API Protection
Protect your APIs with advanced, unified security and defend against evolving threats across hybrid- and multi-cloud environments.
Prevent Downtime and Data Loss
Protect apps and APIs from OWASP Top 10 risks, DDoS attacks, data exposure, and more with full application runtime security in a single platform.
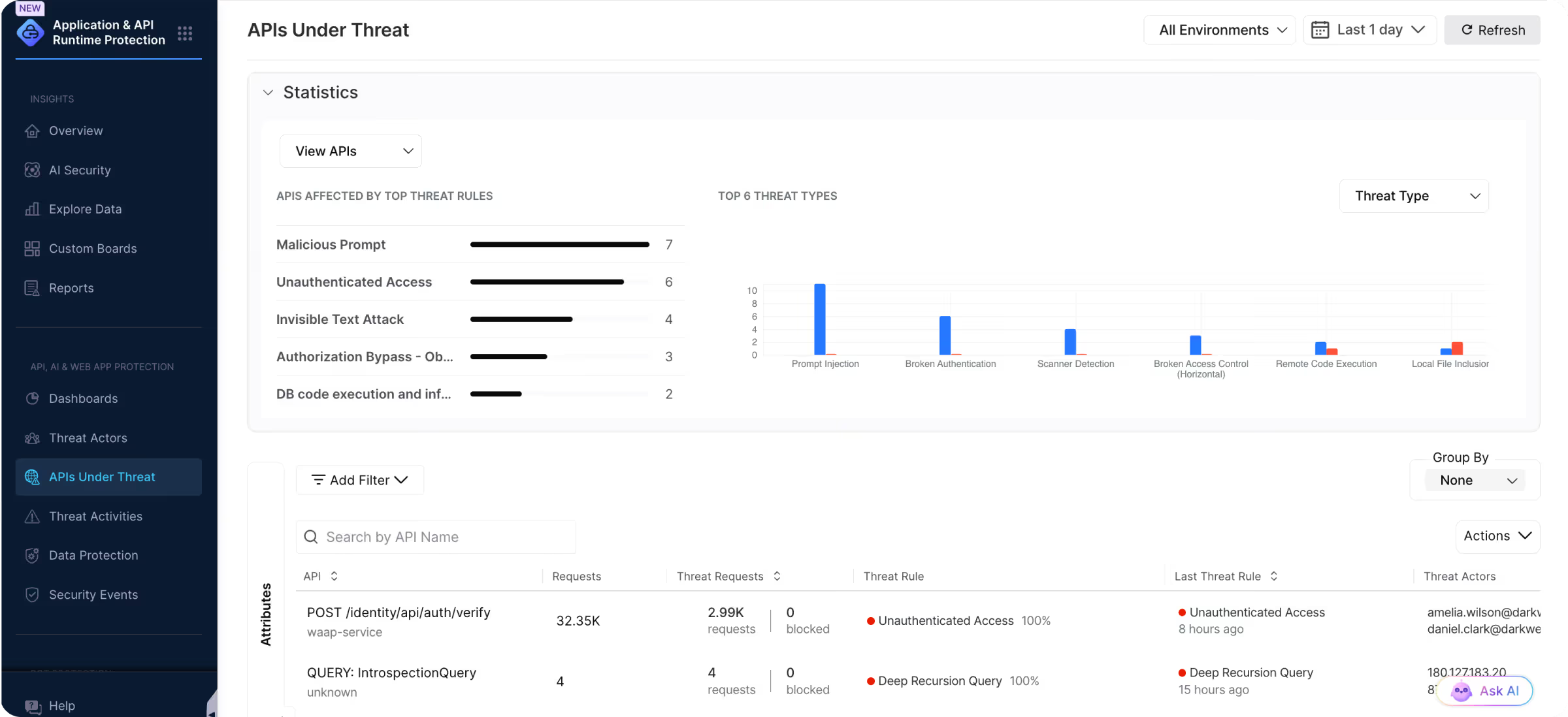
Catch API Attacks Instantly
Monitor threat activity in real-time to detect access control bypasses, data exfiltration, and other API threats and quickly contain impacts.
AI-Assisted Threat Analysis
Dive into specific threats targeting your systems. AI Generated Insight fills in the blanks on what happened, what was impacted, and how to resolve.

Safeguard Your API Endpoints and Flows
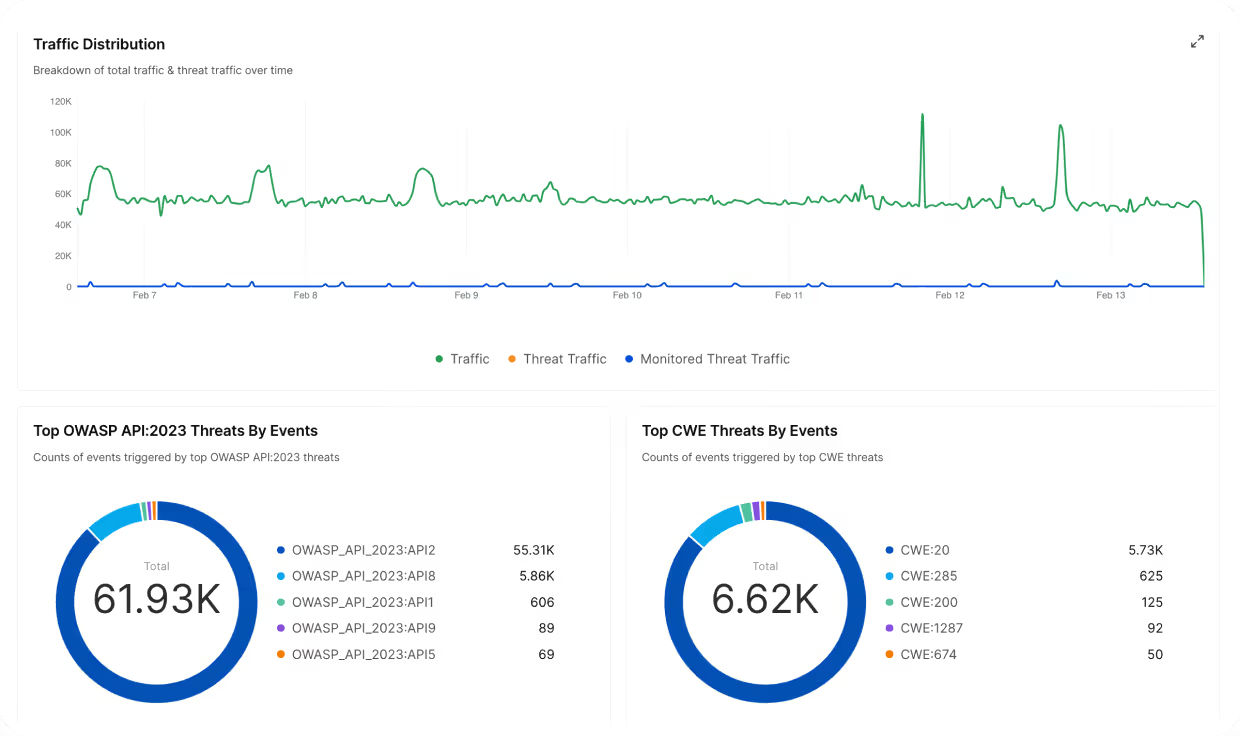
Protect Based on API Insights
Gain real-time insight into every API request and response flowing through your applications and systems.
Map Your Digital Footprint
Harness provides a complete picture of your application environments and sensitive data transmission.
Defend APIs Where They Run
Harness aggregates signals from multiple points of architecture and provides flexible integration to uncover APIs.
Address Third-Party Risk
Harness maps all API calls, including data flows to external partners and suppliers so you can validate appropriate access.
Proactively Detect Attacks
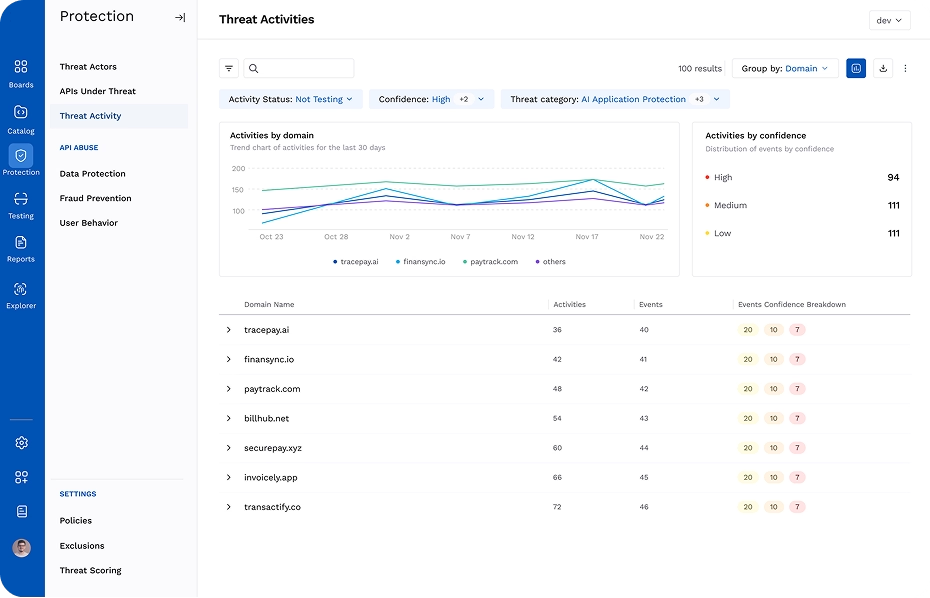
Quickly Identify Threats
Uncover API attacks using signals correlated in Harness's data lake, before damage is done or a breach occurs.
Uncover API Anomalies
Harness inspects and retains full API requests and responses to uncover anomalies, data leaks, and suspicious patterns.
AI/ML-Based Detection
Harness uses advanced AI/ML that continuously evolves to detect zero-days, access control bypasses, logic abuse, and other malicious behaviors with high accuracy and minimal noise.
Block Threats with Precision
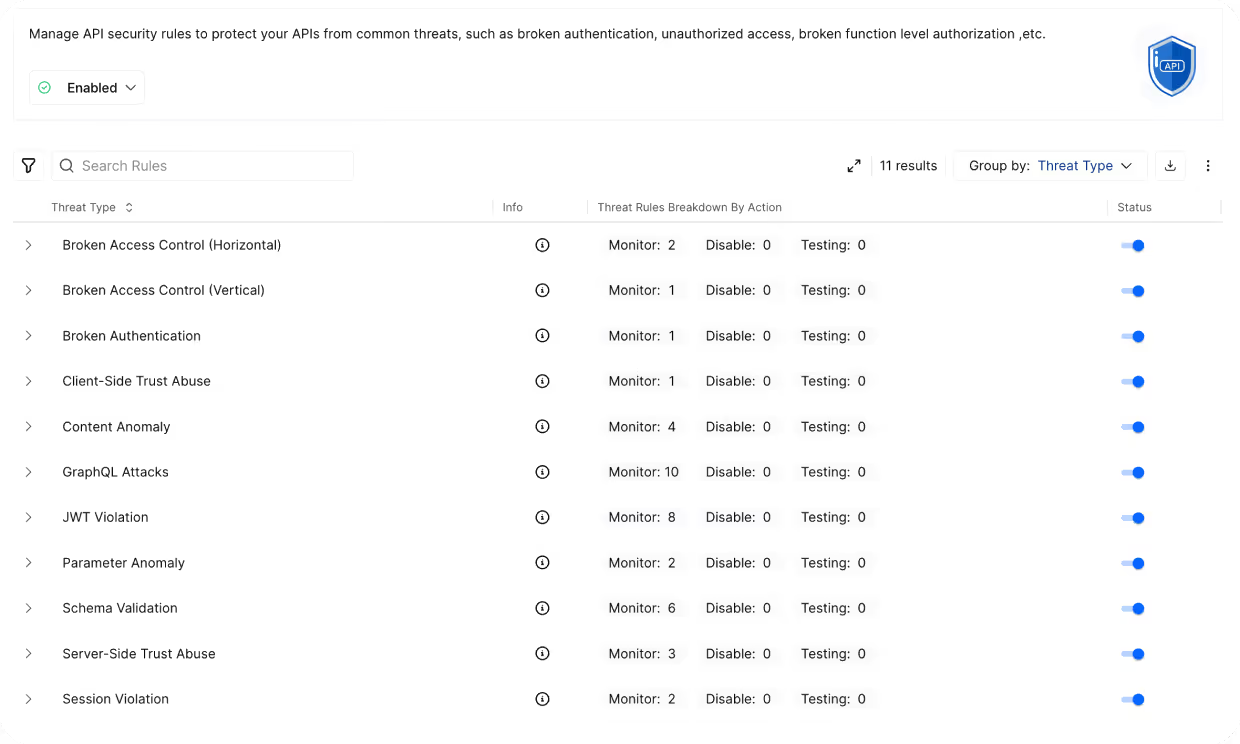
Defend Where You Need It
Harness offers deployment flexibility to ensure full API coverage without disrupting performance or architecture. Threats are blocked in real time based on precise detection signatures.
Augment API Management
Harness offers integration with API management and API gateways so you can mediate APIs with enterprise-grade application runtime security.
Protect Quickly from Edge
Harness deploys quickly with SaaS or edge delivery, complementary to your existing cloud and CDN implementations.
Deploy In-line for Advanced Threats
Deploy additional in-line agents for even greater protection for microservices and inner service threats.

Security for Everything in Runtime
The Harness platform informs with API context, identifies sensitive data flows, protects against application-layer attacks, and guides on the best mix of protective controls to stop application abuse.
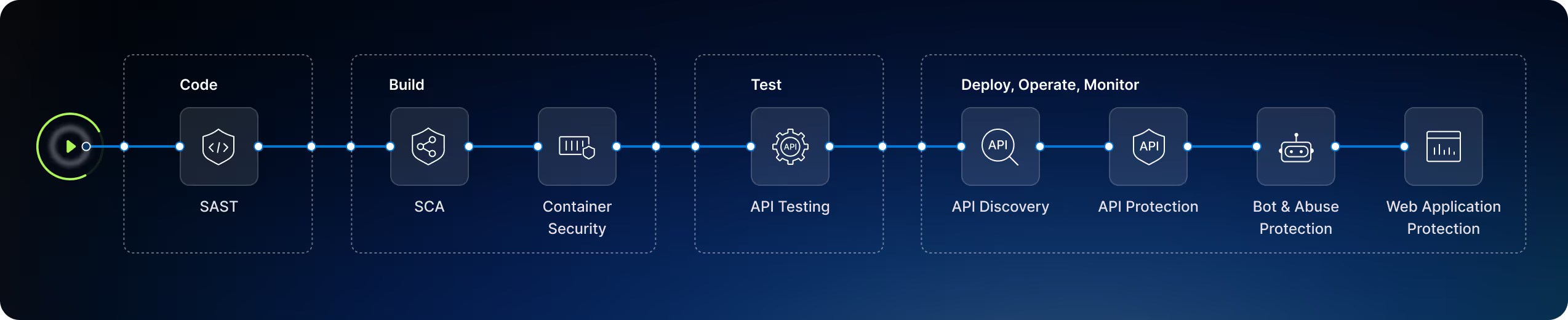
API Discovery
Automatically discover and catalog APIs and gain visibility into your real application attack surface.
API Testing
Find and eliminate API vulnerabilities with continuous scanning and contextualized remediation, without slowing development or release.
Web Application Firewall
API-first WAF with flexible deployment, coverage for all OWASP Top 10 risks, false positive reduction with API context, and full telemetry to aid SecOps.
Frequently Asked Questions
What is API protection?
API protection is the set of controls used to prevent, detect, and block API security threats like unauthorized access, authentication bypass, data exposure, and misconfiguration exploit across your REST, GraphQL, and gRPC endpoints.

How do API security and API protection differ?
API security is used as a general term to describe the overall discipline of securing APIs, which typically includes design review, testing, and API governance. API protection refers to runtime API threat protection or API detection and response, like blocking API attacks, stopping abuse, and continuous monitoring of API traffic.

Why is API protection important for modern designs?
Applications (both web and mobile), system integrations, and AI systems all rely on APIs to facilitate access to data and power functionality. Simply put, without APIs, an application or system doesn't function. Strong API protection reduces risks such as unauthorized access, account takeover (ATO), transaction fraud, and data leakage.

What are the most common API attacks?
Common API attacks include broken object level authorization (BOLA) or insecure direct object reference (IDOR), broken authentication, broken object propery level authorization (BOPLA), broken function level authorization (BFLA), misconfiguration exploitation, unsafe third-party API consumption, injection, and business logic abuse.

What is BOLA (or IDOR) in API security?
Broken object level authorization (BOLA) or insecure direct object reference (IDOR) happens when an API fails to implement appropriate authorization checks throughout an authenticated user session. Identity and access management (IAM) controls are used to authenticate and authorize a user at the initiation of a session, but authorization checks must also be done continuously to avoid situations where a malicious party manipulates APIs calls in order to access another user’s objects or sensitive functionality.

Does rate limiting help with API protection?
API rate limiting can help reduce threats like bruteforcing, scraping, denial-of-service, and credential stuffing if implemented properly. Limits can be set on API request volume per user, token, IP address, or client fingerprint. Static rate limits may work for a time, but organizations typically need dynamic rate limits or must revisit limit policies continuously to address emerging threats or new attack campaigns. Rate limits may also need to be enforced at different ingress/egress points in a given architecture and dependent on API flows.

Does my WAF protect APIs?
A web application firewall (WAF) is useful as a general-purpose application-layer (L7) control. WAFs are ideally suited for protecting web and mobile applications that communicate over HTTP and HTTPS, including client-side application code to server-side backend interactions, typically JavaScript (JS). While APIs often operate using the same standard web protocols, dedicated API protection adds REST/GraphQL awareness, schema validations, and stronger authorization-focused protections. WAFs also don't typically inspect or "understand" API-centric protocols like gRPC common in microservice architectures (MSA).

How do you protect APIs from unauthorized access?
Always use strong API authentication and authorization, powered by community-vetted protocols like OpenID Connect (OIDC) and OAuth 2.0. Emphasize least privilege so users have access to only the data or functionality that's expected in normal user or employee flows. Also use tight scopes, particularly with federated auth and be cautious of redirects. Avoid using weak authentication material like static API keys alone, and pair with additional authentication factors (i.e., 2FA,MFA) for priviliged access. Access control policies must be continuously enforced at gateways and proxies, or even in the application runtime environment.

How do you protect GraphQL APIs?
GraphQL API protection requires query depth limits, complexity limits, schema validations, strict authorization checks, and GraphQL-specific rate limiting to prevent data overfetching or abuse. Attackers may seek to abuse the GraphQL endpoint itself, or they abuse GraphQL as a proxy to backend functionality and data that the GraphQL endpoint aggregates normally.

Does my API gateway protect APIs?
API gateways and API gateways deployed as part of an API Management platform can enforce encrypted transport (e.g., TLS), access control policies, rate limits, usage limits, and intelligent routing. However, runtime API protection is still needed for advanced threat detection, abuse prevention, and full coverage of the OWASP API Security Top 10 risks.


.svg)