Web Application Firewall
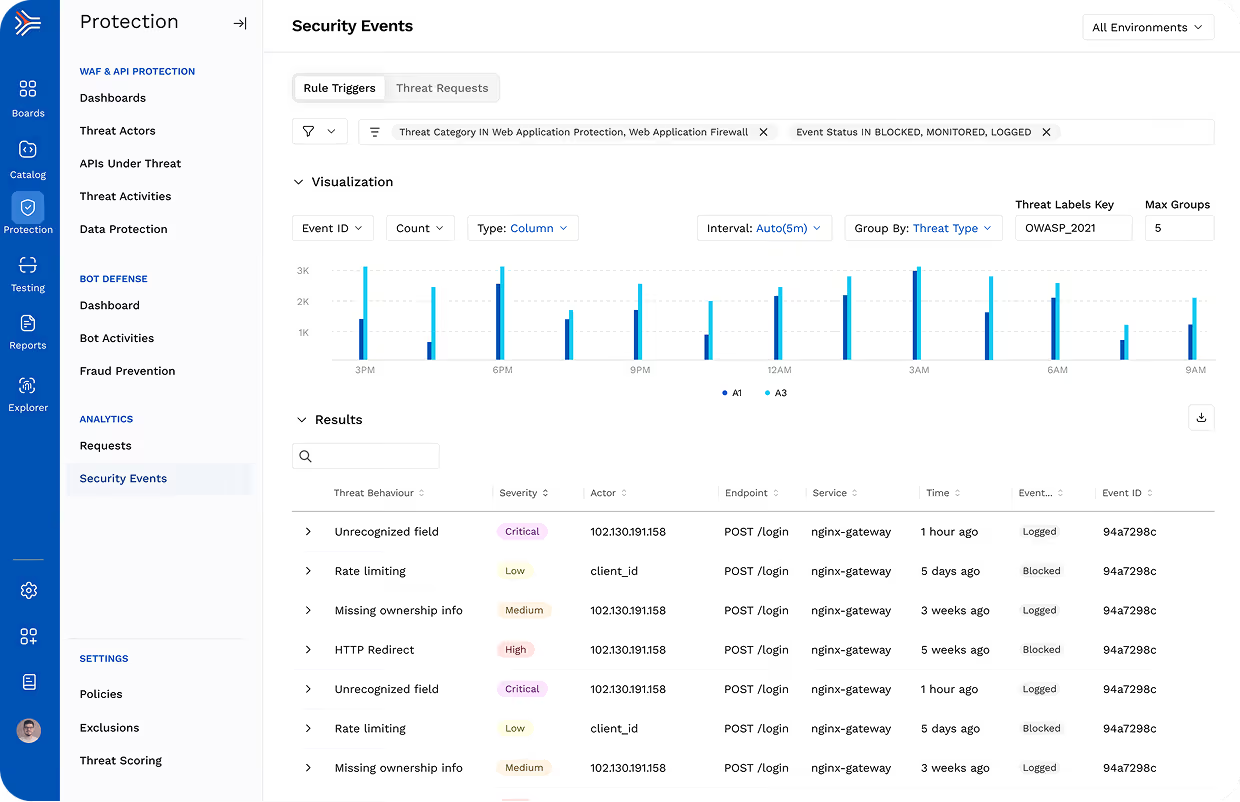
Protect your web applications with cloud-scale, API-centric security that detects and blocks the full spectrum of application attacks and OWASP Top 10 risks, while tuning continuously for your environments.
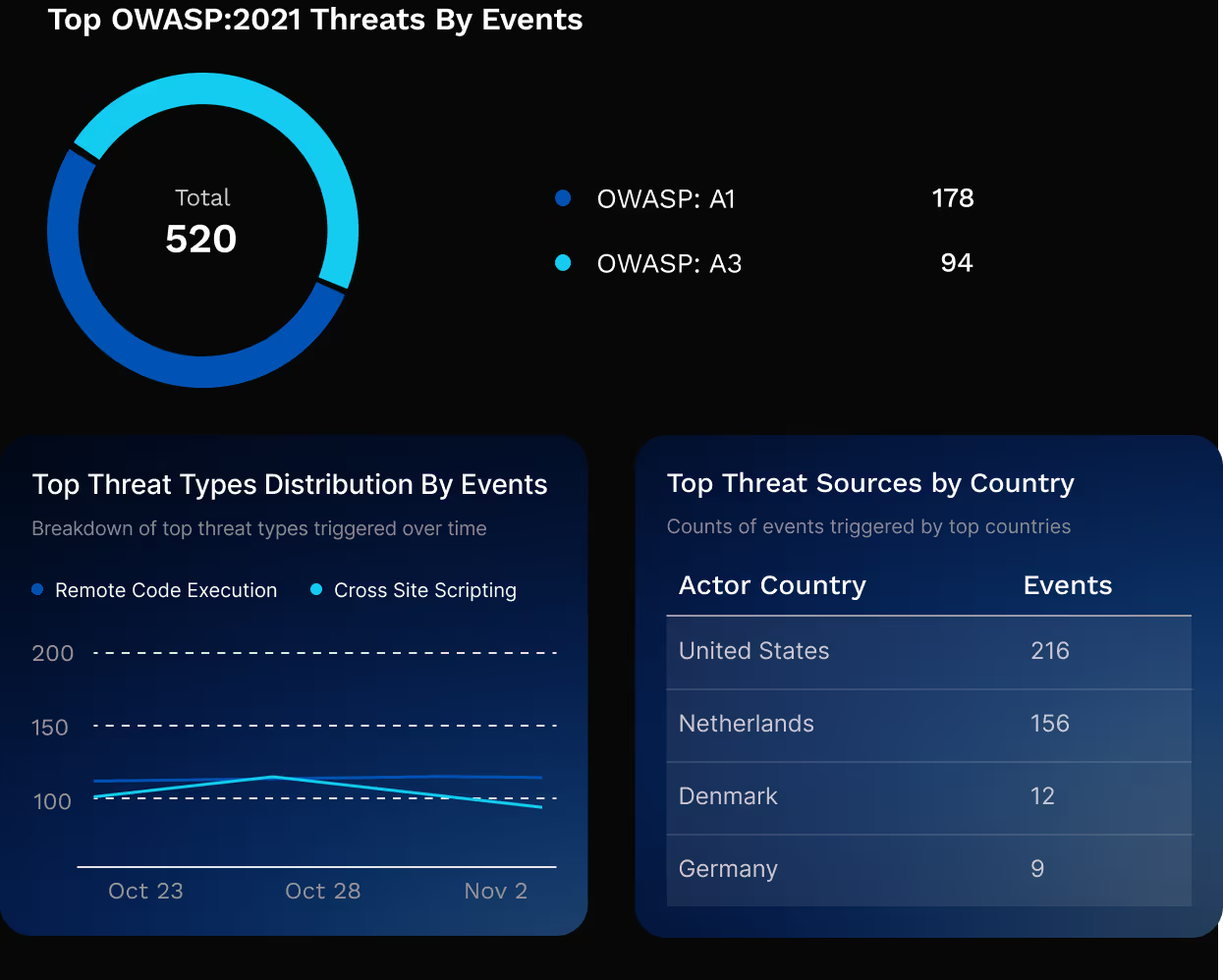
Full OWASP Top 10 Coverage
Harness WAF covers all of the OWASP Top 10 risks and can extend into API security and AI security when you are ready.
Deploy with Flexibility
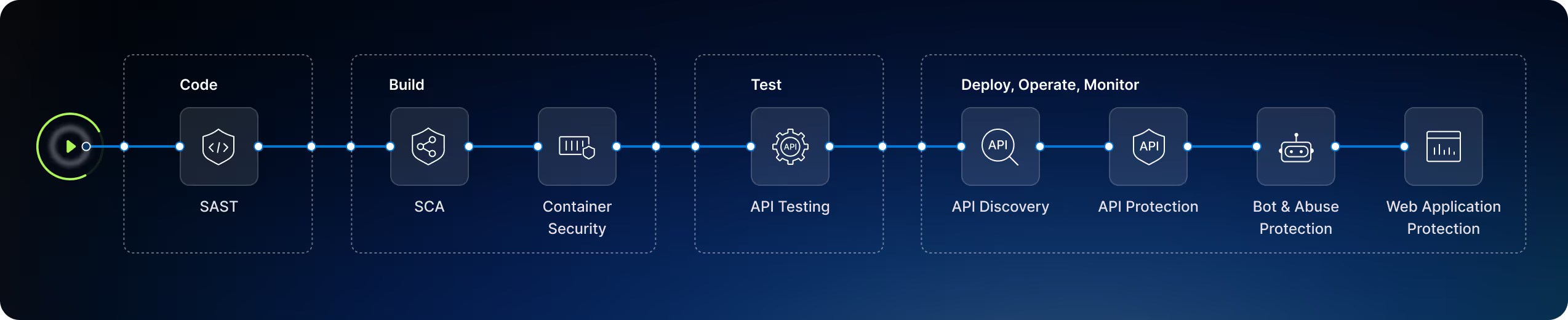
Minimize DevOps friction deploying at edge, or use Harness as internal protection for advanced threats. The choice is yours, based on your architecture.
Protect APIs and Apps
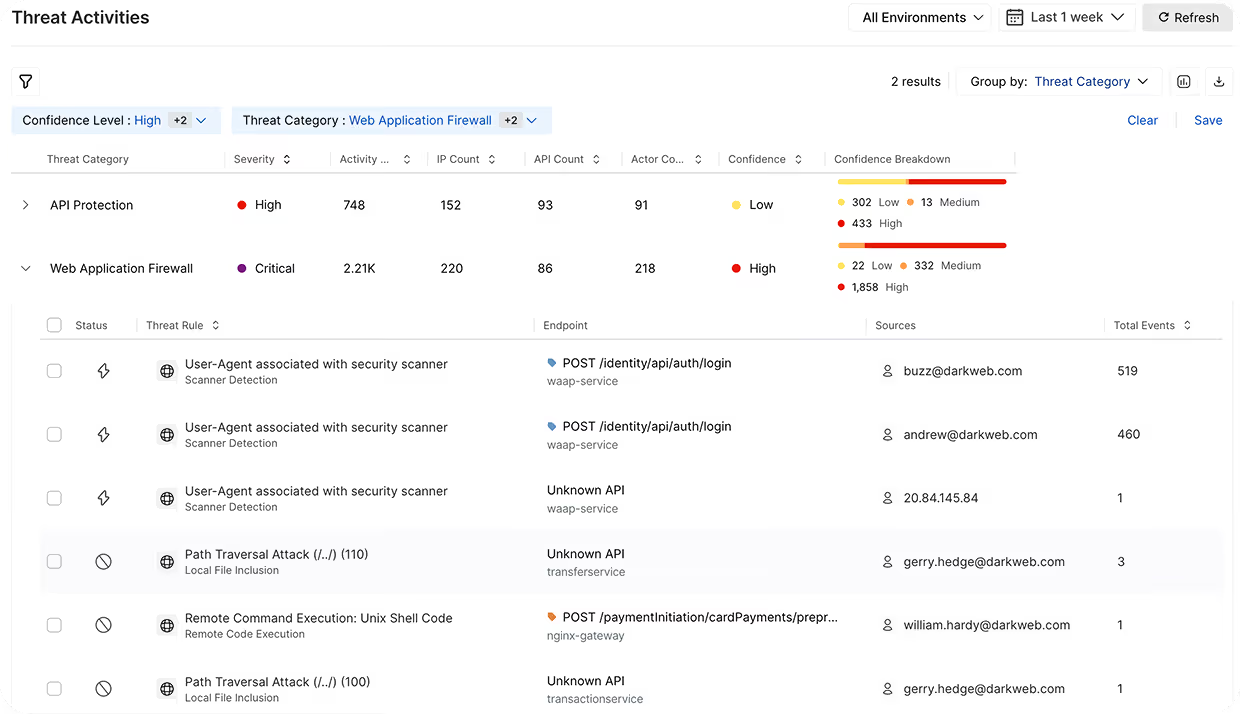
Harness WAF inspects all application and API traffic, not just legacy technology. Modernize your WAF deployment for real-world designs.


.svg)