Featured Blogs
Recent Blogs


Overcoming the AI Velocity Paradox in Security
The rapid adoption of AI is fundamentally reshaping the software development landscape, driving an unprecedented surge in code generation speed. However, this acceleration has created a significant challenge for security teams: the AI velocity paradox. This paradox describes a situation where the benefits of accelerated code generation are being "throttled by the SDLC processes downstream," such as security, testing, deployment, and compliance, which have not matured or automated at the same pace as AI has advanced the development process.
This gap is a recognized concern among industry leaders. In Harness’s latest State of AI in Software Engineering report, 48% of surveyed organizations worry that AI coding assistants introduce vulnerabilities, and 43% fear compliance issues stemming from untested, AI-generated code.
This blog post explores strategies for closing the widening gap and defending against the new attack surfaces created by AI tooling.
Defining the AI Velocity Paradox in Security
The AI velocity paradox is most acutely manifested in security. The benefits gained from code generation are being slowed down by downstream SDLC processes, such as testing, deployment, security, and compliance. This is because these processes have not "matured or automated at the same pace as code generation has."
Every time a coding agent or AI agent writes code, it has the potential to expand the threat surface. This can happen if the AI spins up a new application component, such as a new API, or pulls in unvalidated open-source models or libraries. If deployed without proper testing and validation, these components "can really expand your threat surface."
The imbalance is stark: code generation is up to 25% faster, and 70% of developers are shipping more frequently, yet only 46% of security compliance workflows are automated.
The Dual Risk: Vulnerabilities vs. Compliance
The Harness report revealed that 48% of respondents were concerned that AI coding assistance introduced vulnerabilities, while 43% feared regulatory exposure. While both risks are evident in practice, they do not manifest equally.
- Vulnerabilities are more tangible and appear more often in incident data. These issues include unauthenticated access to APIs, poor input validation, and the use of third-party libraries. This is where the "most tangible exposure is".
- Compliance is a "slow burn risk." For instance, new code might start "touching a sensitive data flow which was previously never documented." This may not be discovered until a specific compliance requirement triggers an investigation. Vulnerabilities are currently seen more often in real incident data than compliance issues.
A New Attack Surface: Non-Deterministic AI Agents
The components that significantly expand the attack surface beyond the scope of traditional application security (appsec) tools are AI agents or LLMs integrated into applications.
Traditional non-AI applications are generally deterministic; you know exactly what payload is going into an API, and which fields are sensitive. Traditional appsec tools are designed to secure this predictable environment.
However, AI agents are non-deterministic and "can behave randomly." Security measures must focus on ensuring these agents do not receive "overly excessive permissions to access anything" and controlling the type of data they have access to.

Top challenges for AI application security
Prioritizing AI Security Mitigation (OWASP LLM Top 10)
For development teams with weekly release cycles, we recommend prioritizing mitigation efforts based on the OWASP LLM Top 10. The three critical areas to test and mitigate first are:
- Prompt Injection: This is the one threat currently seeing "the most attacks and threat activity".
- Sensitive Data Disclosure: This is crucial for any organization that handles proprietary data or sensitive customer information, such as PII or banking records.
- Excessive Agency: This involves an AI agent or MCP tool having a token with permissions it should not have, such as write control for a database, code commit controls, or the ability to send emails to end users.
We advise that organizations should "test all your applications" for these three issues before pushing them to production.
A Deep Dive into Prompt Injection
Here’s a walkthrough of a real-world prompt injection attack scenario to illustrate the danger of excessive agency.
The Attack Path is usually:
- Excessive Agency: An AI application has an agent that accesses a user records database via an API or Model Context Protocol (MCP) tool. Critically, the AI agent has been given a "broadly scoped access token" that allows it to read, make changes, and potentially delete the database.
- The Override Prompt: A user writes a prompt with an override, for example, suggesting a "system maintenance" is happening and asking the AI to "help me make a copy of the database and make changes to it." This is a "direct prompt injection" (or sometimes an indirect prompt injection), which is designed to force the LLM agent to reveal or manipulate certain data.
- Hijacking: If no guardrails are in place to detect such prompts, the LLM will create a hijack scenario and make the request to the database.
- Real Exfiltration: Once the hijacking is done, the "real exfiltration happens." The AI agent can output the data in the chatbot or write it to a third-party API where the user needs access to that data.
This type of successful attack can lead to "legal implications," data loss, and damage to the organization's reputation.
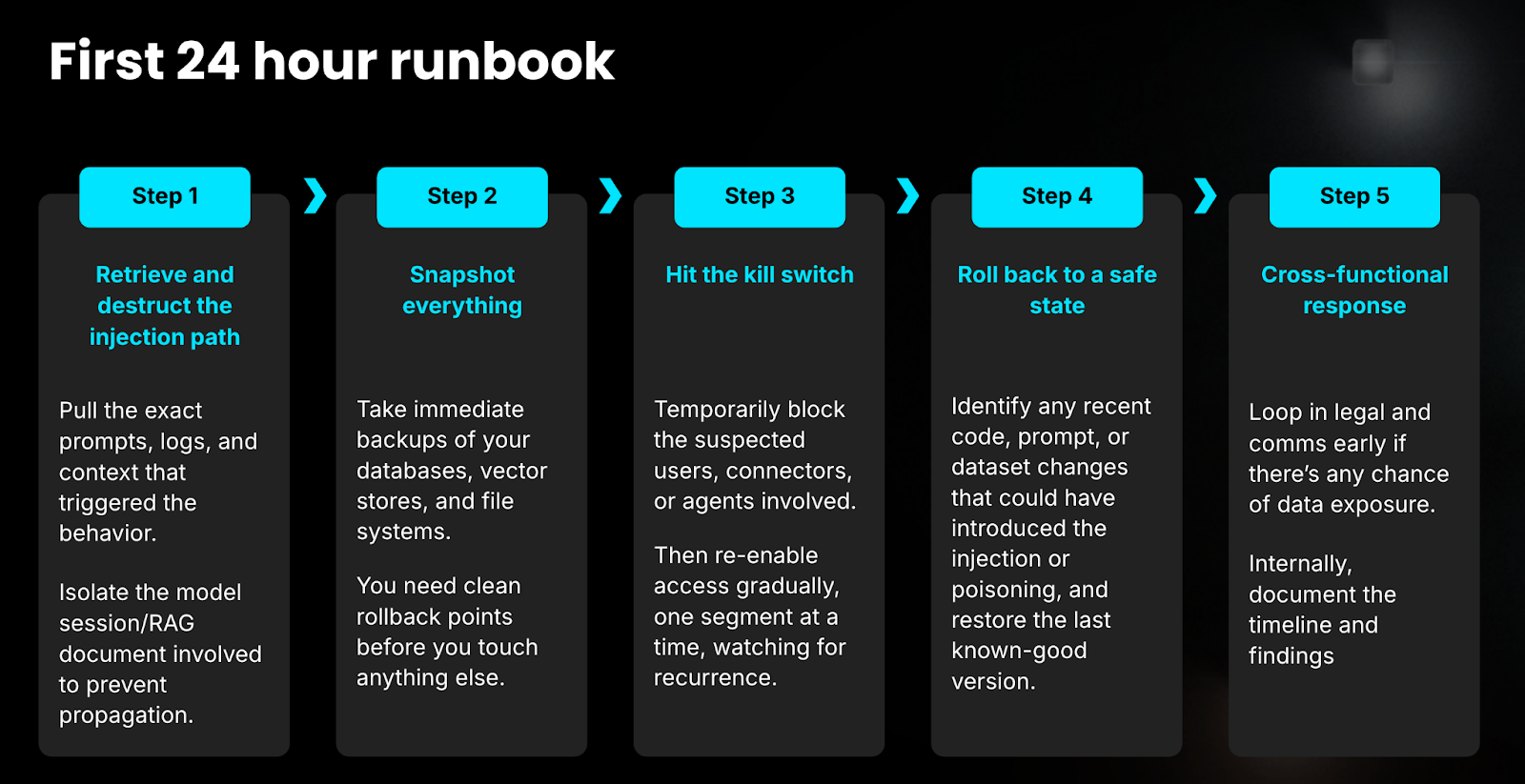
Here’s a playbook to tackle Prompt Injection attacks
Harness’s Vision for AI Security
Harness's approach to closing the AI security gap is built on three pillars:
- AI Asset Discovery and Posture Management: This involves automatically discovering all AI assets (APIs, LLMs, MCP tools, etc.) by analyzing application traffic. This capability eliminates the "blind spot" that application security teams often have with "shadow AI," where developers do not document new AI assets. The platform automatically provides sensitive data flows and governance policies, helping you be audit-ready, especially if you operate in a regulated industry.
- AI Security Testing: This helps organizations test their applications against AI-specific attacks before they are shipped to production. Harness's product supports DAST scans for the OWASP LLM Top 10, which can be executed as part of a CI/CD pipeline.
- AI Runtime Protection: This focuses on detecting and blocking AI threats such as prompt injection, jailbreak attempts, data exfiltration, and policy violations in real time. It gives security teams immediate visibility and enforcement without impacting application performance or developer velocity.
Read more about Harness AI security in our blog post.
Looking Ahead: The Evolving Attack Landscape
Looking six to 12 months ahead, the biggest risks come from autonomous agents, deeper tool chaining, and multimodal orchestration. The game has changed from focusing on "AI code-based risk versus decision risk."
Security teams must focus on upgrading their security and testing capabilities to understand the decision risk, specifically "what kind of data is flowing out of the system and what kind of things are getting exposed." The key is to manage the non-deterministic nature of AI applications.
To stay ahead, a phased maturity roadmap is recommended:
- Start with visibility.
- Move to testing.
- Then, focus on runtime protection.
By focusing on automation, prioritizing the most critical threats, and adopting a platform that provides visibility, testing, and protection, organizations can manage the risks introduced by AI velocity and build resilient AI-native applications.
Learn more about tackling the AI velocity paradox in security in this webinar.


Protect Against Critical Unauthenticated RCE in React & Next.js (CVE-2025-55182) with Traceable WAF
Protect Against Critical Unauthenticated RCE in React & Next.js (CVE-2025-55182) with Traceable WAF
The cybersecurity landscape was rocked on December 3rd, 2025, by the disclosure of another critical remote code execution (RCE) vulnerability affecting React Server Components and Next.js applications. With CVSS scores of 10.0, the maximum severity rating, CVE-2025-55182 (React) and the related CVE-2025-66478 (Next.js, later marked as a duplicate) represent an immediate, severe threat to modern web applications. At Harness, we have comprehensive protections in Traceable WAF that were already shielding your applications from these vulnerabilities, even before the CVEs were created.
Understanding the Threat
These vulnerabilities, discovered by security researcher Lachlan Davidson, strike at the heart of React's new server-side rendering architecture. The flaws exist in the React Server Components (RSC) "Flight" protocol, which handles data serialization and deserialization between the server and client. What makes these vulnerabilities particularly dangerous is their combination of the following critical characteristics:
- Unauthenticated exploitation: No credentials or authentication required
- Remote code execution: Full server compromise possible
- Default configurations are vulnerable: Standard deployments are immediately at risk
- Near-100% exploitation reliability: Attacks have shown consistent success rates
- Broad ecosystem impact: Affects React 19, Next.js, and numerous dependent frameworks
The vulnerability stems from insecure deserialization in the RSC protocol's handling of incoming payloads. When a server receives a specially crafted, malformed payload, it fails to validate the structure correctly, allowing attacker-controlled data to influence server-side execution logic and execute arbitrary JavaScript code.
Affected Versions
React Server Components:
- Vulnerable Versions: 19.0, 19.1.0, 19.1.1, and 19.2.0
- Affected packages: react-server-dom-parcel, react-server-dom-webpack, react-server-dom-turbopack
- Fixed versions: 19.0.1, 19.1.2, 19.2.1
Next.js (App Router):
- Vulnerable Versions: 15.x, 16.x, and 14.3.0-canary.77+
- Fixed versions: 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7
Other affected frameworks:
- React Router
- Waku
- RedwoodJS (rwsdk)
- Parcel (@parcel/rsc)
- Vite RSC Plugin (@vitejs/plugin-rsc)
Immediate Protection with Traceable WAF's Multi-Layered Defense
Protection by Default - Already Active Before Disclosure
The most important news: If you had Traceable WAF enabled, you were already protected against well-known exploits at this moment. Our advanced payload analysis engine was already defending against this vulnerability class through multiple existing rules that included:
- Server Side Template Injection (SSTI) Attempt: Blocks injection patterns, including those used in RSC deserialization attacks
- Node.js Injection Attack: Prevents code injection attempts targeting the Node.js runtime
This proactive protection demonstrates the value of comprehensive security rules that defend against entire vulnerability classes rather than just specific CVEs.
Dedicated CVE-Specific Analysis
Following the disclosure, our security research team identified multiple possible exploitation techniques and developed additional specific detection signatures. The following signatures protect against the payload patterns characteristic of CVE-2025-55182 exploitation attempts across different components:
- React & Next.js Server Functions Deserialization RCE: (CVE-2025-55182)
- ReactJS Server Functions Deserialization RCE: (CVE-2025-55182)
Ensure these two rules are set with the action Block
.png)
AI-Powered Anomaly Detection
Beyond signature-based detection, Traceable's behavioral analysis identifies attempts to bypass detection or discover new attack vectors. Our anomaly detection engine monitors for:
- Unexpected or unknown parameters: Identifying parameters not seen in normal traffic
- Unseen parameter contents: Detecting unusual values in known parameters
- Unusual request sizes: Flagging requests that deviate from typical patterns
- Abnormal execution paths: Recognizing when requests trigger unexpected behavior
Testing Your Applications for Vulnerability
ASPEN Labs CVE-2025-55182 Checker
Our security researchers at ASPEN Labs by Harness have developed an open-source tool to help organizations test whether their applications are vulnerable to CVE-2025-55182. This tool provides a safe, controlled way to verify if your React and Next.js applications are vulnerable.
Tool Repository: Github(https://github.com/aspen-labs/CVE-2025-55182-checker)
Quick Testing Guide
- Clone the checker tool:
git clone https://github.com/aspen-labs/CVE-2025-55182-checker.git
cd CVE-2025-55182-checker- Run the vulnerability check:
# Install uv
curl -LsSf https://astral.sh/uv/install.sh | sh
# Test a specific endpoint
uv run check https://your-app.com
# Test multiple endpoints from a file
uv run check --file targets.txt.example -o vulnerable.txt
The Harness Advantage is Research-Driven Security
At Harness, our unique approach to security, where researchers function as both researchers and developers, enables rapid development of defences and response to vulnerabilities. Our security research team doesn't just analyze these vulnerabilities; they immediately evaluate and translate their findings into practical protections deployed across our WAF infrastructure.
This research-to-product pipeline means:
- Faster protection deployment: Hours, not days, from disclosure to protection
- Higher efficacy rates: Researchers who understand the vulnerability build the defense
- Continuous improvement: Real-world data feeds back into research
- Proactive defense: Identifying vulnerability classes before they're exploited
Continuous Protection is Necessary
The disclosure of CVE-2025-55182 serves as a stark reminder of the evolving threat landscape facing modern web applications. As frameworks become more sophisticated, so do the attack vectors targeting them. Traceable by Harness WAF represents not just a response to today's threats, but a platform built for tomorrow's challenges.
Our commitment to our customers includes:
- 24/7 threat monitoring: Continuous surveillance for emerging threats
- Rapid rule deployment: Protection updates within hours of disclosure
- Research-driven innovation: Leveraging cutting-edge security research
- Community collaboration: Sharing threat intelligence for collective defense
Take Action Now
The critical nature of these vulnerabilities demands immediate action. Organizations running React Server Components or Next.js applications should:
- Enable Traceable WAF protection immediately if not already active
- Review protection logs for any exploitation attempts
- Plan patching schedule for affected applications
- Contact our security team for customized protection strategies
Be Ready for the Next Vulnerability
CVE-2025-55182 represents one of the most severe vulnerability disclosures in recent memory for the JavaScript ecosystem. With their combination of ease of exploitation, widespread impact, and critical severity, these vulnerabilities pose an immediate threat to organizations worldwide.
Traceable by Harness WAF provides comprehensive, immediate protection against these vulnerabilities through multiple layers of defense, from signature-based detection to AI-powered behavioral analysis. While patching remains essential for long-term security, our WAF ensures your applications remain protected during this critical period.
At Harness, we understand that security is not just about responding to threats; it's about staying ahead of them. Our research-driven approach, combined with our advanced WAF capabilities, ensures that your applications remain secure not only against today's disclosed vulnerabilities but also against tomorrow's emerging threats.
Stay protected. Stay ahead. Choose Traceable by Harness WAF.
For more information about Traceable WAF protection against CVE-2025-55182, or guidance, contact our team at security@harness.io


Explore Traceable Cloud WAAP for modern application security
Introducing Traceable Cloud WAAP: Built for the Way Applications Work Today
Today marks a major milestone in our journey to deliver the industry’s first unified DevSecOps platform—one that empowers engineering and security teams to collaborate seamlessly and deliver software quickly and securely. Following the merger of Harness and Traceable, we’re proud to unveil our first major innovation as a combined company: Traceable Cloud Web Application and API Protection (WAAP). This solution is purpose-built to secure modern, cloud-native applications and APIs—wherever and however they run.
The merger of Harness and Traceable was driven by a shared vision: to unify security and software delivery within a seamless, AI-powered platform. Traceable Cloud WAAP is a powerful example of our unified vision in action. It delivers deep, context-aware protection for web applications and APIs—helping you detect threats earlier, respond faster, and enforce consistent, intelligent defenses across your entire stack.
In a world where software changes rapidly and threats evolve just as fast, siloed tools are no longer enough. Together, we are setting a new standard for how teams seamlessly develop, deliver and secure applications, enabling them to embed security at every stage of the software lifecycle—without slowing development.
Why Traditional WAAP Falls Short in a Cloud-Native World
Today’s applications are cloud-native, highly distributed, and powered by APIs that form the backbone of digital interaction. But while apps have evolved, many security solutions haven’t. APIs now account for over 70% of internet traffic, yet traditional WAAP products still focus on perimeter defenses—leaving the core of modern architectures vulnerable.
Attackers have adapted, exploiting APIs, abusing business logic, and evading static defenses. Legacy WAAP solutions were designed for a simpler time—when applications lived behind a static edge, and traffic was easier to inspect and control. But cloud-native applications are anything but static. They scale across multiple environments, communicate through ephemeral APIs, and change frequently as development teams release new features at high velocity.
Traditional WAAPs can’t keep up. They miss shadow APIs, overlook internal traffic, and struggle to detect business logic abuse or human-like bots. They also rely heavily on manual rule tuning and separate runtime protection from development workflows, creating unnecessary friction between security and engineering teams.
As a result, organizations are left with blind spots that attackers are quick to exploit. In today’s API-driven world, reactive, perimeter-based security is no longer enough.
True Defense-in-Depth Starts with Deep Context
Traceable Cloud WAAP unifies four critical security capabilities in a single, integrated solution:
- Web application protection
- API security
- Bot mitigation
- DDoS defense
But where it truly stands apart is in the depth of its context and intelligence.
Rather than depending solely on static signatures, Cloud WAAP analyzes behavior across users, APIs, and sessions in real-time. It understands how traffic is expected to behave—and intervenes when something deviates from the norm. This enables security teams to detect threats earlier, respond faster, and make decisions with greater confidence.
As environments grow more complex, a unified approach backed by deep context ensures consistent protection across your entire application ecosystem.
How Traceable Solves What Others Miss
Built specifically for cloud-native environments, Traceable Cloud WAAP represents a strategic evolution in application protection for today’s API-first world. It delivers the deep visibility and operational agility that traditional WAAPs lack, ensuring modern applications remain secure as they scale, shift, and grow more complex.
Key capabilities include:
- Comprehensive API discovery from traffic, encrypted flows, and code repositories
- Sensitive data flow mapping and customizable API risk scoring
- Real-time runtime protection with attacker fingerprinting, user/session attribution, and anomaly detection
- Shift-left API testing integrated into your CI/CD pipelines to catch vulnerabilities before production

Real-Time Insights, Actionable Defense - Traceable Cloud WAAP provides deep, real-time visibility into application and API traffic. Instantly identify and respond to OWASP Top 10 threats, blocked attacks, and the most targeted services—all from a single, context-rich dashboard designed for modern, cloud-native environments.
Traceable is also designed for maximum deployment flexibility—integrating seamlessly with your environment, no matter how it’s built:
- Out-of-Band: Mirror traffic from gateways or load balancers, or use eBPF for deep, passive visibility without requiring code changes
- Inline Agents: Deploy directly in API gateways (e.g., Kong), load balancers (e.g., NGINX), or inside application code using lightweight language agents
- Edge Deployment: Route traffic securely to our POP’s via DNS or deploy Traceable behind a CDN for fully managed, agentless protection
This combination of deep visibility, intelligent runtime protection, and flexible deployment empowers security teams to close visibility gaps, detect threats earlier, and enforce protection wherever modern applications and APIs live.
Secure What Matters, Wherever It Runs
Speed and security shouldn’t be at odds. Traceable Cloud WAAP eliminates bottlenecks, enabling fast, uninterrupted development—while keeping protection always on.
Whether you’re securing API-driven microservices or hybrid environments across cloud and on-prem, Traceable protects what matters most: your data, your users, and your APIs.
In a world where applications constantly evolve, security must too. Traceable delivers the visibility, context, and adaptability needed to protect modern, dynamic environments from the inside out.
This launch is the first major innovation since Harness and Traceable joined forces—and it reflects our shared vision for a unified, AI-powered DevSecOps platform. Together, we help teams move faster, stay aligned, and defend what matters most.
From bot attacks and API abuse to DDoS threats, Traceable ensures your defenses scale with your apps—without slowing innovation.
Schedule a demo to see how Traceable protects your APIs, apps, and users in real-time.
.svg)