API Discovery
Automatically discover and catalog APIs and sensitive data flows. Gain visibility into your real application attack surface.
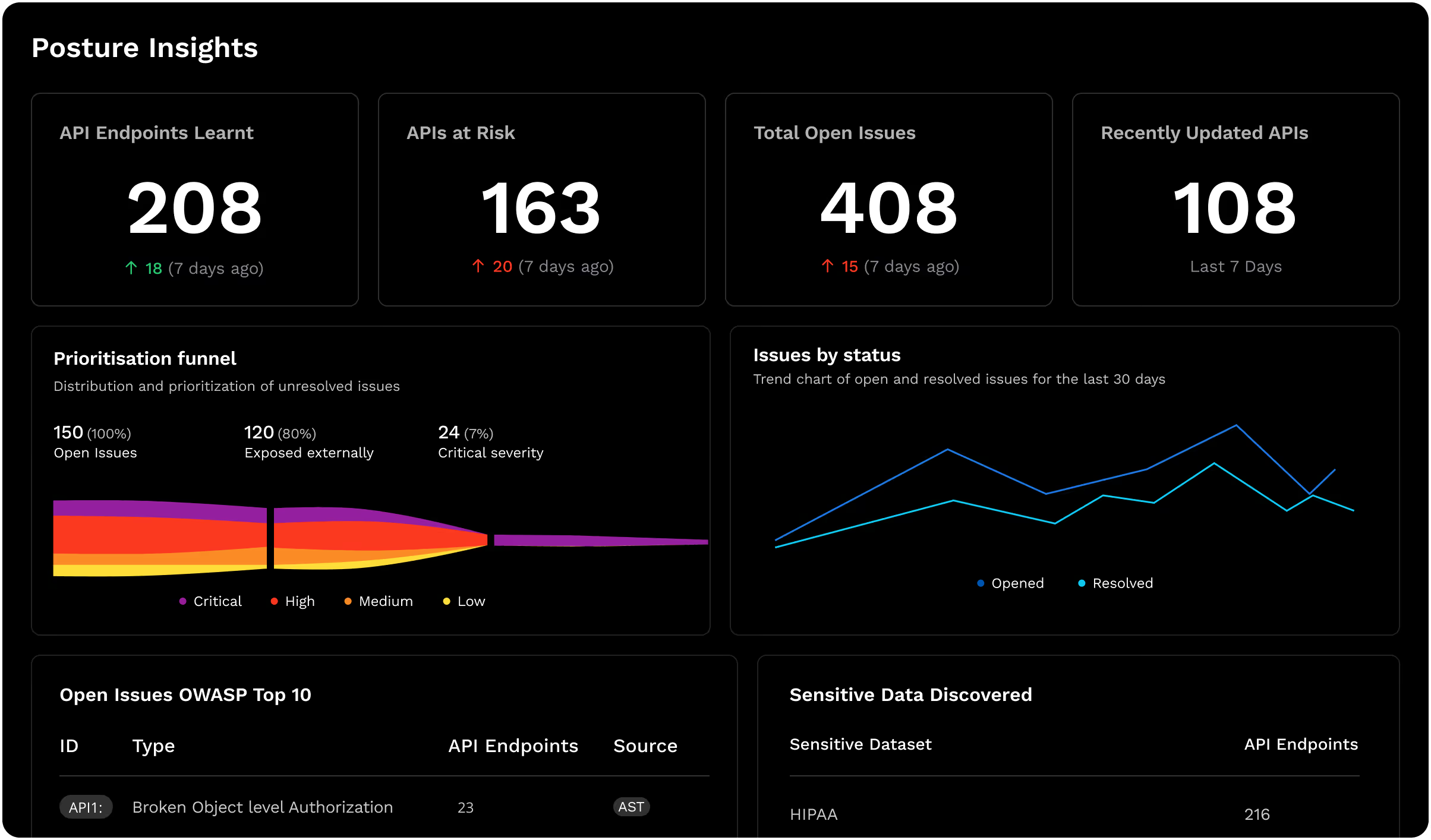
Continuously Inventory APIs
Continuously discover and inventory all of your APIs in a data-rich catalog for complete visibility into your digital estate.
Gain AI Insights on API Risks
Ask Harness AI for contextualized insights on vulnerabilities, access control gaps, and data exposures to proactively manage risk.
Uncover Sensitive Data Exposures
Analyze API data flows and classify sensitive data so you can ensure your most critical data is protected with appropriate controls.
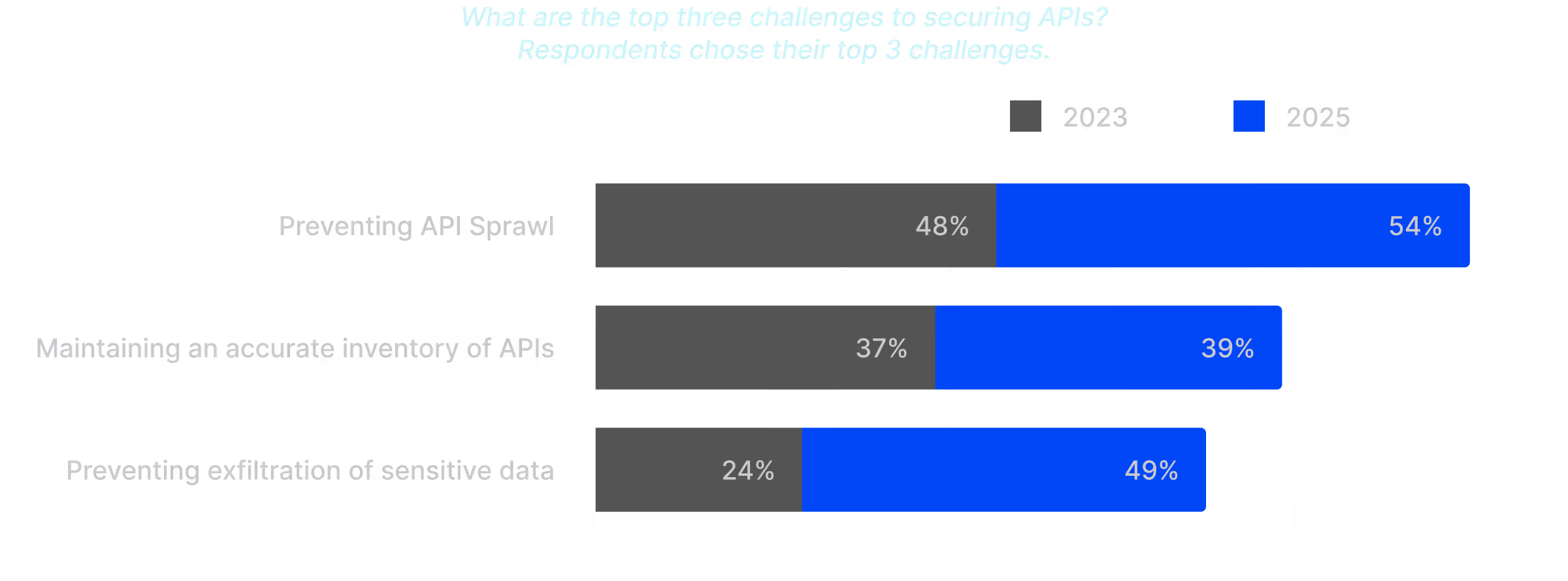
API Sprawl Creates Security Gaps
As API ecosystems grow past hundreds or even thousands, preventing sprawl and maintaining accurate inventories has become not just a priority—but a necessity for survival. – Harness 2025 Global State of API Security Report
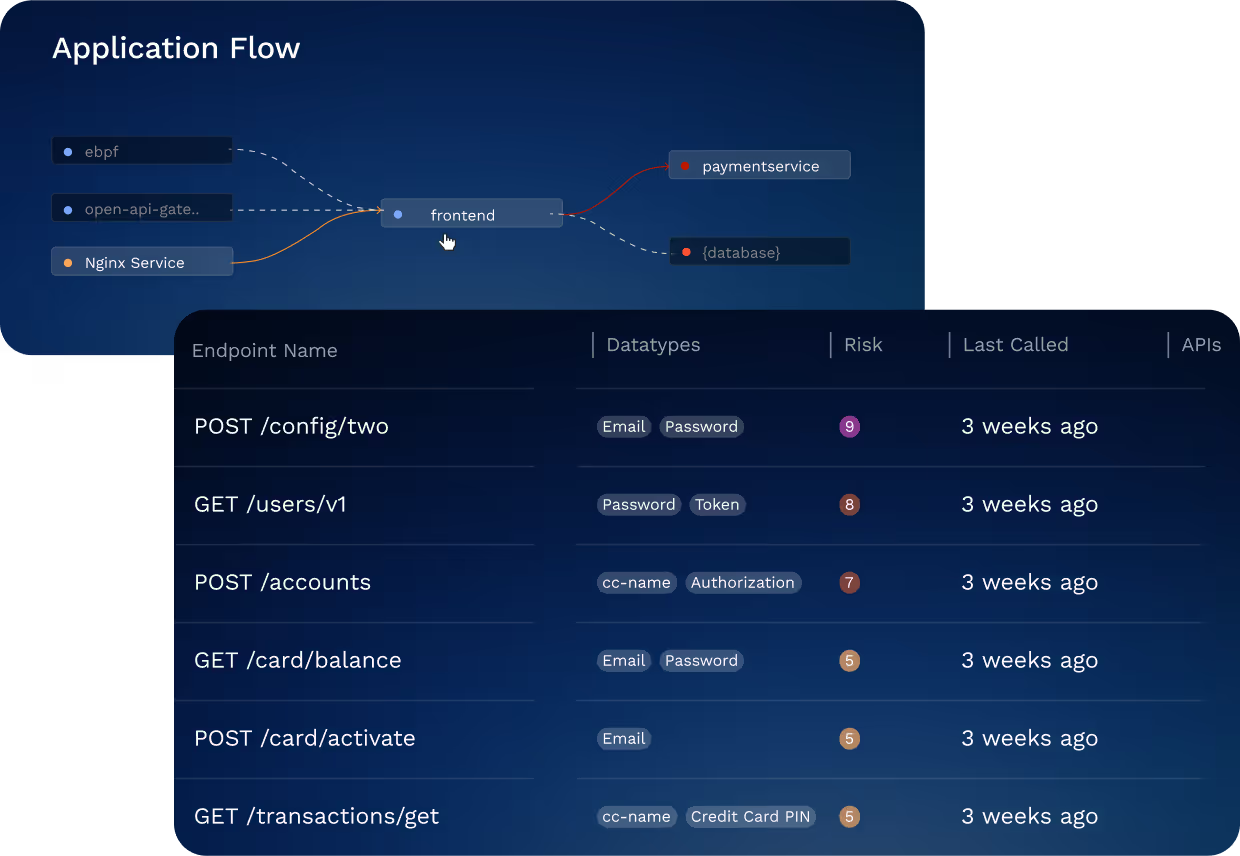
Get Ahead of API Sprawl
Identify APIs from Traffic
Modern system architectures use distributed, evolving API ecosystems. Harness analyzes API signals and mitigates the impacts of sprawl by maintaining accurate API inventories.
Inventory First- and Third-Party APIs
Generate accurate API inventory of all internal and external APIs across all environments. Be audit-ready, understand third-party risk, and power API governance with Harness API Discovery.
Find Shadow and Zombie APIs
Discover unknown and abandoned APIs that result from rapid prototyping, M&A, and missed documentation.
Discover APIs Everywhere
Harness API Discovery works at edge and in-line with API gateway integrations and eBPF agents for distributed workloads
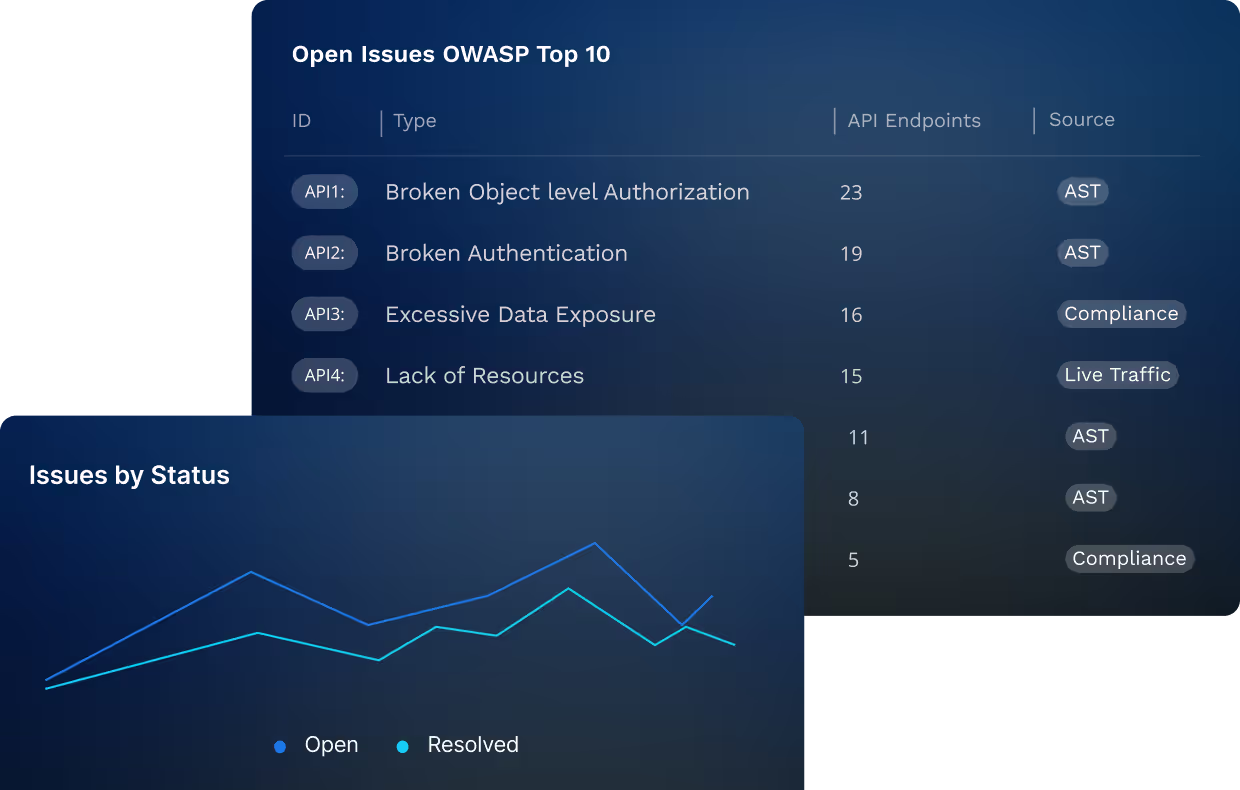
Assess Your Real Application RIsk
Identify Policy Violations
Categorize by OWASP API Top 10 risks, industry standards, and regulatory requirements such as GDPR, HIPAA, PCI-DSS and more.
Automatically Prioritize API Risks
Prioritize API issues automatically based on risk severity, exposure, and business impact.
Strengthen Your API Security Posture
Integrate with developer experience tools like Harness IDP so teams know which APIs are safe, or connect to other tools like Jira and ServiceNow to improve vulnerability remediation tracking.
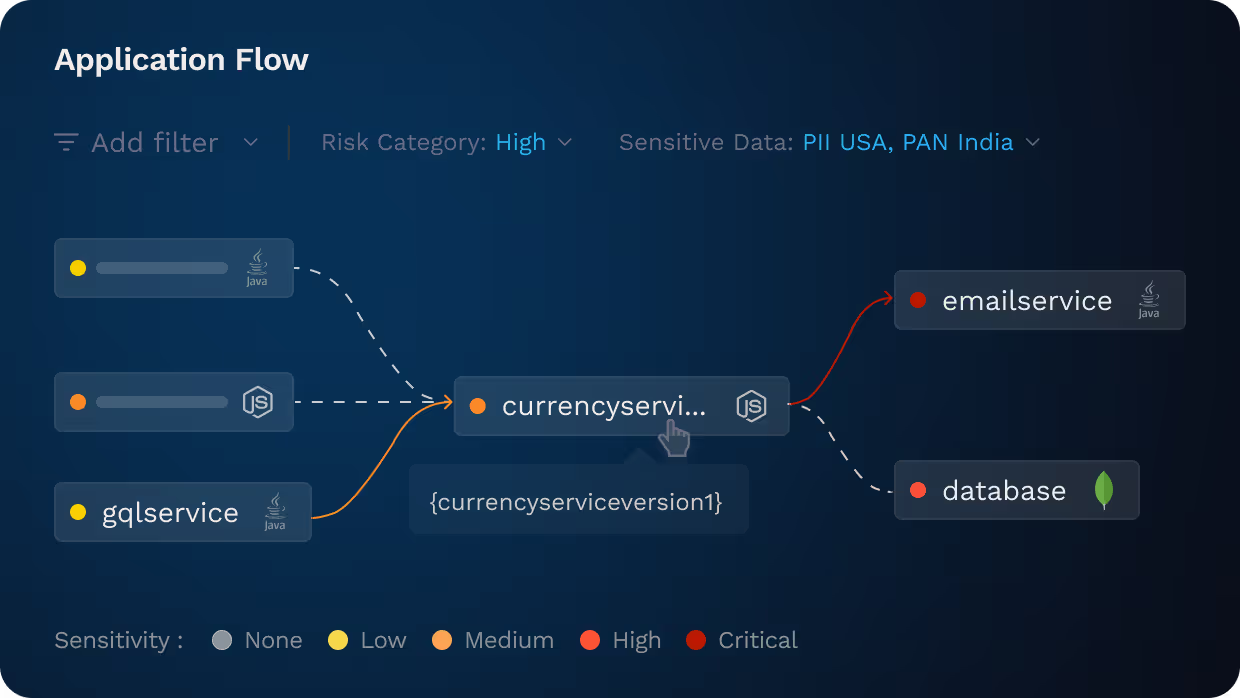
Know Where Sensitive Data Moves
Find Sensitive Data Exposure
Continuously identify data handled by API endpoints and classify what sensitive data is exposed.
Focus Your Data Security Efforts
Prioritize which of your applications need greater security controls to protect sensitive data and intellectual property.
Identify Access Control Gaps
Data flows help define appropriate access controls. Identify API endpoints that handle sensitive data and where authentication or authorization are lacking.

Security for Everything in Runtime
The Harness platform informs with API context, identifies sensitive data flows, protects against application-layer attacks, and guides on the best mix of protective controls to stop application abuse.
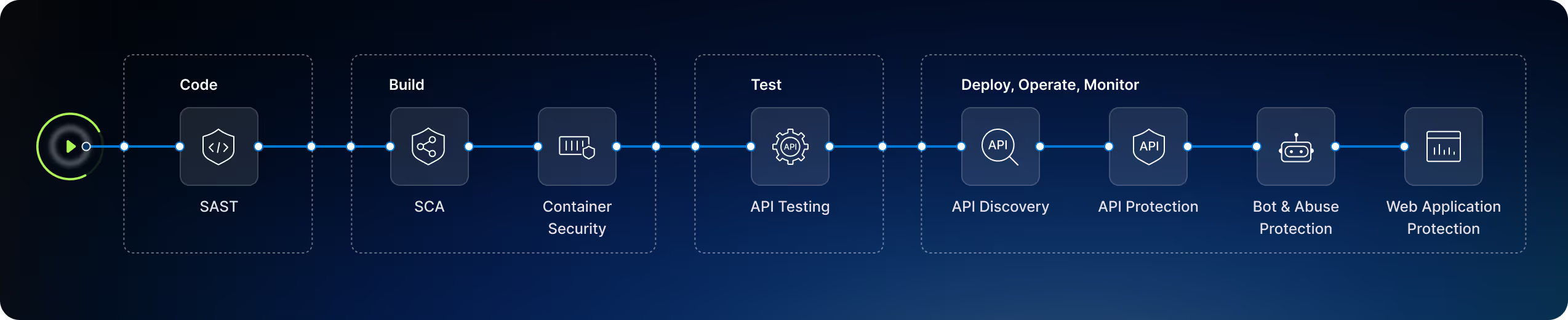
API Testing
Find and eliminate API vulnerabilities with continuous scanning and contextualized remediation, without slowing development or release.
API Protection
Protect your APIs with advanced, unified security and defend against evolving threats across hybrid- and multi-cloud environments.
Bot & Abuse Protection
Mitigate bot attacks and API abuses that result in transaction fraud, data exposure, and business logic manipulation.
Frequently Asked Questions
What is API discovery?
API discovery involves identifying and cataloging all APIs running in all your environments to create a complete, accurate, and current API inventory. Discovery should encompass internal, private cloud, public cloud, and third-party APIs.

What’s the difference between API discovery and an API inventory?
API discovery finds APIs, ideally done continuously as APIs evolve or new endpoints manifest. API inventory, sometimes referred to as API catalog, is the maintained record of what’s been discovered that includes endpoints (or URLs), owners, versions, environments, and risk context.

Why is API discovery important for security?
API discovery helps reduce risk by uncovering unknown (shadow), unmanaged, and exposed APIs that are frequent attack vectors to abuse functionality or exfiltrate data. Security teams use API inventory to gain visibility into the attack surface, employ security monitoring, and implement protective controls.

What are zombie APIs?
Zombie APIs are endpoints that have been deprecated or endpoints thought to be retired that still exist in running systems. Zombie APIs incease exposure and are often easy targets because they’re typically unmonitored, unmaintained, and unhardened.

What are shadow APIs?
Shadow APIs are undocumented or unknown APIs running without central visibility. They commonly arise from third-party procurement, rapid development without documentation, and lack of API management.

How do you discover APIs that aren’t documented with OpenAPI or Swagger?
While API specifications can be useful metadata, application teams don't always produce or maintain them. API discovery tools combine traffic-based discovery from multiple points of architecture including API gateways, perimeter proxies, WAFs, and Kubernetes clusters with additional analysis to reveal API metadata not present in API specs.

How do you discover APIs within microservices architectures (MSA) and Kubernetes clusters?
API discovery in microservices and Kubernetes relies on telemetry gathered from ingress controllers, API gateways, sidecars, and agents (like eBPF) within running workloads to map inner service calls and external API endpoints.

How do you discover APIs in AWS, Azure, or Google Cloud?
API discovery uses cloud-native signals from cloud architectural elements such as application load balancers, API gateways, logs, and mirrored traffic to construct and maintain API inventory across cloud tenants in providers like AWS, Azure, and GCP.

How do you maintain an accurate API catalog?
API catalogs are often static, informed by API management tools, or exist within developer experience platforms. Continuous API discovery is a powerful complement that can enrich the catalog with the actual evironmental configuration, data classifications, and relative secruity risk so development teams source functionally-appropriate and secure APIs.

How do you risk-prioritize discovered APIs?
Prioritize based on network placement (public cloud, private cloud, internal, third-party SaaS, partner integrations), sensitive data handled, authentication and authorization in place, Internet reachability, and usage levels. API discovery tools aid in this data collection and analysis so you can focus testing and protection on the riskiest endpoints.


.svg)