential stuffing is an automated abuse technique that targets login flows using leaked or breached authentication material, typically username (or email) and password pairs, across sites. Stopping credential stuffing typically requires bot detection, anomaly-based login protection, and step-up authentication for high-risk or privileged sessions.

Is CAPTCHA sufficient for bot protection?
CAPTCHAs alone are not enough because advanced bots and attackers can bypass CAPTCHAs, outsource CAPTCHA solving to human (mechanical turk) services, or mimic real user behavior. CAPTCHAs can damage user experience if not implemented properly, or they rely on client fingerprinting and tracking that raises privacy concerns. Interactive or gamified CAPTCHAs have also emerged, but they can be expensive and still result in abandoned user journeys and transactions. Effective bot protection uses layered detection and adaptive mitigation to preserve user experience and still combat bots & abuse.

How do you protect APIs from automated abuse?
API bot & abuse protection pairs API abuse detection with rate limiting, token integrity, anomaly detection, intent analysis, and automated attack fingerprinting to stop scraping, credential attacks, transaction fraud, and high-volume API abuse.

How do you reduce false positives in bot detection?
Reducing false positives requires accurate classification of "good" bots (or behaviors/intent) vs "bad" bots, tuning protection policies by API endpoint, and using adaptive bot mitigations so legitimate users aren’t blocked during traffic spikes that may occur normally, such as with market seasonality or product launches. Traditional "false positive" metrics sometimes need to be scrutinized, and organizations may prefer other ROI or fraud measurements. Example metrics include transaction fraud rates, chargeback percentages, infrastructure costs incurred, conversion rates, and support incident rates from account compromises or abuse.

What is web scraping and how do you prevent it?
Web scraping or content scraping is automated data extraction from websites commonly but also APIs that serve data. Scraping prevention uses bot detection, intent analysis & controls, and adaptive challenges to block undesirable scraping while still allowing legitimate access such as search engine crawling, AI/LLM crawling, or trusted partner/supplier automations. Organizations in specific industries or regions may also want to block even these legitimate use cases or specific providers to preserve intellectual property or privacy, making the good vs. bad bot argument more complex than it seems.


.svg)