
The Argo ceiling is a predictable scaling challenge, not a failure of Argo CD or GitOps. As clusters and teams grow, visibility, governance, and orchestration fragment without a control plane. Script-heavy workflows and manual processes slow delivery and increase risk at scale. A GitOps control plane enables unified visibility, structured workflows, automated guardrails, and secure secret management.
GitOps has become the default model for deploying applications on Kubernetes. Tools like Argo CD have made it simple to declaratively define desired state, sync it to clusters, and gain confidence that what’s running matches what’s in Git.
And for a while, it works exceptionally well.
Most teams that adopt GitOps experience a familiar pattern: a successful pilot, strong early momentum, and growing trust in automated delivery. But as adoption spreads across more teams, environments, and clusters, cracks begin to form. Troubleshooting slows down. Governance becomes inconsistent. Delivery workflows sprawl across scripts and tools.
This is the point many teams describe as “Argo not scaling.”
In reality, they’ve hit what we call the Argo ceiling.
The Argo ceiling isn’t a flaw in Argo CD. It’s a predictable inflection point that appears when GitOps is asked to operate at scale without a control plane.
What Is the Argo Ceiling?
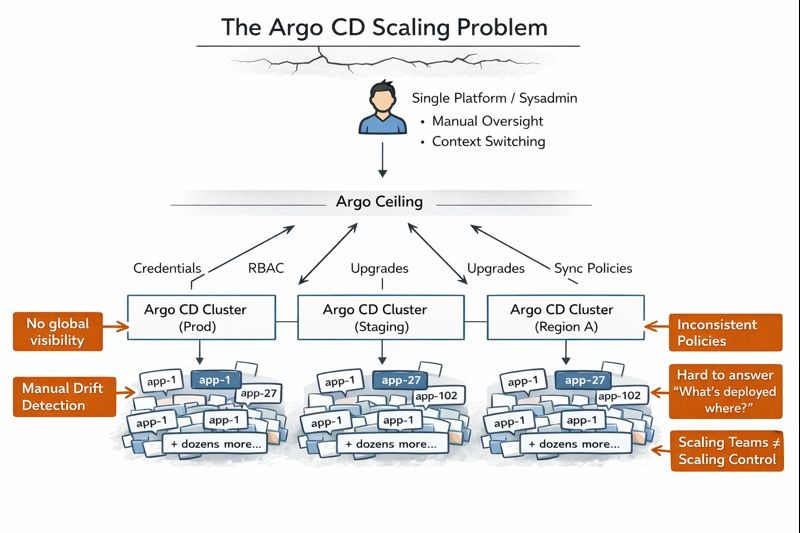
The Argo ceiling is the moment when GitOps delivery starts to lose cohesion as scale increases.
Argo CD is intentionally designed to be cluster-scoped. That design choice is one of its strengths: it keeps the system simple, reliable, and aligned with Kubernetes’ model. But as organizations grow, that same design introduces friction.
Teams move from:
- A small number of clusters to dozens (or hundreds)
- A handful of applications to thousands
- One platform team to many autonomous product teams
At that point, GitOps still works — but operating GitOps becomes harder. Visibility fragments. Orchestration logic leaks into scripts. Governance depends on human process instead of platform guarantees.
The Argo ceiling isn’t a hard limit. It’s the point where teams realize they need more structure around GitOps to keep moving forward.
The Symptoms Teams See at Scale
Fragmented Visibility
One of the first pain points teams encounter is visibility.
Argo CD provides excellent insight within a single cluster. But as environments multiply, troubleshooting often turns into dashboard hopping. Engineers find themselves logging into multiple Argo CD instances just to answer basic questions:
- Where is this application deployed?
- Which environment failed?
- Was this caused by the same change?
What teams usually want instead is:
- A single place to see deployment status across clusters
- The ability to correlate failures back to a specific change or release
- Faster root-cause analysis without switching contexts
Argo CD doesn’t try to be a global control plane, so this gap is expected. When teams start asking for cross-cluster visibility, it’s often the first sign they’ve hit the Argo ceiling.
Glue Code and Script Entropy
As GitOps adoption grows, orchestration gaps start to appear. Teams need to handle promotions, validations, approvals, notifications, and integrations with external systems.
In practice, many organizations fill these gaps with:
- Jenkins pipelines
- GitHub Actions
- Custom scripts glued together over time
These scripts usually start small and helpful. But as they grow, they begin to:
- Accumulate environment-specific logic
- Encode tribal knowledge
- Become difficult to change safely
This is a classic Argo ceiling symptom. Orchestration lives outside the platform instead of being modeled as a first-class, observable workflow. Over time, GitOps starts to feel less like a modern delivery model and more like scripted CI/CD from a decade ago.
Awkward Promotion Flows
Promotion is another area where teams feel friction.
Argo CD is excellent at syncing desired state, but it doesn’t model the full lifecycle of a release. As a result, promotions often involve:
- Manual pull requests
- Repo hopping between environments
- Ad-hoc approvals and checks
These steps slow delivery and increase cognitive load, especially as the number of applications and environments grows.
Secret Sprawl
Git is the source of truth in GitOps — but secrets don’t belong in Git.
At small scale, teams manage this tension with conventions and external secret stores. At larger scale, this often turns into a patchwork of approaches:
- Different secret managers per team
- Custom templating logic
- Inconsistent access controls
The result is secret sprawl and operational risk. Managing secrets becomes harder precisely when consistency matters most.
Difficult Audits
Finally, audits become painful.
Change records are scattered across Git repos, CI systems, approval tools, and human processes. Reconstructing who changed what, when, and why turns into a forensic exercise.
At this stage, compliance depends more on institutional memory than on reliable system guarantees.
What Not to Do When You Hit the Ceiling
When teams hit the Argo ceiling, the instinctive response is often to add more tooling:
- More scripts
- More pipelines
- More conventions
- More manual reviews
Unfortunately, this usually makes things worse.
The problem isn’t a lack of tools. It’s a lack of structure. Scaling GitOps requires rethinking how visibility, orchestration, and governance are handled — not piling on more glue code.
Principles for Scaling GitOps Correctly
Before introducing solutions, it’s worth stepping back and defining the principles that make GitOps sustainable at scale.
Centralize Control (Without Centralizing Ownership)
One of the biggest mistakes teams make is repeating the same logic in every Argo CD cluster.
Instead, control should be centralized:
- RBAC policies
- Governance rules
- Audit trails
- Global visibility
At the same time, application ownership remains decentralized. Teams still own their services and repositories — but the rules of the road are consistent everywhere.
Orchestrate, Don’t Script
GitOps should feel modern, not like scripted CI/CD.
Delivery is more than “sync succeeded.” Real workflows include:
- Pre- and post-deployment steps
- Validations and checks
- Approvals and notifications
These should be modeled as structured, observable workflows — not hidden inside scripts that only a few people understand.
Automate Guardrails
Many teams start enforcing rules through:
- PR reviews
- Documentation
- Manual approvals
That approach doesn’t scale.
In mature GitOps environments, guardrails are enforced automatically:
- Objective policy checks
- Repeatable enforcement
- Rules that run before, during, and after deployment
Git remains the source of truth, but compliance becomes a platform guarantee instead of a human responsibility.
Why GitOps Needs a Control Plane
These challenges point to a common conclusion: GitOps at scale needs a control plane.
Git excels at versioning desired state, but it doesn’t provide:
- Cross-cluster visibility
- Consistent governance
- End-to-end workflow orchestration
A control plane complements GitOps by sitting above individual clusters. It doesn’t replace Argo CD — it coordinates and governs it.
Harness as the GitOps Control Plane
Harness provides a control plane that allows teams to scale GitOps without losing control.
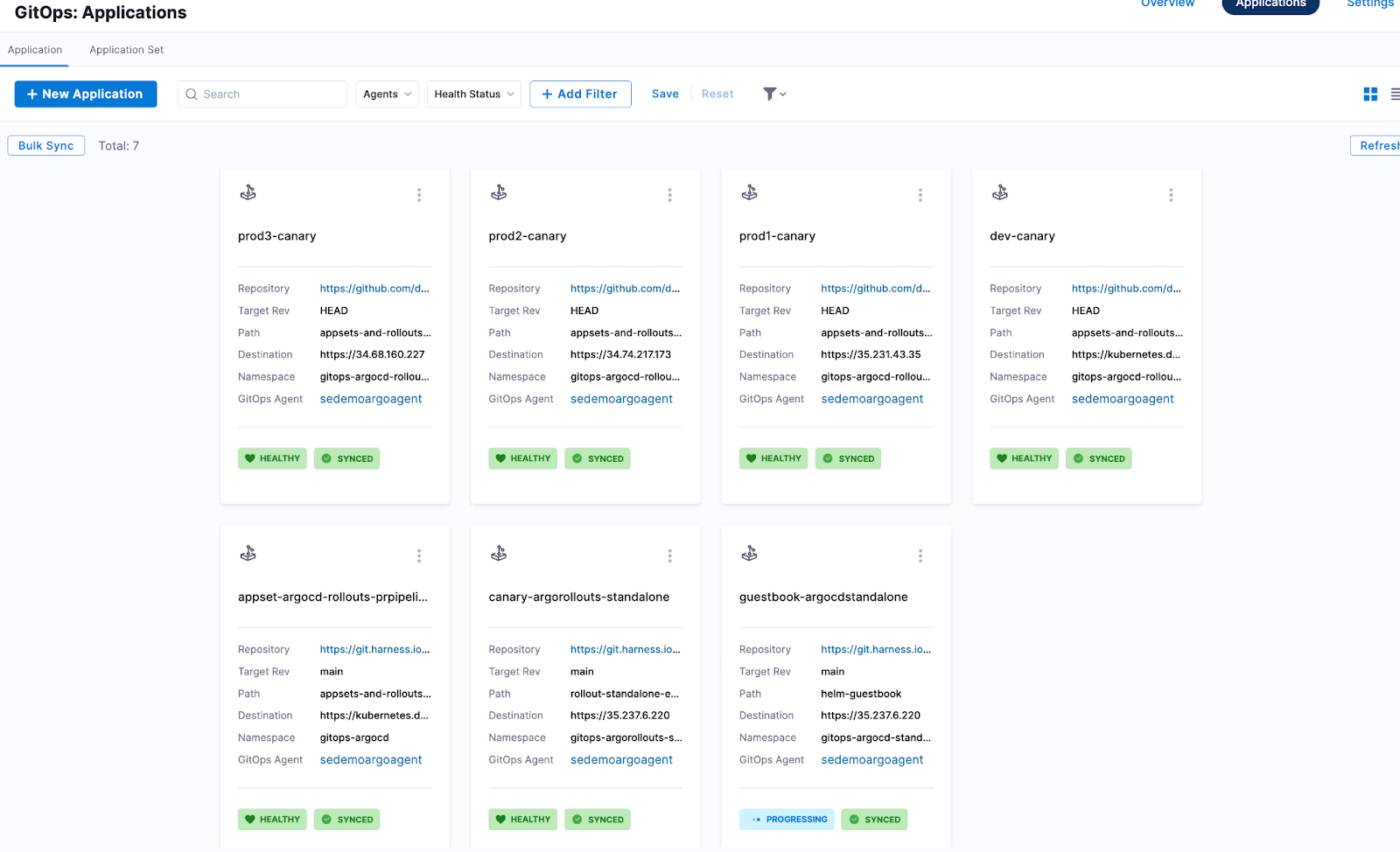
Unified Visibility
Harness gives teams a single place to see deployments across clusters and environments. Failures can be correlated back to the same change or release, dramatically reducing time to root cause.
Structured Orchestration
Instead of relying on scripts, Harness models delivery as structured workflows:
- Pre- and post-sync steps
- Promotions and approvals
- Notifications and integrations
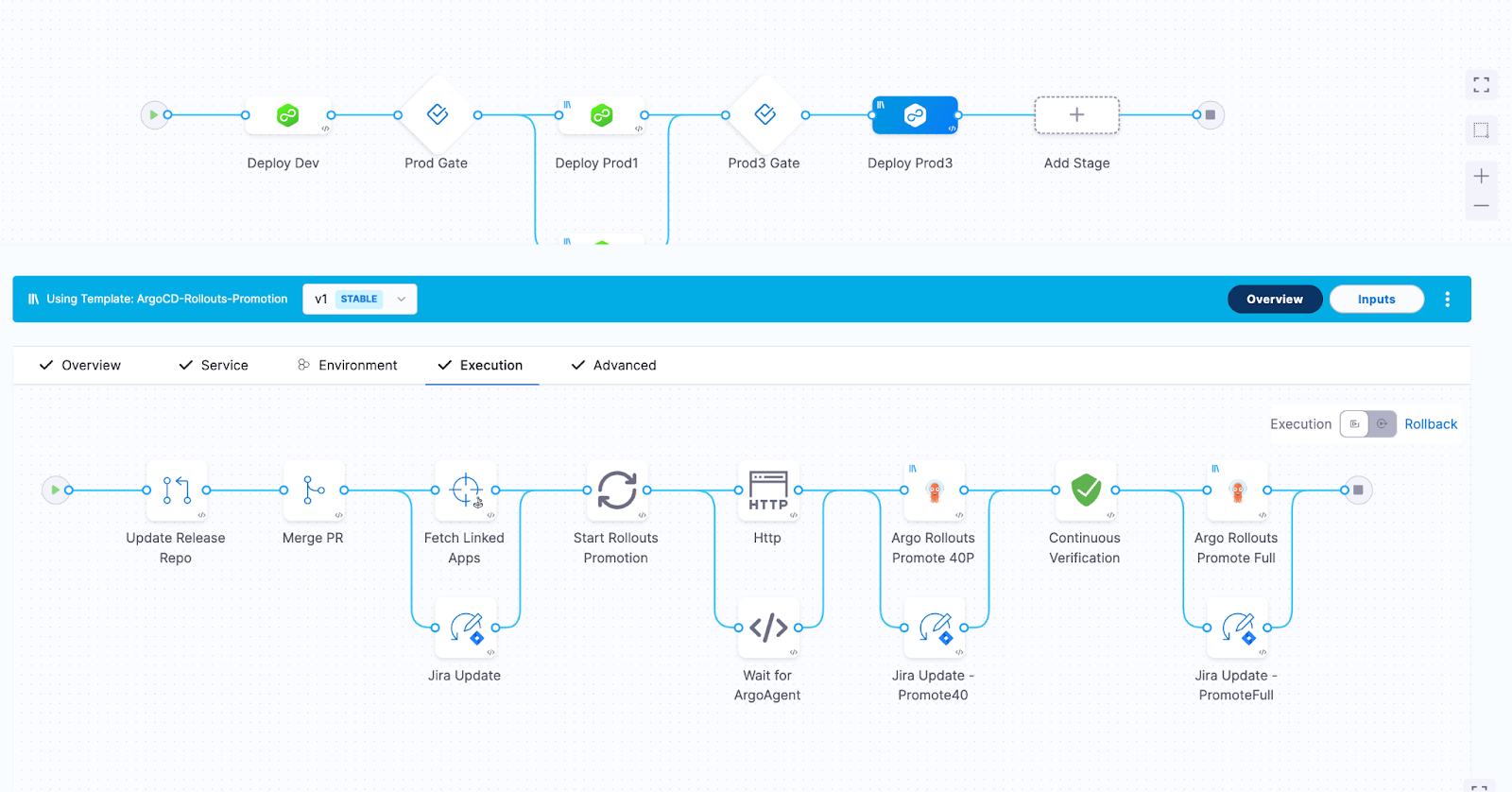
This keeps orchestration visible, reusable, and safe to evolve over time.
AI-Assisted Deployment Verification
Kubernetes and Argo CD can tell you whether a deployment technically succeeded — but not whether the application is actually behaving correctly.
Harness customers use AI-assisted deployment verification to analyze metrics, logs, and signals automatically. Rather than relying on static thresholds or manual checks, the system evaluates real behavior and can trigger rollbacks when anomalies are detected.
This builds on ideas from progressive delivery (such as Argo Rollouts analysis) while making verification consistent and governable across teams and environments.
Solving the GitOps–Secrets Paradox
Harness GitOps Secret Expressions address the tension between GitOps and secret management:
- Secrets are created and stored securely in the Harness platform
- GitOps manifests reference secrets using expressions
- The GitOps agent resolves them at runtime
- Secrets never leave customer infrastructure
This keeps Git clean while making secret handling consistent and auditable.
What’s Next
The Argo ceiling isn’t a failure of GitOps — it’s a sign of success.
Teams hit it when GitOps adoption grows faster than the systems around it. Argo CD remains a powerful foundation, but at scale it needs a control plane to provide visibility, orchestration, and governance.
GitOps doesn’t break at scale.
Unmanaged GitOps does.
Ready to move past the Argo ceiling? Watch the on-demand session to learn how teams scale GitOps with confidence.

